
An affiliate of the BlackCat ransomware group, also known as APLHV, is behind the attack that disrupted MGM Resorts’ operations, forcing the company to shut down IT systems.
In a statement today, the BlackCat ransomware group claims that they had infiltrated MGM’s infrastructure since Friday and encrypted more than 100 ESXi hypervisors after the company took down the internal infrastructure.
The gang says that they exfiltrated data from the network and maintain access to some of MGM’s infrastructure, threatening to deploy new attacks unless an agreement to pay a ransom is reached.
Ransomware deployed, MGM data stolen
Cybersecurity research group vx-underground first broke the news that threat actors affiliated with the ALPHV ransomware operation allegedly breached MGM by impersonating an employee in a voice social engineering attack that targeted the company's help desk.
While BleepingComputer could not confirm if that was true, the BlackCat/ALPHV admin did confirm with BleepingComputer yesterday that one of their "adverts" (affiliate) carried out the MGM attack, saying that it wasn’t the same actor that hacked Western Digital in March.
Citing sources familiar with the matter, reports online [1, 2] later said that the threat actor that breached MGM Resorts is being tracked by cybersecurity companies as Scattered Spider (Crowdstrike).
Other companies use different names to track the same threat actor: 0ktapus (Group-IB), UNC3944 (Mandiant), and Scatter Swine (Okta).
According to Bloomberg reporters, Scattered Spider has also breached the network of Caesars Entertainment, who, in a U.S. Securities and Exchange Commission on Thursday, provided a strong hint at paying the attacker to avoid a leak of customer data stolen in the attack. The ransom demand was allegedly $30 million.
In their statement today, BlackCat says that MGM Resorts remained silent on the provided communication channel, indicating that the company has no intention to negotiate a ransom payment.
The hackers stress that the only action they saw from MGM was in response to the breach, disconnecting “each and every one of their Okta Sync servers after learning that we had been lurking on their Okta Agent servers.”
The attacker claims they were trying to sniff any passwords that they could not recover from the domain controller hash dumps.
Despite shutting down the synchronization Okta servers, the hackers continued to be present on the network, BlackCat says in their statement.
They claimed to still have super administrator privileges on MGM’s Okta environment and Global Administrator permissions to the company’s Azure tenant.
After seeing MGM taking this action and with no intention from the company to engage in negotiations over the provided chat, the threat actor says that they deployed the ransomware attack.
“After waiting a day, we successfully launched ransomware attacks against more than 100 ESXi hypervisors in their environment on September 11th after trying to get in touch but failing. This was after they brought in external firms for assistance in containing the incident,” - BlackCat/ALPHV.
At this moment, the hackers say that they do not know what type of data they stole from MGM but promise to extract relevant information and share it online unless they reach an agreement with MGM.
To pressure the company even more into paying, BlackCat threatened to use their current access to MGM’s infrastructure to “carry out additional attacks.”
BleepingComputer was not able to independently confirm BlackCat's claims and MGM has not replied to our emails.
Who is Scattered Spider
Scattered Spider is believed to be a group of threat actors who are known use a wide range of social engineering attacks to breach corporate networks.
These attacks include impersonating help desk personel to trick users into supply credentials, SIM swap attacks to take over the phone number of a targeted mobile device, and MFA fatigue and phishing attacks to gain access to multi-factor authentication codes.
Unlike most ransomware affiliates who are from CIS countries, researchers believe that the hacking group consists of English-speaking teenagers and young adults ranging from 16-22 years of age.
Furthermore, due to the similar tactics, researchers have noticed a connection between Scattered Spider and the Lapsus$ hacking group, which had a similar makeup for members and tactics.
