
The enterprise has seen an explosion of Internet of Things (IoT) devices. Today we see more connectivity options at the edge and the need to place computing as close to the data as possible to gain valuable business insights. It has led to the proliferation of IoT devices and Internet-connected smart devices.
Despite the advantages and efficiencies of using IoT devices at the edge, it can serve as a blind spot for organizations from a security perspective. How is IoT being used in the enterprise, and how can it be secured? We will consider important security best practices and how a secure password policy is paramount to the security of devices.
What are Internet of Things (IoT) devices?
In general, IoT refers to devices with embedded software, sensors, network connectivity, and other technologies, allowing them to exchange data with other devices connected to the Internet. IoT devices range from household appliances (refrigerators, thermostats, ovens, microwaves, and other appliances) to industrial tools, sensors, and machines in manufacturing facilities. These connected "things" can collect and exchange many types of data.

With the prevalence of broadband network connectivity, wireless networks, and now 5G mobile networks in remote locations, it is now possible to connect any device to the network, including IoT devices. As a result, traditionally "dumb" devices are now transitioning to "smart devices" with the ability to be Internet-connected.
IoT devices are particularly common in the healthcare and manufacturing industries, where business-critical operations and data pass through internet-connected devices like monitors, tablets, scanners, and more.
Why is IoT revolutionizing data collection for businesses?
When you think about the capabilities of IoT devices and the possibilities for collecting and exchanging data, it opens a whole new world of opportunity for businesses to harness the power of data collection.
With IoT devices, the world we live and work in becomes "hyperconnected" so that literally everything around us can collect data and communicate this data to be analyzed. For businesses, it means data collection and analytics sensors can be located everywhere and on everything, giving real-time feedback available for analysis by big-data platforms.
Businesses realize the benefits and value coming from IoT devices, including:
- Businesses can improve productivity and efficiency with the insights gained from IoT-connected devices
- Companies can collect data-driven insights to help make businesses decisions
- It helps businesses realize the full potential of their revenue streams and develop new revenue models
- It allows easily connecting the physical world with the digital world, which helps to drive innovation, agility, efficiency, and new understandings of data models
IoT devices work hand-in-hand with modern machine-learning algorithms allowing the mass of collected data to be analyzed very quickly, allowing businesses to extrapolate intelligent business insights. In addition, the analyzed data allows gaining visibility to statistics, KPIs, and other metrics. These may be used to identify anomalies with equipment performance or send alerts based on various thresholds configured.
Architecture of IoT
What is the architecture of IoT systems, and what hardware, services, and applications does it include? Today, modern IoT systems include a combination of the following:
- Wireless networks – Wireless networks are the connectivity platform for IoT systems and enable IoT smart devices and sensors to be placed anywhere wireless networks can reach
- Cloud or private data center database locations – Cloud or private data center database locations store the mass of information and telemetry data generated, captured, and communicated by the IoT device
- Hardware sensors – Hardware sensors collect data from a wide range of systems depending on the device, the use case, and other aspects
- Smart devices – Smart devices are traditionally "dumb" devices that perform various tasks that now have embedded intelligent sensors and now have the capability to connect to wireless networks for transmitting the data collected
- Compute engines – Compute engines serve the purpose of analyzing and providing intelligent insights from the raw data collected from IoT devices and hardware sensors
IoT security implications
While IoT is an amazingly powerful technology that organizations can benefit from, businesses do well to consider the security implications of IoT as this relates to their overall security posture. What are the current security challenges facing businesses with IoT device implementations?
- Misconfiguration and poor password management
- Vulnerabilities and patch management
- DDoS attacks
- Lack of physical security
- Insecure protocols
1. Misconfiguration and poor password management
One of the primary challenges with IoT device implementations is misconfiguration and poor password management. Many IoT devices and sensors may default to an "open," insecure configuration out-of-the-box. It often includes a very weak "default" password shared among all the IoT devices of the same model/vendor. It may also include defaulting to insecure communication protocols, or dangerous connectivity options turned on by default, such as telnet, FTP, and others.
