
Security analysts have observed three new versions of Prilex PoS-targeting malware this year, indicating that its authors and operators are back in action.
Prilex started as ATM-focused malware in 2014 and it pivoted to PoS (point of sale) devices in 2016. While development and distribution peaked in 2020, the malware disappeared in 2021.
Kaspersky analysts now report that Prilex has returned, and last year's operational hiatus appears to have been a break to focus on developing a more sophisticated and potent version.
The latest installment is capable of generating EMV (Europay, MasterCard, and Visa) cryptograms, introduced in 2019 by VISA as a transaction validation system to help detect and block payment fraud.
As detailed in the Kaspersky report, it also enables the threat actors to use EMV cryptogram (encrypted messages between the card and the reader containing transaction details) to perform 'GHOST transactions' even using credit cards protected with CHIP and PIN technology.
"In GHOST attacks performed by the newer versions of Prilex, it requests new EMV cryptograms after capturing the transaction," to be used in fraudulent transactions, as Kaspersky explained.
.png)
Infection process and new capabilities
The infection begins with a spear phishing email impersonating a technician from a PoS vendor, alleging that the company needs to update its PoS software.
Next, the fake technician visits the target's premises in person and installs a malicious upgrade on the PoS terminals.
Alternatively, the attackers direct the victim to install the AnyDesk remote access tool on their computer and then use it to replace the PoS firmware with a laced version.
After the infection, the operators will evaluate the machine to determine if the target is prolific enough in terms of financial transaction volumes or if it's not worth their time.
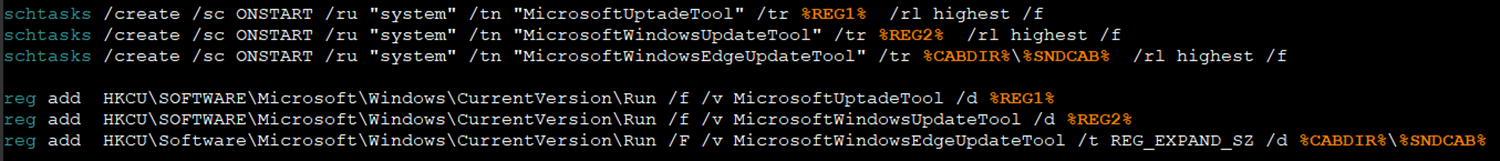
The new Prilex version has added a backdoor for communication, a stealer for intercepting all data exchanges, and an uploader module for exfiltration.
The backdoor supports various capabilities, such as file actions, command execution, process termination, registry modification, and screen capturing.
Its stealer module uses hooks on multiple Windows APIs to snoop on a communication channel between the PIN pad and the PoS software and can modify transaction contents, capture card information, and request new EMV cryptograms from the card.
The captured information is saved in encrypted form locally on the compromised computer and periodically uploaded to the malware's command and control (C2) server via HTTP POST requests.
"The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works," Kaspersky concluded.
"This enables the attackers to keep updating their tools in order to find a way to circumvent the authorization policies, allowing them to perform their attacks."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now