
Scammers are impersonating the bankruptcy claim agent for crypto lender Celsius in phishing attacks that attempt to steal funds from cryptocurrency wallets.
In July 2022, crypto lender Celsius filed for bankruptcy and froze withdrawals from user accounts. Customers have since filed claims against the company, hoping to recover a portion of the funds.
Over the past few days, people have reported receiving phishing emails pretending to be from Stretto, the Claims Agent for the Celsius bankruptcy proceeding.
A recipient shared the phishing email with BleepingComputer, which claims to offer creditors a 7-day exit window to claim their frozen funds.
The email says they are from "Stretto Corporate Restructing," using the email address no-reply@stretto.com, as shown below.
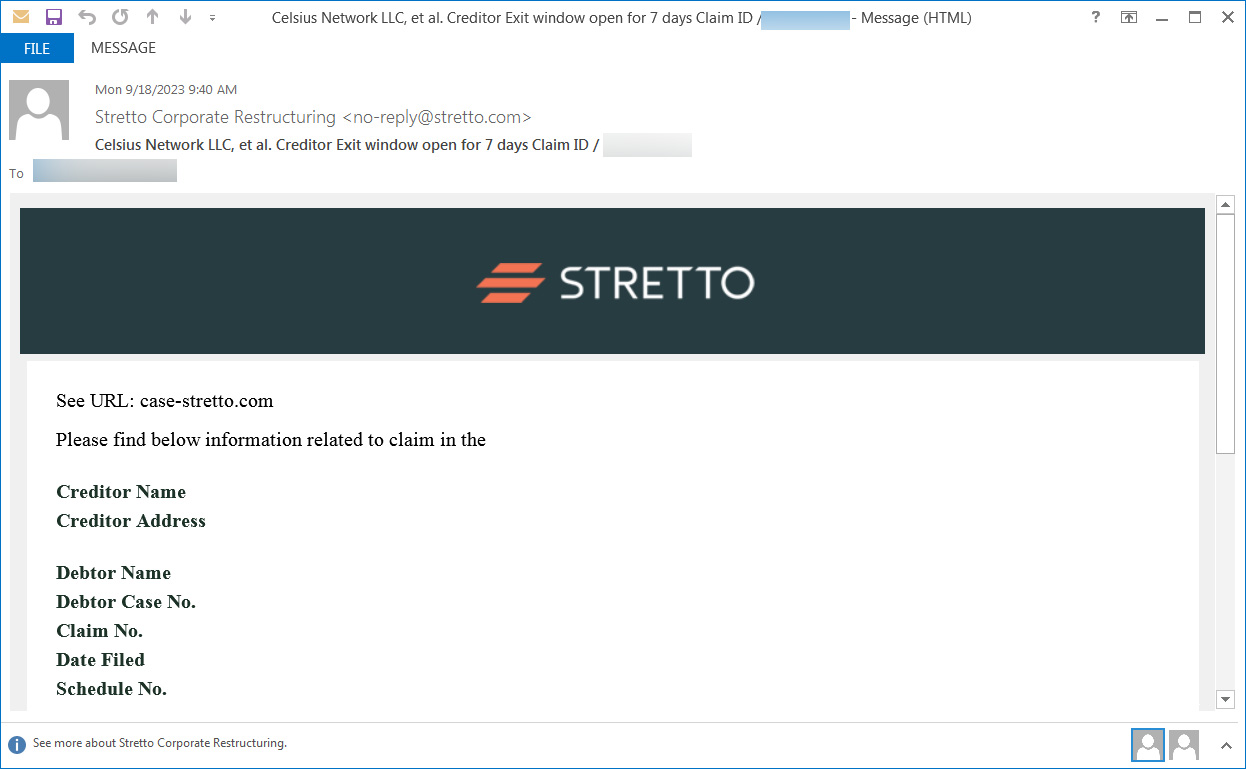
Source: BleepingComputer
The phishing email includes a link to the website case-stretto[.]com, which redirects the recipient to the phishing site claims-stretto[.]com below. The claims-stretto[.]com domain was registered today and is hosted at a web hosting provider in the Seychelles.
