Using Joomla? Your website might have already taken part in DDoS attack
1. Background
According to W3Techs [1], Joomla is currently one of the most popular content management systems (CMS) deployed in websites. The market share of Joomla 9.2% until 29 Nov 2013. On the other hand, code execution and SQL injection vulnerabilities are mostly found in Joomla [2], which implied that attackers can easily compromise outdated vulnerable Joomla to perform malicious activities. The purpose of this article is to illustrate a serious DDoS attack by exploiting Joomla vulnerability.
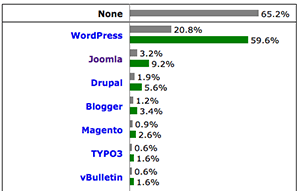
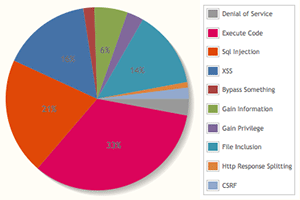
Left: market share of Joomla (source: W3Techs), right: vulnerabilities found in Joomla (source: CVE Details)
2. "Operation Ababil" DDoS attack
In about one year since September 2012 [3], a group called "Izz ad-Din al-Qassam Cyber Fighters" launched a series of DDoS attacks against several U.S. banks. The attacks, namely "Operation Ababil", were triggered by a controversial film trailer mocking the prophet Muhammad in YouTube [4].
Several security vendors reported that the DDoS attacks generated maximum traffic from 60 Gbps to 100 Gbps [5]. As a reference, in the past year, the overall internet traffic in Hong Kong through HKIX is around 150 Gbps on average [6].
To launch such powerful DDoS attack, the attackers made use of a server based botnet called "itsoknoproblembro", which is quite different from some infamous botnet such as Citadel or Pushdo using compromised PC as bot. The attackers will first find web servers with vulnerable PHP based CMS, then inject the "itsoknoproblembro" toolkit into the servers. The compromised server is called "brobot". Since the toolkit is developed in PHP, the attacker can control the infected servers through usual HTTP request, i.e. URL with parameters, to launch DDoS attack [7].
3. HKCERT operation on "brobot" cleanup in Hong Kong
Since October 2012, HKCERT have received reports from US-CERT, APCERT and some U.S. bank about compromised websites hosted in Hong Kong participating in the DDoS attack. Until the time the article is published, we have notified 34 ISP to contact their customers to clean up 293 URL, which come from 144 websites hosted on 129 IP addresses in Hong Kong.
4. How to detect and remove "brobot" in CMS
The compromised websites in Hong Kong mainly used outdated and vulnerable Joomla as CMS, and were injected with "itsoknoproblembro" toolkit. Since the botnet is developed and controlled with PHP, other PHP based CMS such as Wordpress can also be compromised to become "brobot" [7].
4.1 How to detect "brobot" in CMS
- A malicious user "alexaalexa" may have registered in your CMS with email address "[email protected]".
- Regardless of the CMS used, detect brobot by checking any of the following files found in your web server (note the intentional misspelling of the file name):
classfile2.php confgic.php confiq.php define.inc.php erorlog.php error.php get.pl haeadr.php hlep.php imge.php indx.php inedx.hph infophp.php kickstart.php loguout.php mgsbox.php post.pl pr.txt rp.php saerch.php service.php settinq.php seurch.php startphp.php stcp.php stcurl.php stlye.php stmdu.php stph.php style.php themess.php
4.2 How to remove "brobot" in CMS
For Joomla, follow the instructions in Joomla support forum, and use "Joomla antimalware scanning script" to scan the web server for any malicious files [8]:
- http://extensions.joomla.org/extensions/tools/security-tools/24558
- http://forum.joomla.org/viewtopic.php?f=621&t=777957
The tool is only compatible with Joomla 2.x and 3.x, so you need to upgrade any Joomla 1.x to the latest version before using the tool.
5. Reference
- Usage of content management systems for websites, W3Techs
- Joomla: Vulnerability Statistics, CVE Details
- pp. 5-6, Breaking the Bank - An Analysis of the 2012 – 2013 ‘Operation Ababil’ Financial Industry DDoS Attack Campaign, Arbor Networks
- DDoS attacks against US banks peaked at 60 Gbps, Network World
- Islamic group promises to resume U.S. bank cyberattacks, Network World
- `Yearly' Graph (1 Day Average), HKIX Switching Statistics, HKIX
- THREAT: itsoknoproblembro “BroDoS”, Prolexic
- Server generating DDoS Attacks, The Joomla! Forum
Share with
