
The FBI is warning of a new tactic used by cybercriminals where they promote malicious "beta" versions of cryptocurrency investment apps on popular mobile app stores that are then used to steal crypto.
The threat actors submit the malicious apps to the mobile app stores as "betas," meaning that they are in an early development phase and are meant to be used by tech enthusiasts or fans to test and submit feedback to developers before the software is officially released.
The benefit of this approach is that beta apps do not go through a standard, rigorous code review process but are instead superficially scrutinized for their safety.
This less thorough code review process is insufficient to uncover the hidden malicious code that activates post-installation to perform various hostile actions.
"The malicious apps enable theft of personally identifiable information (PII), financial account access, or device takeover," explains the FBI.
"The apps may appear legitimate by using names, images, or descriptions similar to popular apps."
Usually, the apps mimic cryptocurrency investment and digital asset management tools, asking the user to enter their legitimate account details, deposit money for investments, etc.
Victims are directed to these apps via social engineering using phishing or romance scams, and they look legitimate as they are hosted on reputable app stores.
Sophos first documented this problem in March 2022 in a report that warned about scammers abusing Apple's TestFlight system, a platform created to help developers distribute beta apps for testing in iOS.
A more recent Sophos report explores a malicious app campaign called 'CryptoRom', which masquerades as cryptocurrency investment scam apps. These apps are promoted through the Apple TestFlight system, which the threat actors continue to abuse for malware distribution.
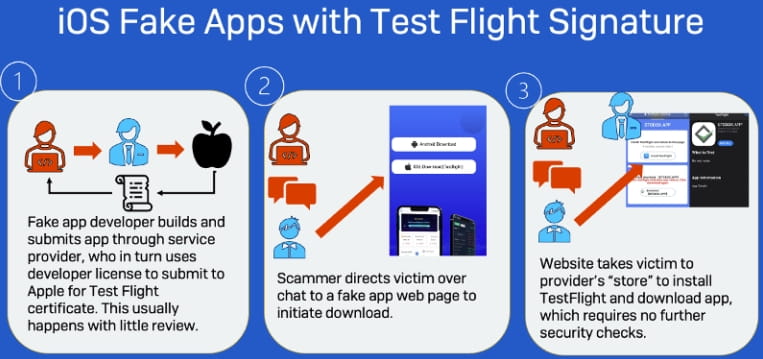
The threat actors initially upload what appears to be a legitimate app to the iOS app store for use on Test Flight.
However, after the app is approved, the threat actors change the URL used by the app to point to a malicious server, introducing the malicious behavior into the app.
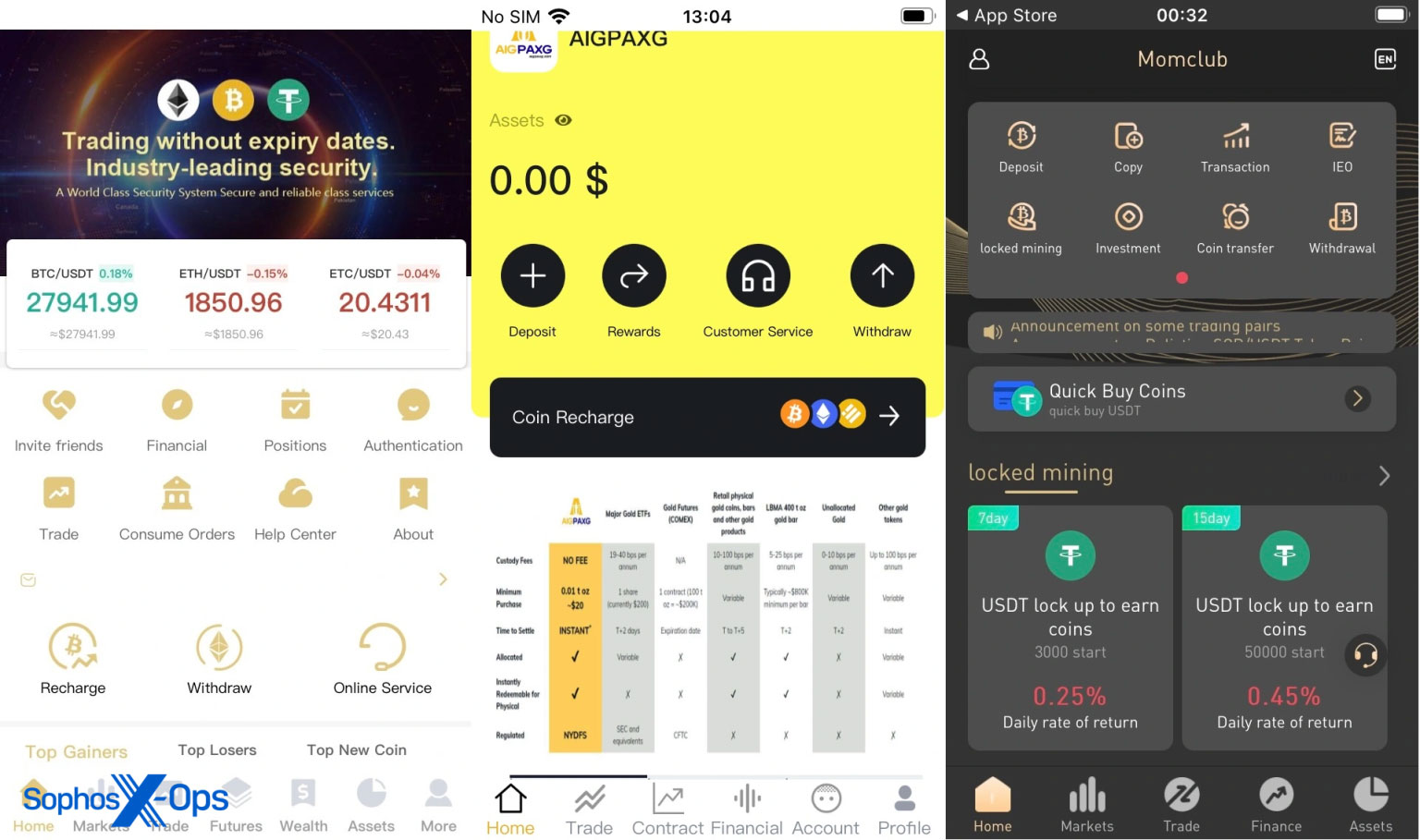
Source: Sophos
Google's Play store also supports the submission of beta testing apps. However, Google told BleepingComputer that the apps in open beta testing and publicly available on Google Play go through the same review process as apps that are in production, so there's no difference there.
FBI advised that you always confirm whether an app's publisher is reputable by reading user reviews on the app store and avoiding software with very few downloads or high download counts combined with very few or no user reviews.
Users should also be cautious during the installation phase of a new app and examine the requested permissions for anything that appears to be unrelated to that software's core functionality.
Some common signs of malware on your device include unusually high battery drain rate, elevated internet data consumption, sudden appearance of pop-up ads, performance degradation, and overheating.
Update 8/15 - Updated story to include statement from Google about their beta app review process.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now