The legitimate Stretto site for Celsius claims is located at https://cases.stretto.com/celsius/claims/.
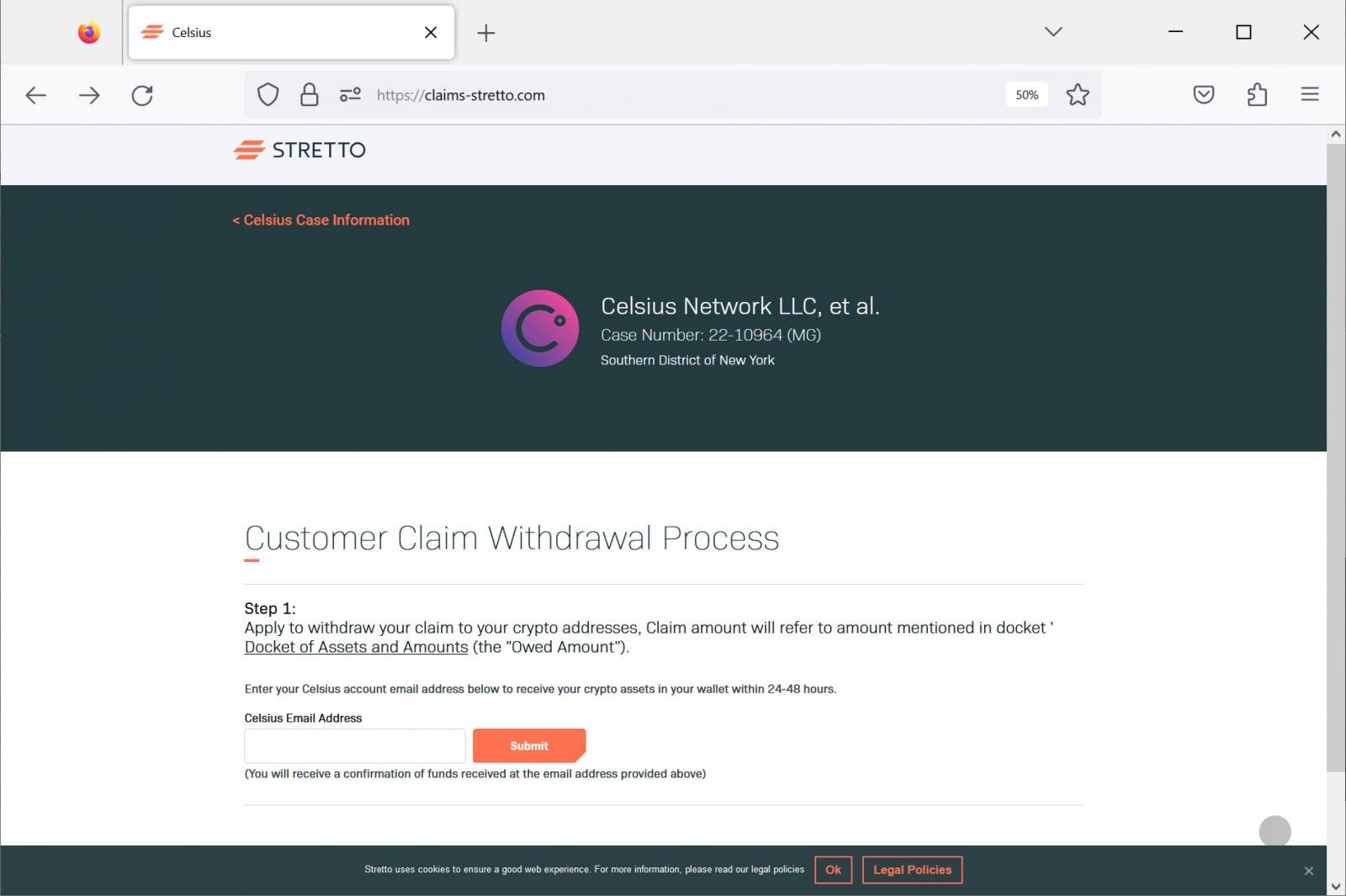
Source: BleepingComputer
The page prompts visitors to enter their email address to withdraw their claim, and when the submit button is pressed, it opens a WalletConnect prompt to connect your installed cryptocurrency wallet with the website.
