Beware of WordPress Sites Being Used for Distributed Denial of Service Attack
Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT), which is operated by the Hong Kong Productivity Council, discovered multiple WordPress websites were used for Distributed Denial of Service (DDoS) by attackers.
Recently, HKCERT received reports of DDoS and found attackers make use of the Pingback feature of WordPress to launch DDoS attack. To avoid being a DDoS tool used by attackers, HKCERT recommend web administrators to check the WordPress settings and monitor the network traffic.
Pingback feature abused
Pingback feature is enabled by default in WordPress websites. When there is a link hoping or a site linking to, the website will send a Pingback message automatically to notify the original site the link is quoted. Pingback is implemented as XML-RPC. Attacker sends craft requests to multiple WordPress websites, make use of their Pingback feature to send out Pingback messages to the target website. The attackers usually have a very long list of WordPress websites with Pingback features turned on. The responses of these WordPress websites collectively caused a HTTP distributed flood attack, sending hundreds of request per second to the to the target.
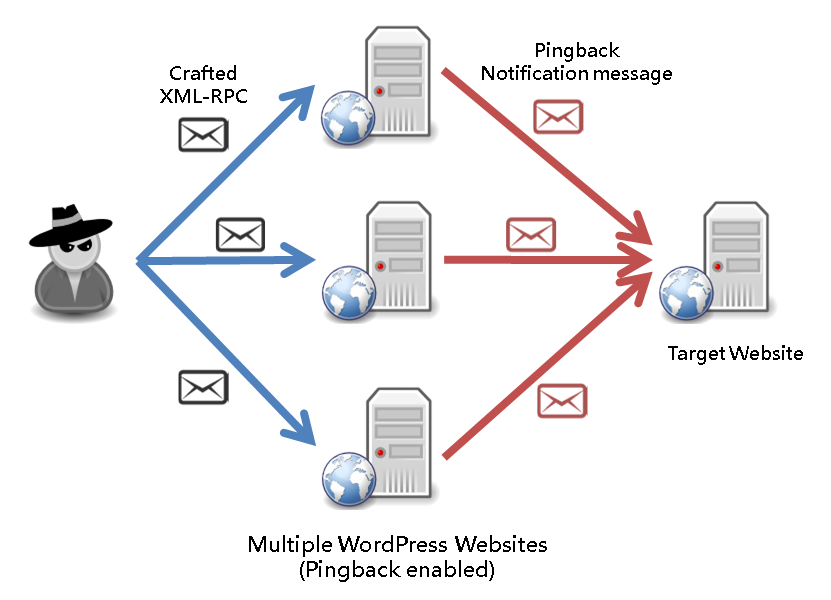
Fig 1) Attack method abusing Pingback feature
Solution
- To prevent your WordPress website from participating in Pingback network attack, HKCERT recommend WordPress website administrators disabling the Pingback feature.
- Web administrators can download the following WordPress Plug-in to stop the Pingback feature of XML-RPC.
Disable XML-RPC Pingback Plug-in
https://wordpress.org/plugins/disable-xml-rpc-pingback/ - For the installation of WordPress Plug-in, please refer to http://codex.wordpress.org/Managing_Plugins
Reference:
Share with
