
Two vulnerabilities affecting some version of Jupiter X Core, a premium plugin for setting up WordPress and WooCommerce websites, allow hijacking accounts and uploading files without authentication.
Jupiter X Core is an easy-to-use yet powerful visual editor, part of the Jupiter X theme, which is used in over 172,000 websites.
Rafie Muhammad, an analyst at WordPress security company Patchstack, discovered the two critical vulnerabilities and reported them to ArtBee, the developer of Jupiter X Core, who addressed the issues earlier this month.
Flaw details
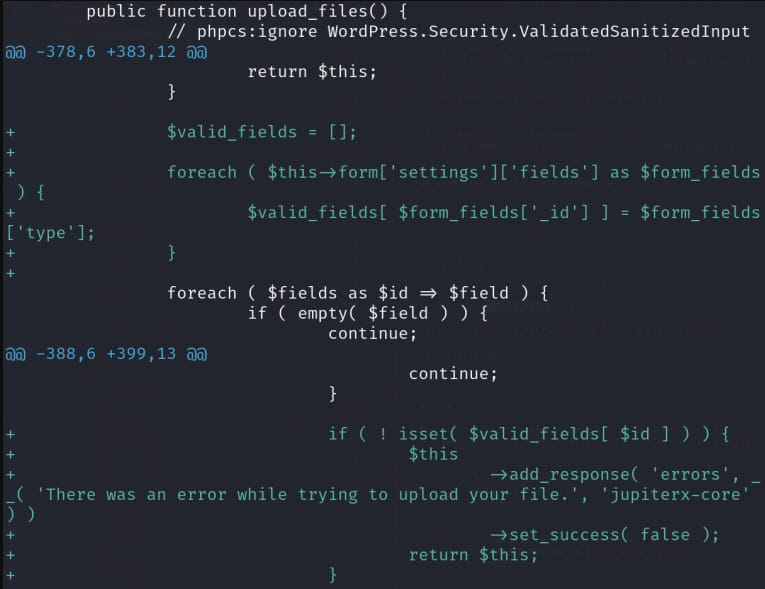
The first vulnerability is identified as CVE-2023-38388 and allows uploading files without authentication, which could lead to executing arbitrary code on the server.
The security problem has received a severity score of 9.0 and impacts all JupiterX Core versions starting 3.3.5 below. The developer fixed the problem in version 3.3.8 of the plugin.
CVE-2023-38388 can be exploited because there are no authentication checks within the plugin's 'upload_files' function, which can be called from the frontend by anyone.
The vendor's patch adds a check for the function and also activates a second check to prevent uploading risky file types.
The second vulnerability, CVE-2023-38389, allows unauthenticated attackers to take control of any WordPress user account on the condition that they know the email address. It received a critical severity rating of 9.8 and impacts all versions of Jupiter X Core starting from 3.3.8 and below.
ArtBees fixed the problem on August 9 by releasing version 3.4.3. All users of the plugin are recommended to update the component to the latest release.
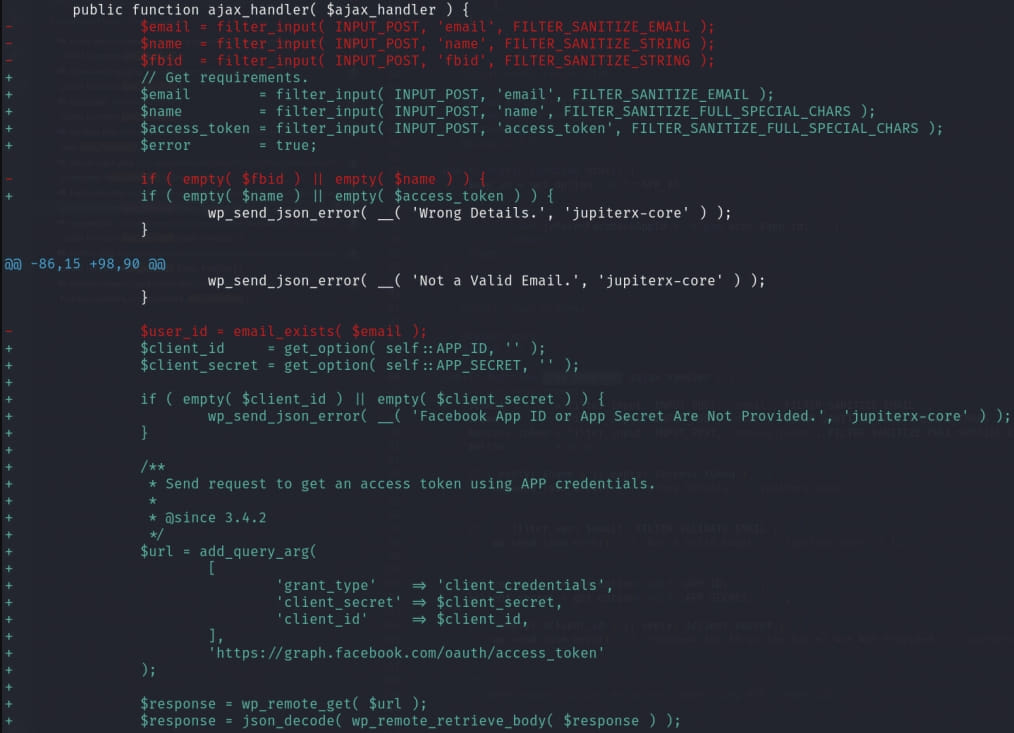
Rafie Muhammad explains that the underlying problem was that the 'ajax_handler' function in the Facebook login process of the plugin allowed an unauthenticated user to set any WordPress user's 'social-media-user-facebook-id' meta with any value through the 'set_user_facebook_id' function.
As this meta value is used for user authentication in WordPress, an attacker can abuse it to authenticate as any registered user on the site, including administrators, as long as they use the correct email address.
ArtBees' solution is to fetch the required email address and unique user ID directly from Facebook's authentication endpoint, ensuring the legitimacy of the login process.
Users of the JupiterX Core plugin are recommended to upgrade to version 3.4.3 as soon as possible to mitigate the severe risks posed by the two vulnerabilities.
At the time of writing we could not find any public reports about the two vulnerabilities being exploited in the wild.



Comments
PluginVulns - 8 months ago
Jupiter X Core isn't a premium plugin. It was available for free through WordPress' plugin directory until it was pulled last year because of one of a number of known security issues:
https://wordpress.org/plugins/jupiterx-core/
It's unclear why Patchstack doesn't know this and isn't warning people about using the plugin, considering the developer is known to not properly handle security. We did just that in June of last year: https://www.pluginvulnerabilities.com/2022/06/03/wordpress-plugin-developer-security-advisory-artbees/