Understanding and Tackling Supply Chain Attack
Background
HKCERT named the Supply Chain Attack as one of the five Potential Cyber Security Trends in January 2018 in our annual review and outlook [1].
- Financially Motivated Cyber Crimes continue to proliferate
- Internet of Things (IoT) attacks on the Rise
- Mobile Payment Apps as New Attack Targets
- More Regulation for Security and Privacy
- Supply Chain Attacks bypass Enterprise Defenses
In 2017 we have seen cyber attacks making its way upstream of the supply chain to bypass the defences of enterprises. We have to understand more about it in order to better defend our information assets.
What is Supply Chain Attack?
The term “supply chain” is used to connect the flow of business activities of certain products or services through the participating parties involved. The activities involved are material supply, manufacturing, assembly, distribution (wholesales and retail) to end consumer. Supply chain exists in any industry, from the financial sector, manufacturing industry, software industry to government sector.
The complex interconnection of parties involved in a supply chain can be represented in a simplified flowchart as that in Figure 1.
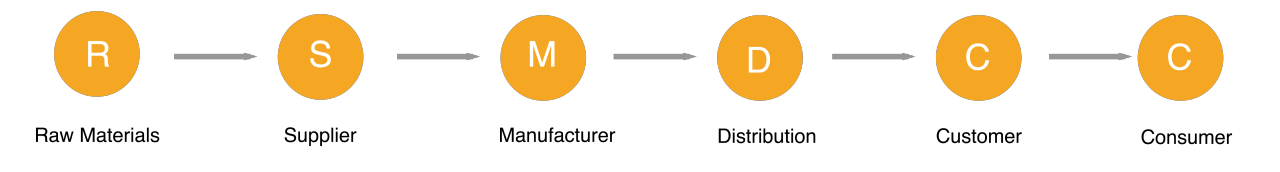
Figure 1
Image source: https://www.wikiwand.com/en/Supply_chain_attack#/citenote30
Supply chain attack is about the attackers leveraging on our trust on our supply chain partners to bypass traditional defenses and compromise a large number of computers. Attackers target weak points in the supply chain to launch their initial attacks. The compromised software spread to other parties downstream. For example, the attacker might target a less secure distributor to spread malware to customers and consumers.
Forms of Supply Chain Attacks
Supply chain attack can take many forms and new forms can emerge by the innovation of the attackers. In this article, we discuss the following common ones with recent attack cases.
- Software Update Contamination
- Software Library Contamination
- Firmware Contamination
- Waterhole Attack
1. Software Update Contamination
Software update contamination of commercial software is the most popular form of supply chain attacks today.
Enterprises has legitimate software installed on the enterprise network after serious testing process. The software providers provide continual update of new features or bug fixes. Software vendors with good security practice will digitally sign the software updates to ensure integrity and send to clients through the software distribution mechanism which is usually highly automated. At the endpoint, client system verifies the authenticity of the software update before applying it.
Enterprise IT teams might whitelist the IP addresses of the update servers provided by the software providers on the firewall. Some enterprise might allow automatic update of software, especially for malware definitions of anti-malware solutions.
There are a few ways that attackers compromise the software update mechanism. Attacker can simply hack into the web servers that is used to distribute software and replace the legitimate software with a poisoned one. However, this might be detectable because the malware were not authenticated by the supplier. Alternatively the attackers can compromise the internal of the software distribution mechanism, the code could have a higher chance to be signed by legitimate digital certificate of the software provider. A signed software update is usually trusted by the systems.
NotPetya ransomware

In June 2017, the “NotPetya” ransomware hit Ukraine and some Eastern European countries. Investigation showed that the initial infection was from the software update of M.E.Doc software, an accounting system having 80% market share in Ukraine. Attacker infiltrated into the software company and created backdoors inside M.E.Doc disguised as legitimate software update.
Besides Ukraine, global shipping company Maersk and FedEx subsidiary TNT were hit by NotPetya, each had financial loss in millions of US dollars.
ShadowPad backdoor

