
There’s a trick that allows attackers to hijack a victim’s WhatsApp account and gain access to personal messages and contact list.
The method relies on the mobile carriers’ automated service to forward calls to a different phone number, and WhatsApp’s option to send a one-time password (OTP) verification code via voice call.
The MMI code trick
Rahul Sasi, the founder and CEO of digital risk protection company CloudSEK, posted some details about the method saying that it is used to hack WhatsApp account.
BleepingComputer tested and found that the method works, albeit with some caveats that a sufficiently skilled attacker could overcome.
It takes just a few minutes for the attacker to take over the WhatsApp account of a victim, but they need to know the target’s phone number and be prepared do some social engineering.
Sasi says that an attacker first needs to convince the victim to make a call to a number that starts with a Man Machine Interface (MMI) code that the mobile carrier set up to enable call forwarding.
Depending on the carrier, a different MMI code can forward all calls to a terminal to a different number or just when the line is busy or there is no reception.
These codes start with a star (*) or a hash (#) symbol. They are easily found and from the research we did, all major mobile network operators support them.
“First, you receive a call from the attacker who will convince you to make a call to the following number **67* or *405*. Within a few minutes, your WhatsApp would be logged out, and the attackers would get complete control of your account” - Rahul Sasi
The researcher explains that the 10 digit number belongs to the attacker and the MMI code in front of it tells the mobile carrier to forward all calls to the phone number specified after it when the victim’s line is busy.
Once they tricked the victim into forwarding calls to their number, the attacker starts the the WhatsApp registration process on their device, choosing the option to receive the OTP via voice call.
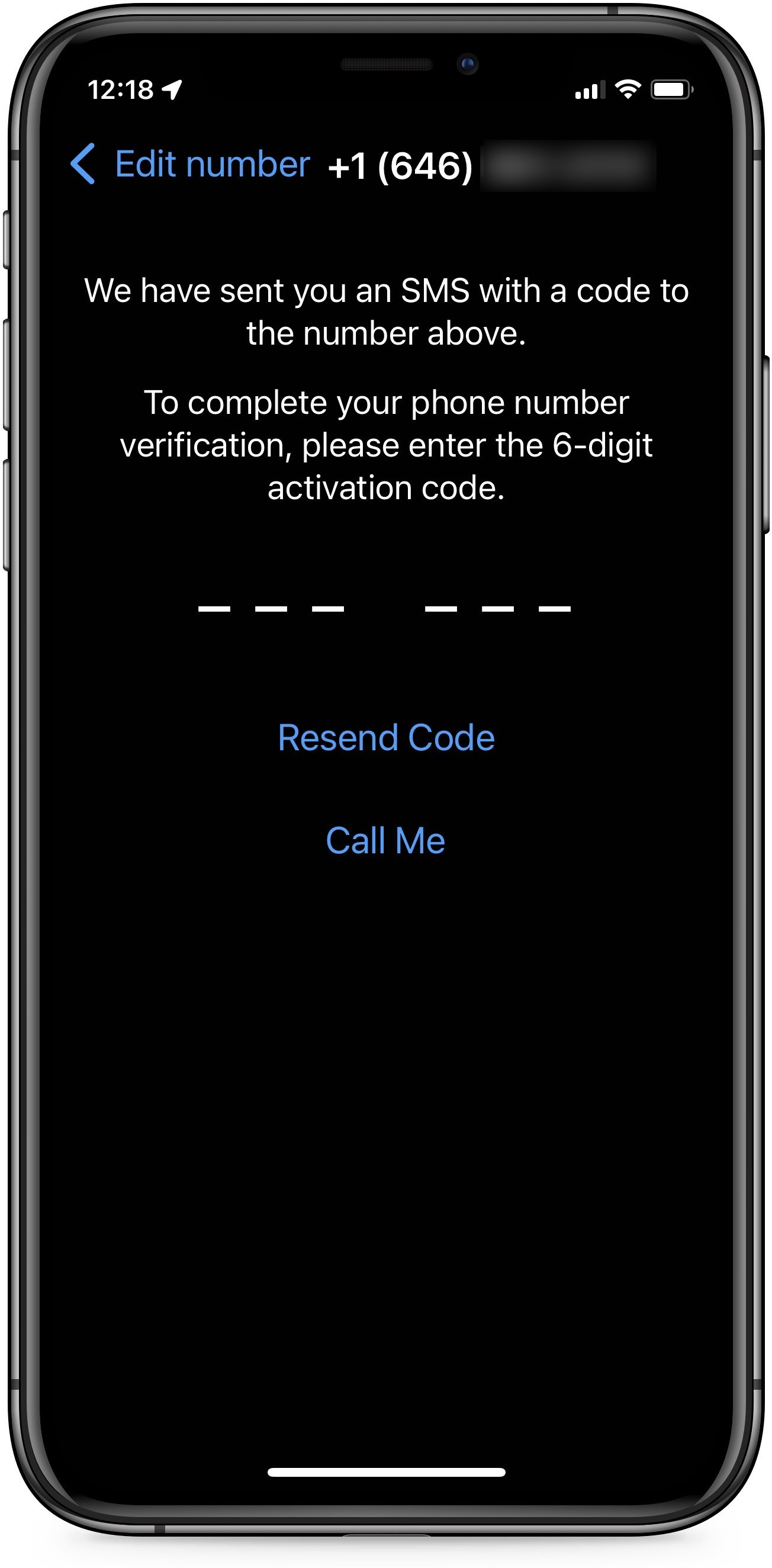
After they get the OTP code, the attacker can register the victim’s WhatsApp account on their device and enable two-factor authentication (2FA), which prevents legitimate owners from regaining access.
