
Hackers are using a critical exploit chain to target Juniper EX switches and SRX firewalls via their Internet-exposed J-Web configuration interface.
Successful exploitation enables unauthenticated attackers to remotely execute code on unpatched devices.
"With a specific request that doesn't require authentication an attacker is able to upload arbitrary files via J-Web, leading to a loss of integrity for a certain part of the file system, which may allow chaining to other vulnerabilities," Juniper says.
One week after Juniper disclosed and released security updates to patch the four flaws that can be chained to achieve remote code execution, watchTowr Labs security researchers released a proof-of-concept (PoC) exploit targeting the SRX firewall bugs (tracked as CVE-2023-36846 and CVE-2023-36845).
While Juniper said there was no evidence of active exploitation, watchTowr Labs said they believe attackers would soon start targeting unpatched Juniper devices in widescale attacks.
"Given the simplicity of exploitation, and the privileged position that JunOS devices hold in a network, we would not be surprised to see large-scale exploitation," the researchers warned.
As expected, security researchers at the nonprofit internet security organization Shadowserver Foundation revealed today that they'd detected exploitation attempts starting the same day watchTowr Labs' PoC exploit was released.
"Since 25th August we are seeing exploitation attempts from multiple IPs for Juniper J-Web CVE-2023-36844 (& friends) targeting /webauth_operation.php endpoint," Shadowserver Foundation tweeted on Tuesday.
"Same day an exploit POC was published. This involves combining lower severity CVEs to achieve pre-auth RCE."
Shadowserver CEO Piotr Kijewski confirmed to BleepingComputer that the attackers are using exploits built using watchTowr Labs' PoC as inspiration.
"The exploitation attempts appear to be based on this exploit POC, with some variations, which attempts to upload a PHP file and then execute it. So I guess we may expect webshells," Kijewski said.
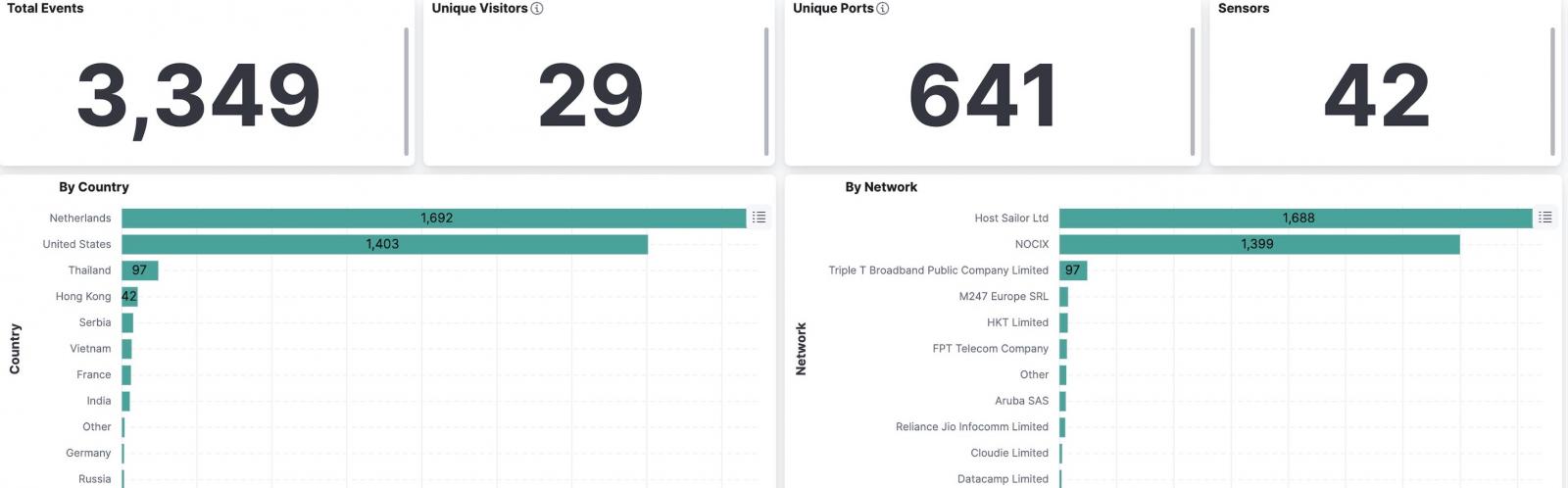
"Based on our honeypot observations, I would say all Juniper instances with J-Web exposed have already been hit. 29 IPs currently attempting these attacks, [..] possibly multiple threat actors."
Currently, over 8,200 Juniper devices have their J-Web interfaces exposed online, according to Shadowserver data, most of them from South Korea (Shodan shows more than 10,000 Intenet-exposed devices).
Admins are advised to apply patches or upgrade JunOS to the latest release immediately or, at least, disable Internet access to the J-Web interface to remove the attack vector.
.jpg)

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now