Image credit: https://arstechnica.com/information-technology/2017/08/powerful-backdoor-found-in-software-used-by-100-banks-and-energy-cos
In July 2017, it was found that a backdoor named ShadowPad was injected into the Xmanager Suite, a popular server management software produced by NetSarang. The contaminated software was pushed by software update. The attack was spotted when a company using the software observed suspicious domain name lookup requests. The backdoor allowed the attacker to load malware on the victim systems and exfiltrate data.
CCleaner compromised

CCleaner is a popular free software used for PC maintenance produced by Avast-owned Piriform. In August 2017, it was found that the official download of the free version of CCleaner contained a malicious code and had command and control functionality. It was estimated that 2.3 million copies of poisoned CCleaner software were downloaded. Infected computers would potentially be connected by attacker to steal sensitive personal information. Furthermore the attacker targeted 20+ companies with additional malware.
Chrome browser extensions compromised

Image credit: https://wccftech.com/attackers-chrome-extension-hijacking-spree/
In August 2017 attacker compromised a series of Chrome browser extensions to hijack traffics from legitimate ad network. Attacker used phishing email to obtain the password of chrome extension developers to obtain their Google account credentials.
These compromised extensions attempted to substitute ads on a victim’s browser and hijack traffic from legitimate ad networks. The malicious extensions also attempted to steal CloudFlare credentials from the victim machines.
2. Software Library Contamination
Software Library Contamination is another software supply chain attack. The attack happens through the third-party code that software developers use in their projects.
Most applications contains frameworks, libraries or software development kits (SDK). If these components are compromised, the malicious code will be embedded in applications developed with these components.
The attacker might hack into the hosting website of the framework, library or SDK and replace them with a contaminated version. The developers trusting these components would not be aware that they are using a contaminated third-party code.
XcodeGhost

In 2015, thousands of iOS apps (e.g. 微信、天天動聽、滴滴打車、同花順、憤怒的小鳥2) were found to have backdoor. After investigation it was found that the developers in China used a trojaned Xcode (iOS development tool) on an unofficial website. In China, developers use local copies of Apple Xcode development environment hosted on unofficial websites due to network performance issues in accessing the Apple Xcode website.
The XcodeGhost had a large impact. Apple took the infected apps off the shelf. Affected users could update the apps to get disinfected. However, even as today, some enterprises are still using the infected apps and the threat still exists.
Youmi Ad SDK found spyware

n 2015, SourceDNA researchers found that Youmi’s new advertising SDK was illegally collecting information on users. Developers who created apps with Youmi Ad SDK were unaware that the SDK was collecting user information and sending back to Youmi’s server in China. Apple later took down all affected apps. The number if downloads of affected apps amounted to 1 million.
3. Firmware Contamination
Supply chain attack can occur in firmware. Firmware contamination is difficult to detect because pre-loaded firmware coming with devices is at a lower level than the operating system. It cannot be detected or removed by anti-malware software.
Zombie Zero poisoned handheld scanner firmware

In 2014, security consulting company TrapX discovered malware breaking into ERP system to steal financial, logistics and customer information. After investigation, the source of attack was found to be hand-held scanners with Embedded WinXP. The devices had a malware installed when they were shipped from the Chinese manufacturer. TrapX did not confirm if the scanner manufacturer knowingly shipped devices with pre-loaded malware.
4. Waterhole Attack
In Waterhole Attack, attacker poisons a website frequently visited by victims. Victims trusting the website were prompted to download.
Bad Rabbit ransomware via waterhole attack

