
Ransomware threat actors are spending less time on compromised networks before security solutions sound the alarm. In the first half of the year the hackers' median dwell time dropped to five days from nine in 2022
Statistics from cybersecurity company Sophos show that the overall median dwell time for all cyberattacks was eight days in the first half of the year, down from ten in 2022.
The company notes that ransomware attacks accounted for 68.75% of all cyberattacks recorded by Sophos this year.
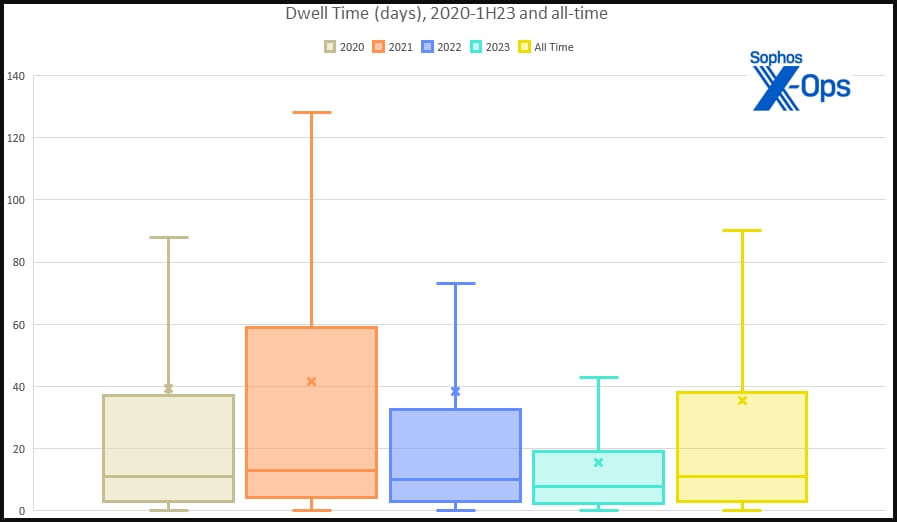
Sophos reports that median dwell time for non-ransomware incidents increased from 11 to 13 days this year. This suggests that while ransomware threat actors move quicker, other cybercriminals carrying out network intrusions "tend to linger" and wait for an opportunity.
The average dwell time stands at 15-16 days across all cases, while the maximum observed this year was over three months.
Sophos observed data exfiltration occurring in 43.42% of the cases, an increase by 1.3% from last year.
It appears that data theft is becoming more common, as the company saw fewer such attacks, down to 31.58% in H1 2023 from 42.76% in 2022. Supporting this trend is an increase in incidents where there was confirmation that no data was exfiltrated (up from 1.32% to 9.21%).
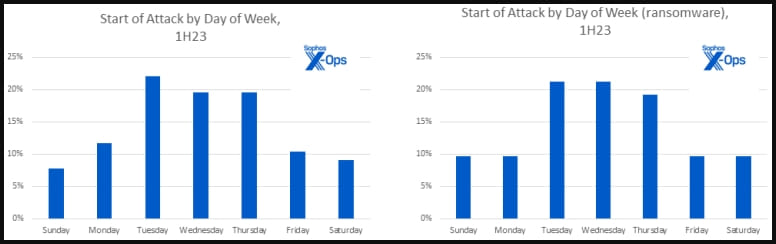
Interesting patterns also emerge when looking at Sophos data concerning days and times, indicating that threat actors, including ransomware operators, prefer to hit organizations on Tuesdays, Wednesdays, and Thursdays.
Threat actors attack their targets late in the local work day to catch IT teams understaffed and unlikely to detect the intrusion and its development on the network.
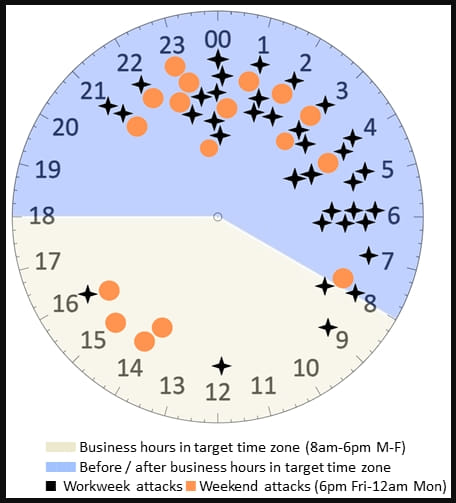
However, Sophos found that most ransomware incidents occur on Fridays and Saturdays, when companies are slowest to react because it is more difficult to reach out to tech teams.
One of the most abused tools remains the remote desktop protocol (RDP), which is built into most Windows versions. "Combined with the fact that the use of compromised credentials is rampant, and that single-factor authentication is the norm, it’s no mystery why attackers love it," Sophos says.
Statistics show that RDP was used in 95% of the intrusions. However, attackers used RDP mostly for internal activity (93% of the cases) and only in 18% cases externally.
For these reasons, Sophos recommends companies to make securing RDP a priority because denying this type of access could make a hacker spend too much time and effort to break in, which translates into more time to detect the intrusion.
Storing data for a reasonable period and checking it regularly is also an important factor, because it can help catch threat actors already on the network before they move to the final stage of an attack.
It can also provide key information for defenders and incident responders with a clear picture of what needs to be done and how to tackle the issue promptly.



Comments
GT500 - 8 months ago
I warned so many companies over the years to stop opening ports globally, and that only changing the port number wasn't enough to stop a real attacker. IT admins would always argue with me, claiming it wasn't necessary to keep ports for potentially vulnerable services like RDP closed. Hell, even the CTO for the company I worked at would argue with me and tell customers they didn't need to keep ports closed globally, until one day they decided that they needed to close the RDP port on their servers and use port knocking to temporarily open it for their IP when they needed to connect.
GoboFraggel - 8 months ago
Need to use that for my environment. We already use DUO, but this will help too.
horsedoggs - 8 months ago
We lock down the https rd gateway (rdp) or https vpn to only approved country’s in combination with duo for mfa.
GT500 - 8 months ago
Unfortunately that's easily bypassed with VPN's and proxies, and since there are some services that use home IP's (and those are apparently popular with criminals) it's difficult to actually block all threat actors unless you leave the ports closed globally and then use port knocking or single-packet authorization (SPA may be safer) to temporarily open a port for a single IP when needed.