Some caveats
Although the method seems simple, getting it to work requires a little more effort, as BleepingComputer found during testing.
First off, the attacker needs to make sure that they use an MMI code that forwards all calls, regardless of the victim device’s state (unconditionally). For example, if the MMI only forwards calls when a line is busy, call waiting may cause the hijack to fail.
During testing, BleepingComputer noticed that the target device also received text messages informing that WhatsApp is being registered on another device.
Users may miss this warning if the attacker also turns to social engineering and engages the target in a phone call just long enough to receive the WhatsApp OTP code over voice.
If call forwarding has already been activated on the victim device, the attacker must use a different phone number than the one used for the redirection - a small inconvenience that might require more social engineering.
The most clear clue of suspicious activity for the target user occurs after the mobile operators turn on call forwarding for their device, since activation comes with a warning overlayed on the screen that doesn't go away until the user confirms it.
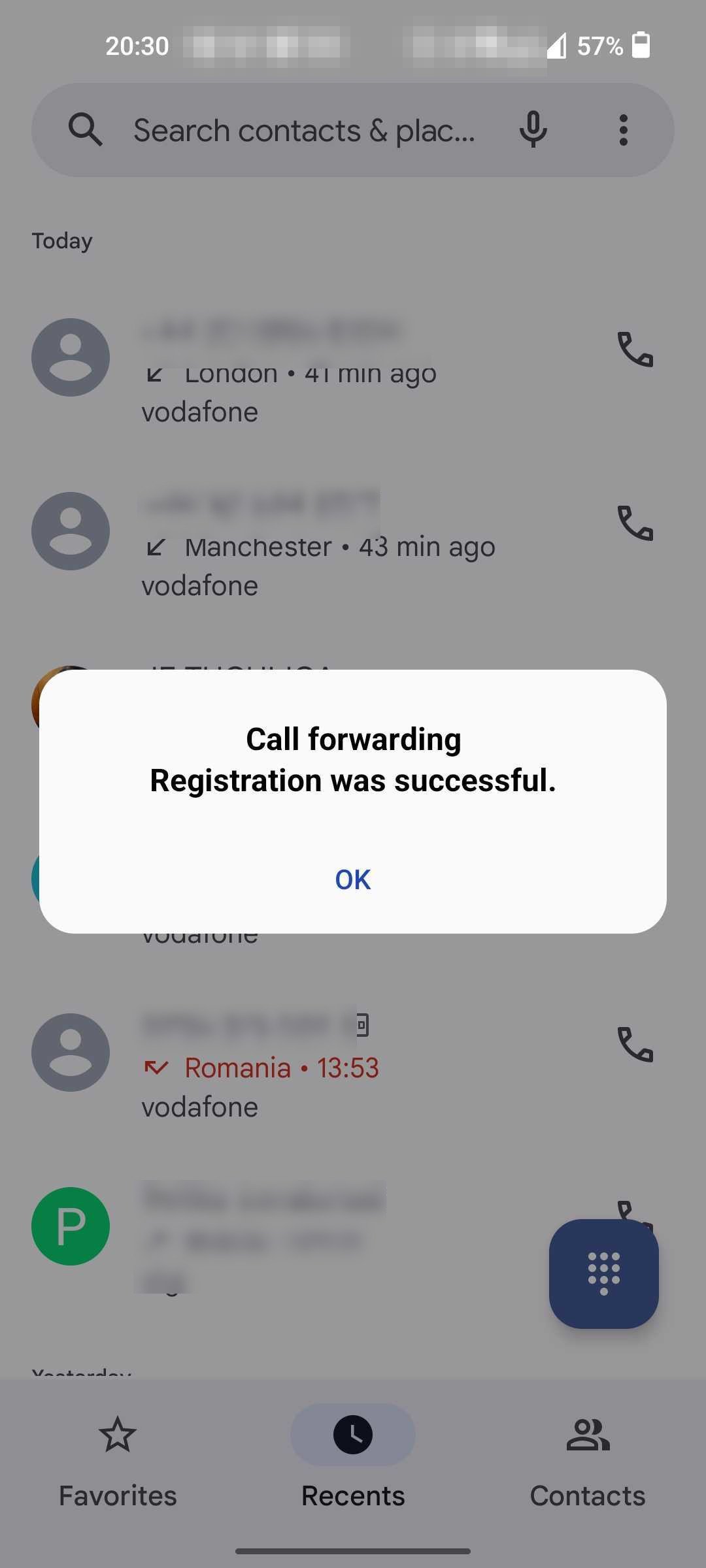
Even with this highly visible warning, threat actors still have a good chance of success because most users are not familiar with the MMI codes or the mobile phone settings that disable call forwarding.
Despite these obstacles, malicious actors with good social engineering skills can devise a scenario that allows them to keep the victim busy on the phone until they get the OTP code for registering the victim WhatsApp account on their device.
BleepingComputer has tested this method using mobile services from Verizon and Vodafone and concluded that an attacker with a plausible scenario is likely to hijack WhatsApp accounts.
Sasi's post refers to Airtel and Jio mobile carriers, each with more than 400 million customers as of December 2020, according to public data.
Protecting against this type attack is as easy as turning on two-factor authentication protection in WhatsApp. This feature prevents malicious actors from getting control of the account by requiring a PIN whenever you register a phone with the messaging app.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now