
Fake Bitwarden sites are pushing installers purportedly for the open-source password manager that carry a new password-stealing malware that security researchers call ZenRAT.
The malware is distributed to Windows users through websites that imitate the legitimate Bitwarden site and rely on typosquatting to fool potential victims.
Focused on Windows users
The purpose of ZenRAT is to collect browser data and credentials along with details about the infected host, a behavior consistent with an information stealer.
Cybercriminals can use the details to create a fingerprint of the compromised system that can be used to access an account as if the legitimate user logged in.
Security researchers at cybersecurity company Proofpoint discovered ZenRAT after receiving in August a sample of the malware from Jérôme Segura, Senior Director of Threat Intelligence at Malwarebytes.
The distribution point was “a very convincing lookalike to the real bitwarden.com” with a domain name specifically selected to trick visitors into believing they were accessing the official resource - bitwariden[.]com.
source: Proofpoint
Inside the fake Bitwarden installation package, Proofpoint researchers found a malicious .NET executable that is a remote access trojan (RAT) with info-stealing features they are now tracking as ZenRAT.
The malicious website provides the fake Bitwarden package only to Windows users, otherwise, it redirects to a cloned page of an opensource.com article about the password manager.
When trying to download the Bitwarden version for Linux or Mac, the user is redirected to the official download page of the software, Proofpoint notes.
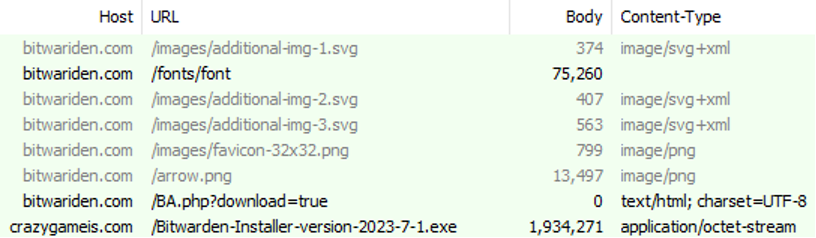
The malicious Bitwarden installer for Windows is delivered from crazygameis[.]com, another fake URL for the legitimate browser-based gaming platform CrazyGames.
source: Proofpoint
The researchers don't know how potential victims land on the fake Bitwarden site but phishing campaigns through Google ads have been used in the past to target Bitwarden users specifically.
Stealing data, evading analysis
Once running, ZenRAT uses WMI queries and other system tools to collect data about the host, which includes:
- CPU Name
- GPU Name
- OS Version
- Installed RAM
- IP address and Gateway
- Installed Antivirus
- Installed Applications
The details above are delivered to the command and control (C2) server in a ZIP archive that also includes data and credentials collected from the web browser.
Before communicating with the C2, though, ZenRAT makes sure that the host is not in a restricted region (Belarus, Kyrgyzstan, Kazakhstan, Moldova, Russia, and Ukraine).
The malware also checks if it is running in a virtual machine or a sandbox, a sign that researchers are analyzing it.
However, the researchers also discovered some strange information in the installer’s metadata, such as claiming to be the hardware info app Speccy, from Piriform.
Another peculiarity is data about the signer of the installer. Although the digital certificate is not valid, ZenRAT’s installer lists Tim Kosse, the developer of the open-source FileZilla FTP software, as the signer.
Despite having functions specific to an information stealer, Proofpoint has found evidence suggesting that the malware is designed to be modular and its capabilities can be expanded; however, no other modules have been observed in the wild.
The Bitwarden password manager has increased in popularity lately as it is regarded as a better alternative to other products on the market. With a growing user base, the software and its users become a target as cybercriminals take advantage



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now