
MetaMask and Phantom are warning of a new 'Demonic' vulnerability that could expose a crypto wallet's secret recovery phrase, allowing attackers to steal NFTs and cryptocurrency stored within it.
Recovery phrases, otherwise known as “seeds,” are a series of words that function as a human-readable version of your wallet's private key.
Anyone who gains access to a wallet's recovery phrase can import the wallet onto their own devices, allowing them to steal all the cryptocurrency and NFTS stored within it.
The ‘Demonic’ vulnerability was discovered by Halborn, an organization devoted to blockchain cybersecurity, who found the flaw in September 2021 and reported it to wallet vendors for remediation.
Browser feature leads to exploit
The Demonic vulnerability is tracked as CVE-2022-32969 and is caused by how web browsers save contents of non-password input fields to the disk as part of their standard “restore session” system.
While using Google Chrome and Mozilla Firefox, the browsers will cache data inputted into text fields (other than password fields) so that the browser can restore the data after a crash using the 'Restore Session' feature.
As browser wallet extensions, such as Metamask, Phantom, and Brave, use an input field that is not designated as a password field, when a user enters their recovery phrase, it is saved on the disk in plain text form.
An attacker, or malware, with access to the computer, could then steal the seed and import the wallet on their own devices. This attack would require physically stealing the computer, having remote access, or compromising it with a remote access trojan, which is not uncommon in highly-targeted and persistent attacks.
However, if a hard drive is encrypted, even if it is stolen, the attacker would not be able to access the recovery phrase unless they had the decryption key.
Another prerequisite for exploitation, according to Halborn, is for the victim to have used the “Show Secret Recovery Phrase checkbox to view the phrase during import, which triggers local disk storage.
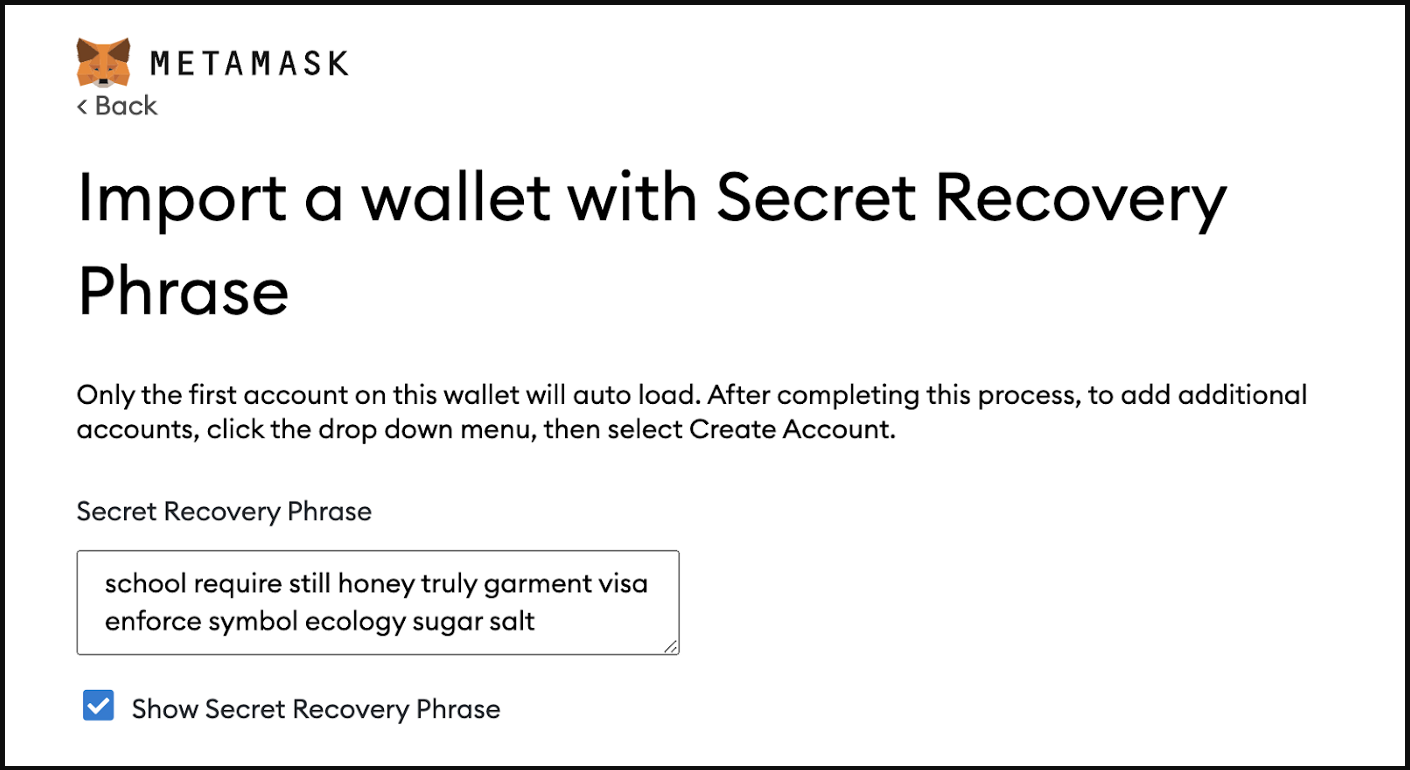
This action might be fairly common as many people use that feature to confirm that they have entered the correct words since those phrases are long and it’s easy to mistype something.
As Halborn explains, once the seed is stored in the disk, no matter if the system is restarted or the wallet browser extension is uninstalled, the recovery phrase will remain accessible to malicious actors.
Fix status and recommendations
Metamask fixed the problem with wallet extension version 10.11.3, xDefi addressed ‘Demonic’ in version 13.3.8, and Phantom plugged the critical flaw in April 2022.
Brave hasn’t released a statement on Demonic yet and has not responded to Bleeping Computer’s email while writing this. We will update this post when we receive a statement.
For those who believe this flaw might have impacted them, the recommended action is to migrate all assets to a new account.
Users who hold significant amounts of digital assets should always use disk encryption and avoid copy-pasting entire phrases on their browser or even desktop apps, as the clipboard is another point of information disclosure risk.
The most secure wallet remains a cold wallet, so this is still the best choice for cryptocurrency holders and digital investors who are willing to live with the drawbacks.
Halborn has posted a list of security recommendations for wallet developers on a separate webpage. Users who want to determine their wallets' security level may also read the guidance.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now