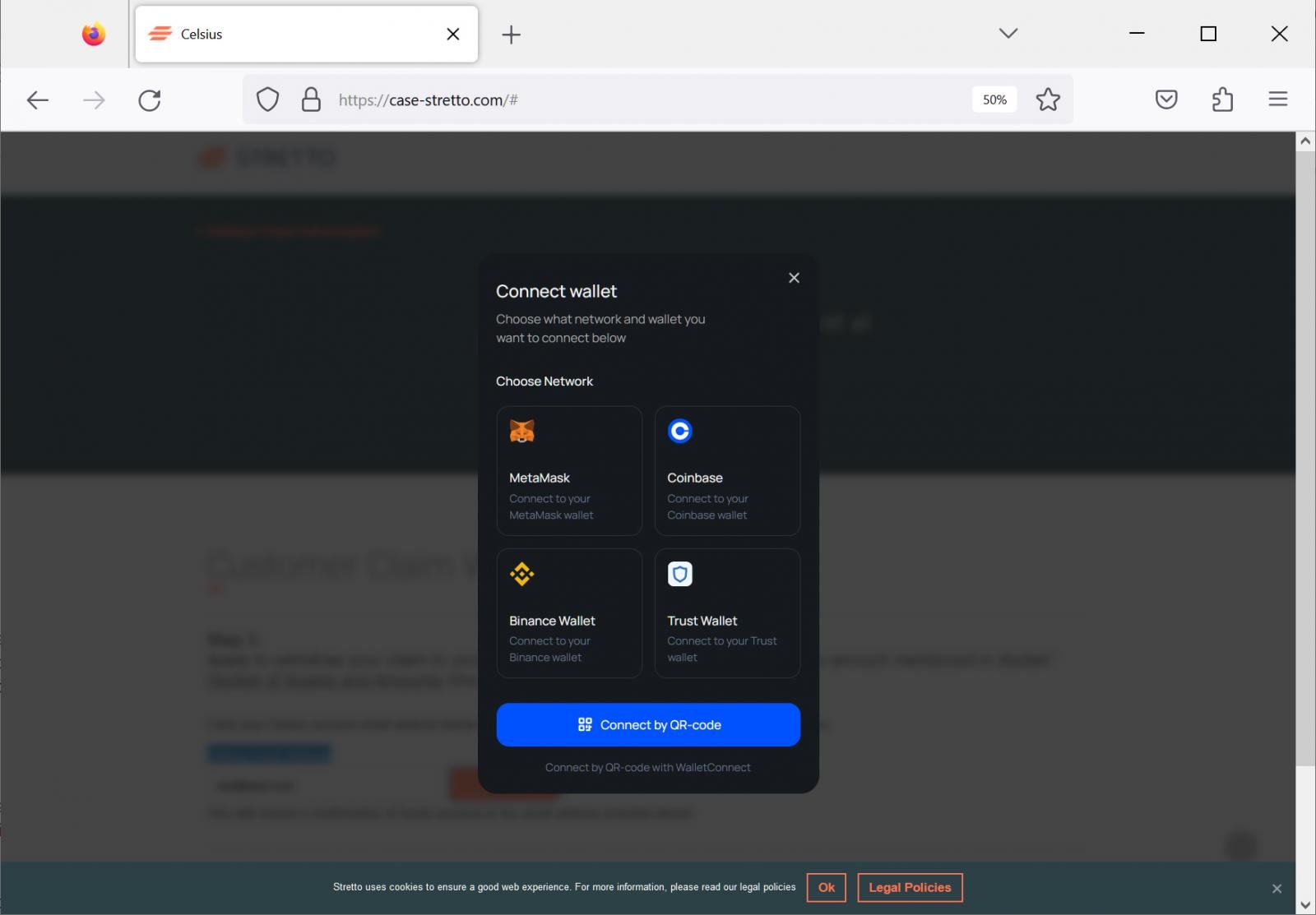
Source: BleepingComputer
If you connect a wallet, the site will now have access to all the information stored within it, including crypto addresses, balances, activity, and the ability to suggest transactions.
