
Recent Flipper Zero Bluetooth spam attacks have now been ported to an Android app, allowing a much larger number of devices to implement these annoying spam alerts.
Inspired by previous research on the topic and Flipper Zero applets targeting iOS devices, and later Android and Windows, software developer Simon Dankelmann developed an Android app capable of the same Bluetooth spam.
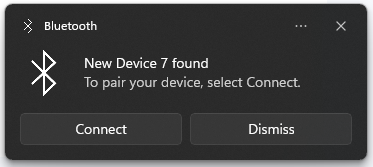
The Android app, named 'Bluetooth-LE-Spam,' can generate BLE (Bluetooth Low Energy) advertisement packages spoofing various devices to nearby Windows and Android devices, eliminating the need for a Flipper Zero.
The project is still in early development, but BleepingComputer's tests confirmed that it works as advertised.
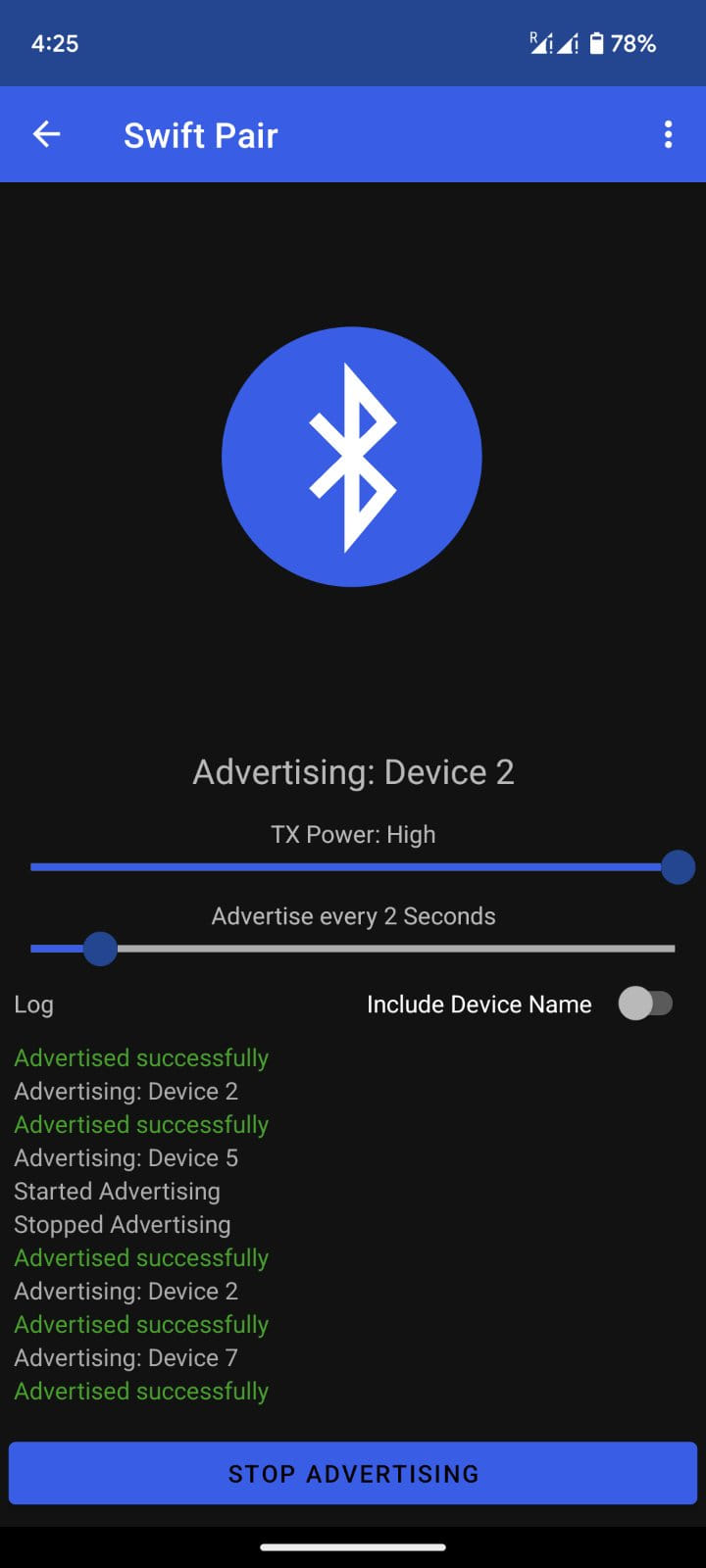
Specifically, the app can broadcast connection requests with set time intervals as frequent as 1 second, targeting 'Fast Pair' on Android or 'Swift Pair' on Windows.
BleepingComputer
One thing to note is that even though the Android API allows setting the transmission (TX) power level, developers have limited control over the actual data being broadcasted in relation to the TX power level.
This constraint by the Android SDK can result in poor reception from the target devices, which is not a problem in Flipper Zero, which can achieve a more extended and precise range when connecting to other devices.
In our tests, we found that some broadcasts were caught by the target only if the Android device generating them was as close as a few centimeters. In contrast, in other cases, notifications were generated from several meters away.
BleepingComputer
An interesting side-effect we noticed is that Bluetooth-connected devices like mice and keyboards can become unresponsive during spam broadcasts. This is another way of creating disruptive "denial of service" attacks on a target.
For now, the app stands as a demonstration of a possibility rather than a severe threat to users, but knowing how to turn off these notifications in the event you're targeted is good.
On Android, head to Settings → Google → Nearby Share, and turn the toggle on Show notification to the "Off" position.
[Update 11/4] Mishaal Rahman pointed out to BleepingComputer that a more effective solution would be to disable 'Fast Pair' on Android through Settings > Google > Devices & sharing > Devices and turning off "Scan for nearby devices."
On Windows, open Settings, select 'Bluetooth & devices' from the menu on the left, then click on 'Devices,' scroll down to 'Device settings,' and turn the 'Show notifications to connect using Swift Pair' toggle to the 'Off' position.
We recommend against testing the 'Bluetooth-LE-Spam' app on your main device for reasons of security, as BleepingComputer cannot provide any guarantees that the project is safe.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now