GameOver Zeus Botnet Detection and Cleanup in Hong Kong

HKCERT estimated that about 2,400 computers in Hong Kong were infected by GameOver Zeus (GOZ) botnet. To avoid your computers become the hacker tools, you can detect if you are infected and clean up your computer with the provided steps.
1. HKCERT operation on GameOver Zeus botnet infection
In Jun 2014, U.S. law enforcement cooperated with a number of national law enforcement and network security companies to launch a joint operation named "Operation Tovar", the goal is to disrupt the criminals behind the GOZ botnet.
HKCERT received reports from Shadowserver1, Symantec2 and US-CERT3 about computers in Hong Kong infected by the GOZ botnet. About 2,400 HK IP addresses were reported to have connected to the sinkhole detection system set up by security researcher. These computers may have been infected by the GOZ malware to become part of GOZ botnet and made those call home connections. Upon receiving the reports, HKCERT has notified the related ISPs who administrated those IP addresses to alert their customers about the potential infection.
2. GameOver Zeus botnet
Zeus is a notorious malware targeted to banking and GOZ (as known as P2P Zeus, ZeuS v3) is a new variant. It changes to adopt Peer-to-Peer (P2P) communication for infrastructure control and also provides Domain Generation Algorithm (DGA) as a fallback communication channel and transmit data in encrypted form, it make the botnet harder to take down. According to information from FBI4, GOZ has more than 1 million infected computers worldwide. The United States is the most affected country, accounting for about 25%.
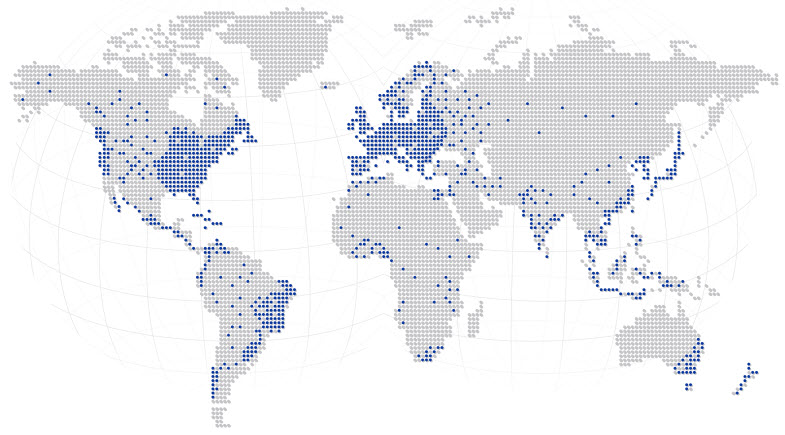
Fig 1: Distribution of infected countries (Image source: FBI)
GOZ is a malware targeting Windows operating system which was first discovered in September, 2011. It spreads via the malware attachment in spam or phishing emails, mainly delivered by the Pushdo botnet.
The major purpose of GOZ is to steal banking credentials from infected computers. It uses man-in-the-browser (MITB) technique to intercept messages of online session. It can bypass two factor authentication and display fraudulent banking security messages in order to obtain user account information for transaction authorization. In addition to stealing data, it also uses the infected computer to send spam emails, conduct network attacks and installs other malicious softwares, such as infamous ransomware "CryptoLocker" to earn money. FBI estimated GOZ botnet has caused a global loss of more than one hundred million U.S. dollars.
3. How to detect and remove GameOver Zeus malware
If you suspect that your computer was infected by GOZ malware, please refer to the following webpage to perform a full system scan:
https://www.hkcert.org/botnet#cleanup
Note: Due to the victim’s banking credential may have been compromised, HKCERT suggest to change the password immediately after clean up the malware.
4. Reference
You can find below the references noted and other technical details about GOZ botnet.
- http://blog.shadowserver.org/2014/06/08/gameover-zeus-cryptolocker
- http://www.us-cert.gov/ncas/alerts/TA14-150A
- http://www.symantec.com/connect/blogs/international-takedown-wounds-gameover-zeus-cybercrime-network
- http://www.fbi.gov/news/stories/2014/june/gameover-zeus-botnet-disrupted
Share with
