
Proof-of-concept exploits for the actively exploited critical CVE-2022-26134 vulnerability impacting Atlassian Confluence and Data Center servers have been widely released this weekend.
The vulnerability tracked as CVE-2022-26134 is a critical unauthenticated, remote code execution vulnerability exploited through OGNL injection and impacts all Atlassian Confluence and Data Center 2016 servers after version 1.3.0.
Successful exploitation allows unauthenticated, remote attackers to create new admin accounts, execute commands, and ultimately take over the server.
The vulnerability was disclosed last week after Volexity discovered it was used by multiple threat actors in attacks. At the time, a patch was not available, and Atlassian advised admins to take servers offline or block them from being accessible from the Internet.
On Friday, Atlassian released security updates to fix the vulnerability just as attacks escalated in the wild.
Confluence exploits publicly released
Friday afternoon, a proof-of-concept exploit for the Atlassian Confluence vulnerability was publicly posted. The exploit soon spread widely online over the weekend, with researchers sharing examples on Twitter of how trivial it was to exploit.
Yesterday afternoon, Andrew Morris, the CEO of cybersecurity firm GreyNoise, tweeted that they had begun to see 23 unique IP addresses exploiting the Atlassian vulnerabilities.
Today, GreyNoise reports that the number of unique IP addresses attempting to exploit this vulnerability has grown almost ten times, to 211 unique IP addresses.
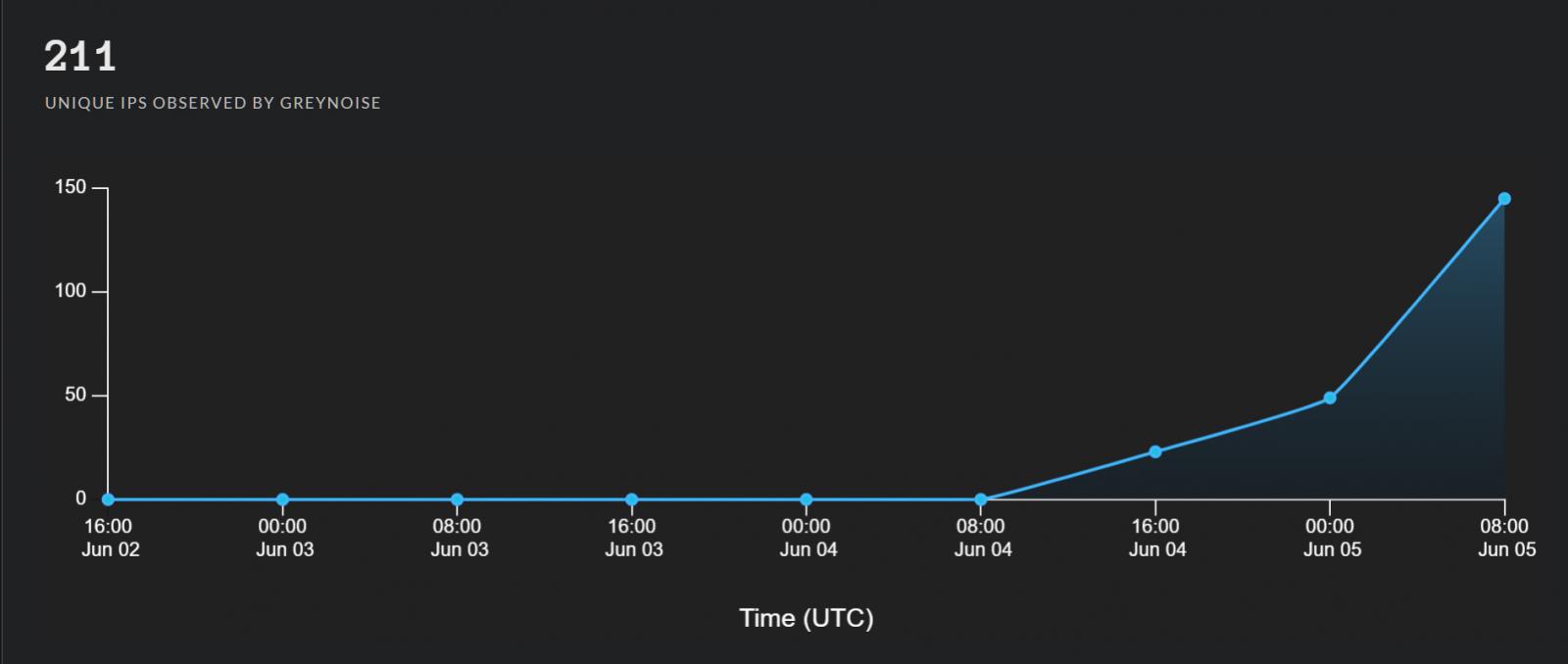
Source: GreyNoise
Confluence exploits posted online demonstrate how to create new admin accounts, force DNS requests, gather information, and generate reverse shells.
Patch your Confluence servers now
If you haven't yet patched the security vulnerability in your Confluence or Data Center servers, you should do so immediately before threat actors compromise them.
"Released versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1 which contain a fix for this issue," explains the Atlassian advisory.
If for some reason, you are unable to patch your servers immediately, Atlassian has provided mitigations for Confluence 7.0.0 through version 7.18.0.
As Confluence servers are an attractive target for initial access to a corporate network, devices should be updated immediately, mitigated, or taken offline.
Not doing so will ultimately lead to more significant attacks, including ransomware deployment and data theft.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now