In October 2017, the Bad Rabbit ransomware spread wildly in Russia, Ukraine, Bulgaria, Turkey and Germany. It was found to be spread by drive-by-download via waterhole attack. The compromised legitimate websites were popular ones in their countries, such as Radio Station in the US, Tourist Office and Hercegnovi Municipality in Montenegro, Defense association in Bulgaria, Bahmut Municipality of Ukraine, German booking website and Turkish twitter trend, booking website, SEO web services.
Attacker sets a trap and wait for the victim to come. Victims visiting the website would be either attacked by exploits on the browser and plugin vulnerability, or download a contaminated version of legitimate version of document or software and install by themselves.
New challenges to the supply chain in digital transformation
Our businesses are undergoing digital transformation and new service models are emerging. These new value chain requires closely coupling of supply chain partners in coordinating their resources to provide value. The accompany cyber security risks cannot be underestimated. They will bring in new forms of supply chain attacks.
1. Cloud services brokerage
Cloud services brokerage (CSB) is an IT role and business model in which a company or other entity adds value to one or more (public or private) cloud services on behalf of one or more consumers of that service via aggregation, integration and customization brokerage. For example, cloud access security broker (CASB) is a software tool or service that sits between an organization's on-premises infrastructure and a cloud provider's infrastructure, acting as a gatekeeper, allowing the organization to extend the reach of their security policies beyond their own infrastructure. Cloud service brokerage provides network interface and software API to enable the collaboration. Attackers who exploit vulnerabilities in these interfaces can launch attacks to downstream stakeholders.
2. Fintech
A lot of startups are emerging to enable technological innovation in financial services such as blockchain, artificial intelligence, machine learning, and aggregation of marketplace. These new partners has changed the in-premise processing model of the financial industry. They service multiple financial institutions and provide software API for service access. The startups are pioneers in innovation but in general are way behind in security practice. The compartmentation of their service among clients, the integrity of software library and software updates should be reviewed. The security management and compliance is a challenge to financial institutions.
3. Smart city and Internet of Things (IoT)
The number of devices connected to the Internet is growing exponentially. Sensors and actuators of different purpose, cameras and smart meters would be deployed as part of the services to detect traffic flow, environment parameters, usage of service and then use AI and machine learning (from another service provide on the supply chain) to predict future need of resources and automatically regulate the amount of supplies. These IoT devices and analytics services becomes part of the enabler of the public services. If attackers compromise the supplier of these devices or services, they can affect the downstream users.
4. Smart Industry
The innovation known as the fourth industrial revolution (or Industry 4.0) embraces vertical integration of smart factory production line and horizontal integration of supply chain partners, the aggregation of production data for big data analytics. The power to predict shortage of components and failure, to streamline production process would bring immense benefits. However, the network interfaces and software APIs are potentially attack targets. Successful compromise of one partner can affect the physical setup of the factory and the quality of products, or even cause hazard to human safety. It can also create a stepping stone for attackers to launch attacks to the other connected partners.
Tackling Supply Chain Attacks
Supply chain attack is complex and there is no simple defense. For example, it is hard to detect and remove malicious firmware because they sit below the operating system. Governments in global economies and the industries are considering the feasibility to enhance supply chain security in the supply side via regulation, security standards and practices.
At the user side, tackling the threat of supply chain attacks should start with partner management. We have to manage the security of supply chain partners.
1. Put third party security management in place
- Put third party security into security policy. Include cyber security risks related to third parties and related information flow into security risk assessment
- Purchase only from authorized suppliers; check supplier reputation
- Put in place controls in contracts, e.g. right to audit for third parties
- Employ network separation and restrict access of partners to enterprise network
- Test third party software and updates before deployment
2. Require service providers to implement security measures in service provision
- Provide contact point for incident reports
- Provide transparency to client of their security controls related to the service provision including access control and annual security audit
- Provide proof of authenticity and integrity to delivered software and patches
- Give timely notification of the cyber incidents and the critical vulnerability of their products and services
- Provide security awareness education to staff
3. Involve partners and contractors in company-side security awareness programme
- The End -
References
- HKPC Warns of More Financially-Motivated Cyber Attacks in 2018 /my_url/en/articles/18011801
- ENISA, “Supply chain attacks”, 29 August, 2017 https://www.enisa.europa.eu/publications/info-notes/supply-chain-attacks
- “What is a Supply Chain Attack”, Motherboard, September 2017. https://motherboard.vice.com/en_us/article/d3y48v/what-is-a-supply-chain-attack
- Proofpoint, “Threat Actor goes Chrome extension hacking”, 14 August 2017 https://www.proofpoint.com/us/threat-insight/post/threat-actor-goes-chrome-extension-hijacking-spree
分享至