Organizations must ensure they are correctly reconfiguring the "defaults" to more secure device configurations. Integrating IoT devices with LDAP authentication provides a much more secure configuration allowing IoT device authentication to align with corporate Active Directory Password Policies and be centrally controlled. Admins should change the default passwords to strong, unique local device passwords or disable them altogether.
2. Vulnerabilities and patch management
Vulnerabilities provide additional challenges related to IoT devices. Like other technology systems with a specific combination of hardware and software, vulnerabilities can arise based on legacy software, firmware security, and zero-day vulnerabilities.
IT Security teams need to have a routine patching schedule for their various IoT devices or other compensating controls in place to diminish the risk posed by running outdated software if newer software patches cause issues with interoperability between legacy systems.
3. DDoS attacks
A major security issue posed by IoT devices is their use in the amplication of DDoS attacks. DDoS, or Distributed Denial of Service attacks, use massive groups of compromised systems to overwhelm network security defenses such as perimeter firewalls to disrupt or "deny" traffic.
Due to their notoriously insecure "defaults," including default passwords, IoT devices are an easy target for takeover by malicious attackers who use them in massive Botnet-driven DDoS attacks. According to one report, DDoS attacks were surpassing 4 Tbps (terabits per second) in an analysis of more than 10,000 DDoS attacks gathered from ISPs worldwide.
4. Lack of physical security
IoT devices are often located in areas that may lack physical security (manufacturing facilities, warehouses, shop floors, hospital hallways, etc.). Suppose an attacker is able to gain physical access to an IoT device. In that case, they may bypass the device's built-in security, compromising the device, loading malware, or other backdoors in the system.
Organizations must think about the physical security of IoT devices and also bolster their data security with encryption and other best practices for an effective "layered" security approach.
5. Insecure protocols
One of the defaults that may pose security risks to businesses is insecure protocols. Like a weak default password, weak default protocols, such as HTTP vs. HTTPS, can allow attackers to intercept traffic or perform network "snooping" to easily see sensitive data communicated over the network.
Companies must ensure they disable weak default protocols and only enable and use secure protocols for communication between IoT devices.
Bolster IoT Password security with Specops
Integrating IoT device authentication is a great way to bolster IoT password security. However, this presupposes you have a robust, secure Active Directory Password Policy in place to control and secure your AD passwords effectively. By default, Active Directory Domain Services (AD DS) has minimal built-in controls as part of the default AD Password Policies available.
Specops Password Policy bolsters the capabilities of Active Directory Password Policies to increase password security and the overall cybersecurity stance of your organization, including AD-integrated IoT devices. In addition, it adds missing password security features to help protect your organization from many types of attacks, including breached passwords.
