New strong ransomware emerged - CryptXXX
Overview
Ransomware became a prevalent cyber threat since February 2016. According to the statistics of HKCERT, there were 172 ransomware incident reports up to end of May 2016.
Following the prevalence of the Locky ransomware in March 2016, other ransomware became more active. While Locky is gradually losing momentum, another ransomware CryptXXX moved up to the top of list of ransomware incident reports, with 32 cases reported in May. CryptXXX emerged very fast. The latest version 3.1 of CryptXXX has enhancements to evade detection and includes encryption of network shares.
CryptXXX spread via compromised website
CryptXXX is very different from Locky in propagation. It does not rely on spam email at all. CryptXXX spreads via compromised websites and banner advertisement that host the Angler exploit kits. Among the 32 incident reports of CryptXXX in May, one case is hosting of the exploit kit for ransomware infection. The website has unpatched security vulnerability and was utilized by cyber criminals to serve the attack.
Here is another example of such kind of propagation. In April 2016, a popular American toy company Maisto, was caught to distribute the Angler exploit kit eventually result in ransomware infection. According to a web security company Sucuri, Maisto website is running an outdated version of Joomla content management system, therefore exposing itself to the cyber criminals. Malicious code was injected to the homepage to attack security vulnerabilities of the visitors' operating system, browser and plugins such as Adobe Flash or Microsoft Silverlight. Once successful, CryptXXX ransomware is installed on the computer.
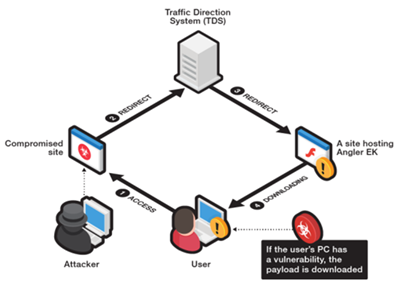
Figure 1. CryptXXX infection vector via Angler EK (Source: trendmircro.com)
CryptXXX good at detection evasion
CryptXXX introduced several enhancements to evade detection.
1. Skip deleting volume shadow copy
2. Use dynamic link library (dll) injection to hide inside signed windows processes
3. Delay execution for longer than an hour to evade detection by most traditional sandboxes which are capable of executing for just a few minutes.
4. Minimize the network activity with the ransomware control server to avoid blocking of encryption key exchange operation.
The Ransomware-as-a-Service
Ransomware is not just a malware. It is part of the Cybercrime-as-a-service. Some cyber criminals provide the malware, exploit kit, malware distribution channel, Bitcoin ransom payment services, and management panel as a service to other criminals who do not possess the skill and infrastructure. They sold CryptXXX and other ransomware underground circles for a good price.
The lucrative returns of ransomware will lure more cyber criminal groups to enter the arena. Criminals behind ransomware keep on refining the malware and the service model. More ransomware that are more difficult to trace will continue to emerge, which might extend to include targets of Mac and Linux operating systems and mobile devices.
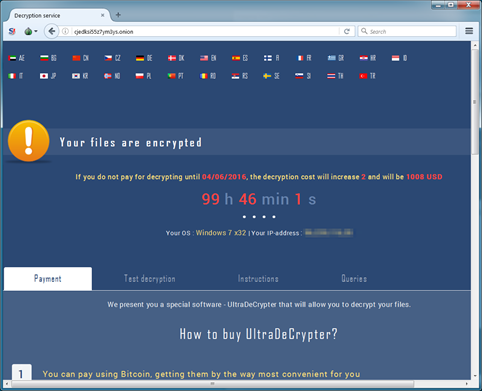
Figure 2. Increase the ransom amount if victim delays payment (Source: proofpoint.com)
Tackling the Threat of Ransomware
Users are advised to take steps to protect from ransomware threats:
• Regularly backup the files stored on your computer, and keep an offline copy of the backup
• Minimize the risk of infection through visiting website by applying updated security patch on OS, software and browser plugins, and uninstall any software that are no longer needed.
• Stop using any end of support software (e.g. Windows XP) since there is no security patch released for them.
• Always keep your security software up to date. • Do not open any suspicious email and attachment. Delete them right away.
• Turn off the marco feature of Microsoft office, and only re-enable it temporarily when necessary and under secure condition
• For IT administrator, users should be restricted in minimum access privilege in order to reduce the destructive effect from ransomware.
Conclusion
The evolution of ransomware with advanced evasion techniques gives it an advantage over most security systems to maintain a low detection rate of new sample. We should deploy the multi-layer defense approach to tackle ransomware attack. We should refuse to pay ransom because it is funding cyber criminals and encourages them to propagate more ransomware.
References
1. /my_url/en/alert/16060301
2. http://blog.trendmicro.com/trendlabs-security-intelligence/will-cryptxxx-replace-teslacrypt-ransomware-shakedown/
3. http://blog.checkpoint.com/2016/05/27/cryptxxx-simple-evasive-effective/
4. https://blog.malwarebytes.org/threat-analysis/2016/04/toy-maker-maisto-unwittingly-serves-up-cryptxxx-ransomware/
5. https://www.proofpoint.com/us/threat-insight/post/cryptxxx-ransomware-learns-samba-other-new-tricks-with-version3100
Share with