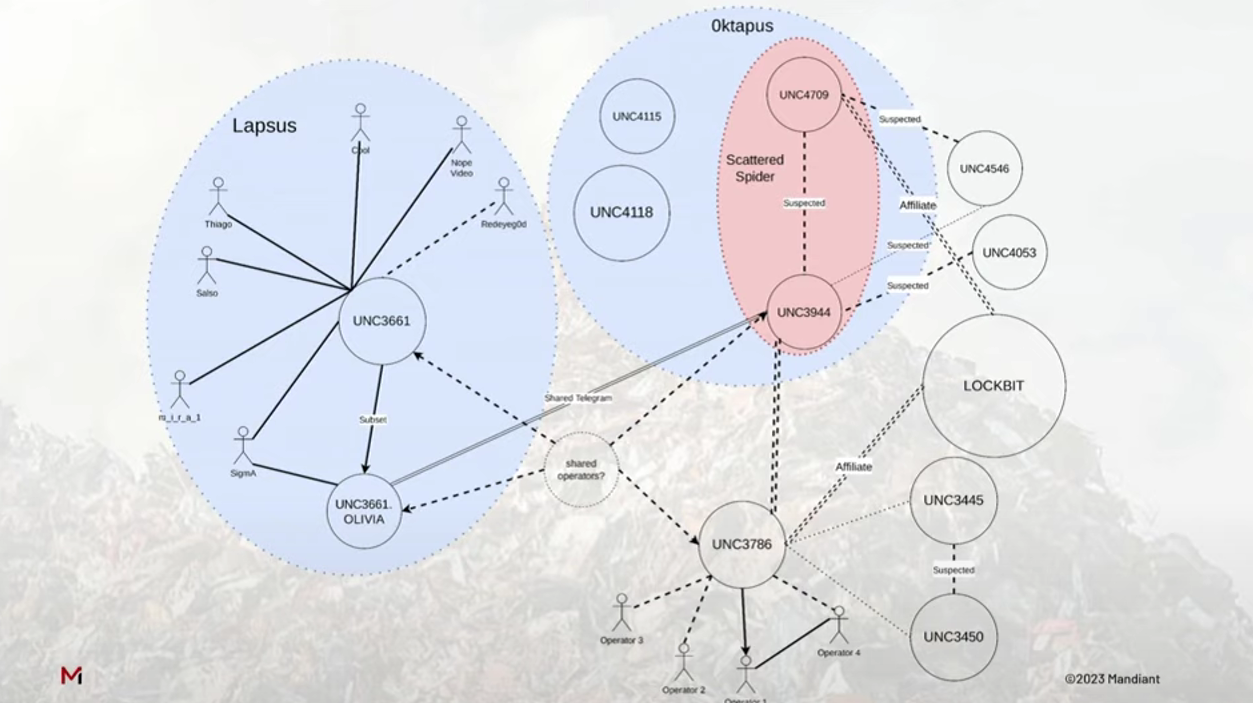
source: Jake Nicastro, Mandiant, at Sleuthcon 2023
A Scattered Spider campaign called '0ktapus' was used to target over 130 organizations to steal Okta identity credentials and 2FA codes, with some of those targets including T-Mobile, MetroPCS, Verizon Wireless, AT&T, Slack, Twitter, Binance, KuCoin, CoinBase, Microsoft, Epic Games, Riot Games, Evernote, AT&T, HubSpot, TTEC, and Best Buy.
Once the threat actors breach a network, they have a history of utilizing Bring Your Own Vulnerable Driver attacks to gain elevated access on a compromised device. This access is then used to further spread laterally on the network while stealing data and ultimately gaining access to admin credentials.
Once they gain access to admin credentials, they can perform further attacks, such as hijacking single sign-on administration, destroying backups, and, more recently, deploying the BlackCat/ALPHV ransomware to encrypt devices.
While the ransomware component is a relatively new tactic of the hacking group, almost all of their attacks involve extortion, where they demand million-dollar ransoms in return for not publishing data or to receive an decryptor.



Comments
Saigua - 7 months ago
S.b. "to receive a decryptor"
ilaion - 7 months ago
Thanks! Corrected!
sakethm - 6 months ago
Great... lets run agent based solutions on our critical infrastructure and have passwords reset over phone.
When everybody moving towards Just-in-time access I still can't believe there are people still sticking to ways, that were secure 10 years ago. Having agents on any server is stupid, everything is agentless now a days.