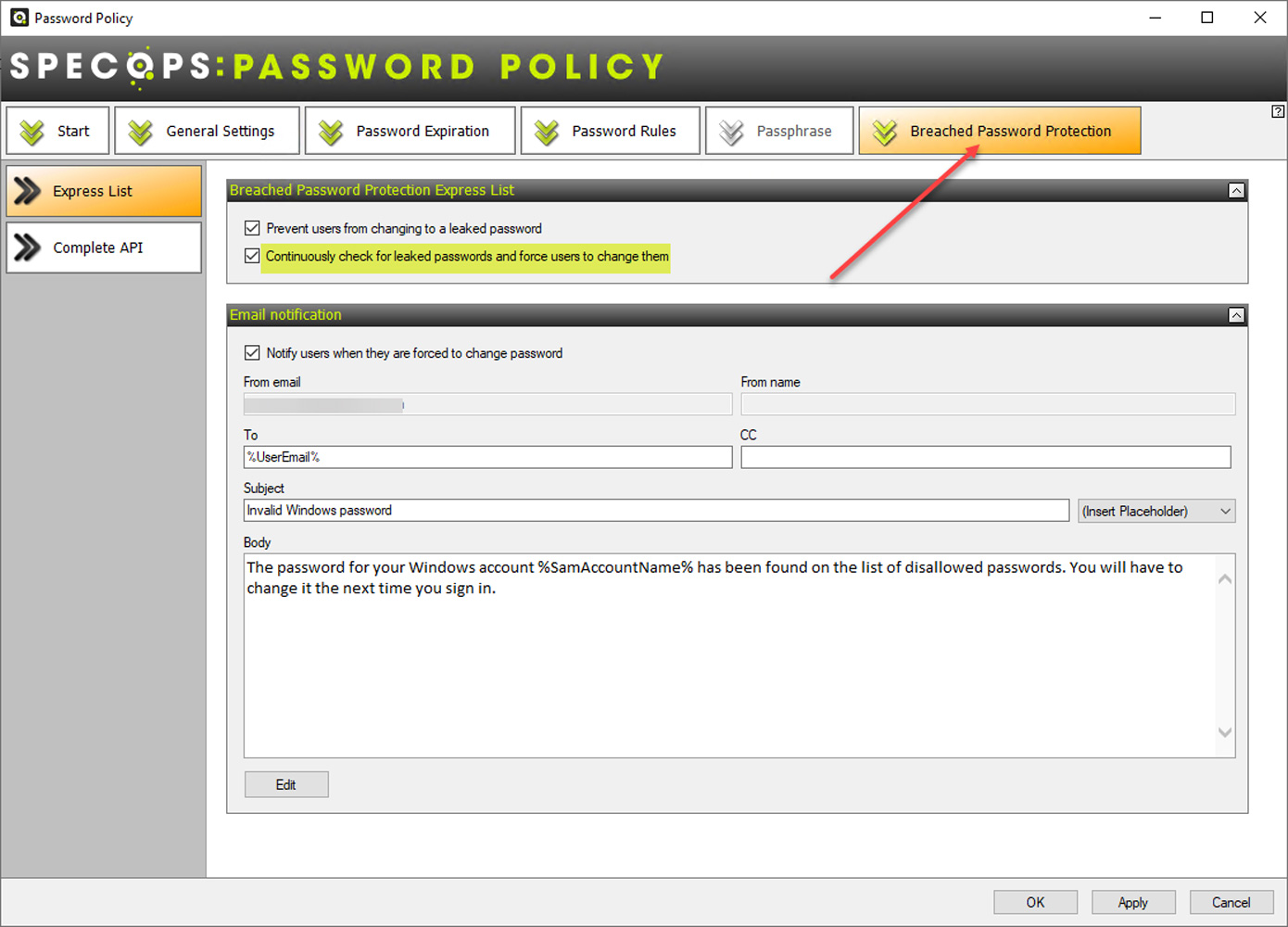
Organizations can start protecting their user's passwords with Breached Password Protection with just a few clicks in the Specops Password Policy configuration settings. With the continuously check for leaked passwords and force users to change them setting, you can leverage Specop Password Policy's enhanced honeypot intelligence for the most late-breaking breached passwords available.
Wrapping Up
IoT devices are bringing exciting capabilities and benefits to businesses, allowing them to capture, process, and gain intelligence from real-time data collected at the edge. However, organizations do well to consider the security implications of IoT devices, including weak passwords configured by default.
Integrating IoT devices with Active Directory offers many benefits to securing IoT infrastructure, including centralized Active Directory Password Policies. First, however, businesses must ensure their Active Directory passwords are protected from modern password security threats, such as breached passwords. Specops Password Policy bolsters the security of default Active Directory Password policies, allowing these to be protected against threats such as breached passwords, incremental passwords, and credential stuffing.
Learn more about Specops Password Policy and see how it can help your business bolster your password security strategy.
Sponsored and written by Specops.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now