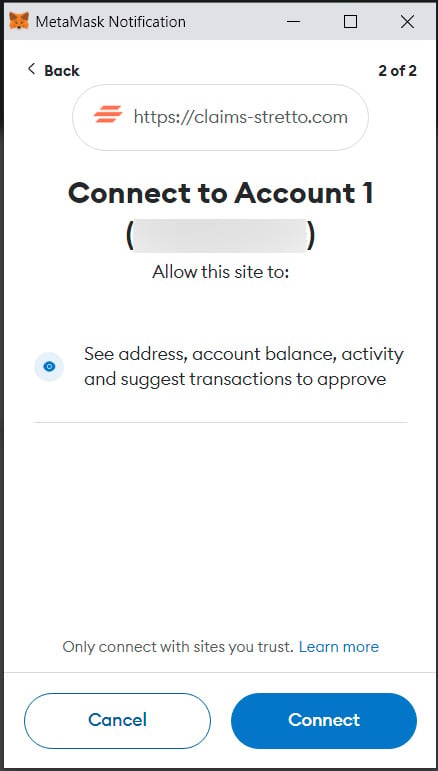
Source: BleepingComputer
With this connection in place, the threat actors can attempt to drain all assets and NFTs stored within the wallet by disguising the transaction as a deposit.
Passes SPF checks
This phishing campaign stands out because the emails pass Sender Policy Framework (SPF) checks, which determine if an email comes from a valid email server for the sending domain.
SPF performs this check by comparing the IP address of the mail server that sends the email to a list of IP addresses found in the DNS SPF record for the domain used in the 'Return-Path' mail header.
In this case, the phishing email's return path is 'bounces+xxx-xx=xxx.com@em6462.stretto.com', with em6462.stretto.com having an SPF record of v=spf1 ip4:149.72.171.199 -all. This SPF record means that any emails from 149.72.171.199 should be considered valid and not marked as spam.
As these phishing emails originate from 149.72.171.199, which belongs to the email marketing firm SendGrid, they pass the SPF check and are allowed for delivery.
This is illustrated below (some information is redacted), where the email is successfully delivered to Gmail after passing SPF checks.
ARC-Authentication-Results: i=1; mx.google.com;
dkim=pass header.i=@stretto.com header.s=s1 header.b=xx;
spf=pass (google.com: domain of bounces+xxx-xxx-xx=xxx.com@em6462.stretto.com designates 149.72.171.199 as permitted sender) smtp.mailfrom="bounces+xxx-xxx-xx=xxx.com@em6462.stretto.com";
dmarc=pass (p=QUARANTINE sp=QUARANTINE dis=NONE) header.from=stretto.com
A recipient of one of these phishing emails told BleepingComputer that they did not have an account at Celsius and never filed as a creditor, making it strange that they received this email.
The threat actors are likely using older contact lists previously stolen through hacked cryptocurrency marketing accounts.
BleepingComputer has reached out to Stretto to confirm if their SendGrid account was compromised to send these emails but has not received a reply.
If you receive an email claiming to be about Celsius' claims, please ignore it and check for new updates on the case at the legitimate https://cases.stretto.com/celsius/ site.
Unfortunately, if you have already visited one of these phishing sites and lost funds or NFTs after connecting your wallet, there is likely no way to recover your assets.
Celsius has previously reported similar phishing attacks used to steal creditors' funds.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now