Ramnit Botnet Detection and Cleanup in Hong Kong

HKCERT estimated that about 150 computers in Hong Kong were infected by Ramnit botnet. To avoid your computers become the hacker tools, you can detect if you are infected and clean up your computer with the provided steps.
1. HKCERT operation on Ramnit botnet infection
In Feb 2015, Europol's European Cybercrime Centre (EC3) cooperated with a number of national law enforcement and network security companies to launch a joint operation named "Operation Rubly", the goal was to disrupt the criminals behind the Ramnit botnet.
HKCERT received reports from Shadowserver, Microsoft[1] about computers in Hong Kong infected by the Ramnit botnet. About 150 HK IP addresses were reported to have connected to the sinkhole detection system set up by security researcher. These computers may have been infected by the Ramnit malware to become part of Ramnit botnet and made those call home connections. Upon receiving the reports, HKCERT has notified the related ISPs who administrated those IP addresses to alert their customers about the potential infection.
2. Impact of Ramnit botnet
Ramnit is a module-based malware focus on stealing credential information from banking websites and sensitive data files in infected computer. It uses 2 types (Domain Generation Algorithm (DGA), update via configuration file) of botnet command and control servers to manage different modules and provides software debug and update features. In addition, all data exchanges with the control center server are transmitted in encrypted form, so that the botnet is more stable and difficult to collapse. According to information from Symantec[2], Ramnit has more than 3.2 million infected computers worldwide. India is the most affected country, accounting for about 27%.
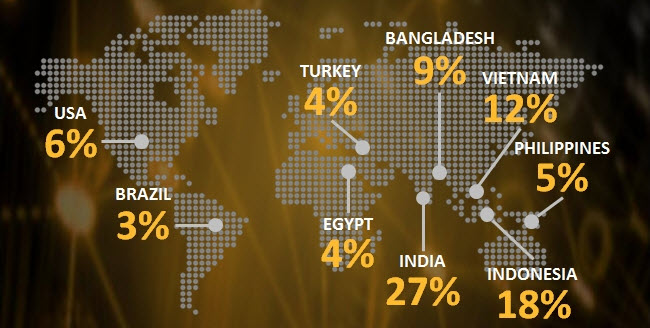
Fig 1: Distribution of infected countries (Image source: Symantec)
Ramnit is a malware targeting Windows operating system which was first discovered in 2010, infected all EXE, DLL, HTM and HTML files on internal hard disk and external disk to quickly self-propagation. After years of improvement, now it can be spread through a various channel, including exploit kits hosted on compromised websites and social media pages, distributed the malware by public FTP servers and bundles with potentially unwanted applications (PUAs) from less reputable sources.
Ramnit is a versatile malware, featuring six standard modules and using various channels to cause serious impact on the infected computer.
- Spy module – Detects web browsing activity, when the victim visits certain web pages, such as online banking sites. It can inject customized data input field in original website content, such as credit card expiry dates, making it appear the bank is asking the victim for additional credentials. This stolen data can be used to facilitate fraud.
- Cookie grabber module - Steals session cookies from web browsers and send them back to the criminals, who can impersonate the victim by using the cookies to pass website authentication. This could allow them to hijack online banking sessions.
- Drive scan module – Steals the sensitive data via scanning computer’s hard drive to search the file contains specific keywords such as passwords.
- FTP module - Gathers the login credentials of FTP client applications and set up an anonymous FTP server in computer to distribute Ramnit malware.
- Virtual network computing (VNC) module: Provides remote access to the computer.
- Anti-AV module – Disables the security protection features in Microsoft Windows and a blacklist of more than 300 types of antivirus applications.
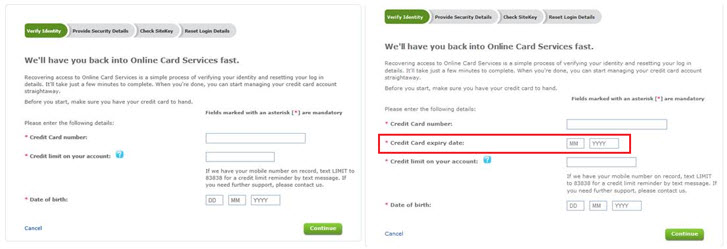
Fig 2: Website is injected by customized data input field (Image source: Microsoft)
In addition to these features, Ramnit has a hot pluggable modular framework design that gives a flexibility to extend new features on demand.
3. How to detect and remove Ramnit malware
If you suspect that your computer was infected by Ramnit malware, please follow the steps to perform a full system scan.
Note: Due to the victim’s banking credential may have been compromised, HKCERT suggest to change the password immediately after clean up the malware.
4. Reference
You can find below the references noted and other technical details about Ramnit botnet.
- http://blogs.technet.com/b/mmpc/archive/2015/02/25/microsoft-malware-protection-center-assists-in-disrupting-ramnit.aspx
- http://www.symantec.com/connect/blogs/ramnit-cybercrime-group-hit-major-law-enforcement-operation
- http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32-ramnit-analysis.pdf
- https://cdn2.hubspot.net/hubfs/507516/PDF/Ramnit_CaseStudy.pdf
- https://www.europol.europa.eu/content/botnet-taken-down-through-international-law-enforcement-cooperation
Share with
