
A new Mirai-based botnet malware named Enemybot has been observed growing its army of infected devices through vulnerabilities in modems, routers, and IoT devices, with the threat actor operating it known as Keksec.
The particular threat group specializes in crypto-mining and DDoS; both supported by botnet malware that can nest in IoT devices and hijack their computational resources.
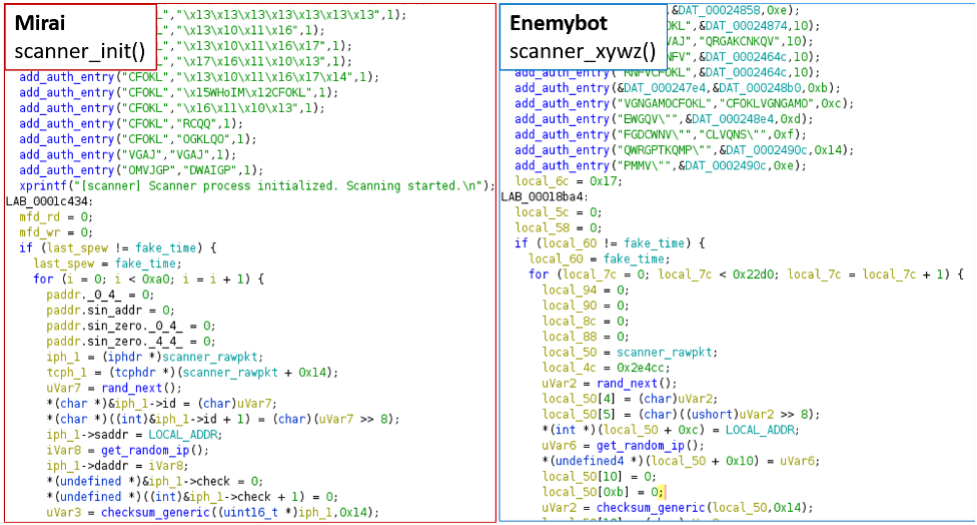
Enemybot features string obfuscation while its C2 server hides behind Tor nodes, so mapping it and taking it down is quite challenging at this time.
Still, it has been spotted in the wild by threat analysts at Fortinet, who have sampled the malware, analyzed it, and published a detailed technical report on its functions.
Enemybot’s capabilities
When a device is infected, Enemybot begins by connecting to the C2 and awaiting commands to execute. Most of the commands are related to DDoS (distributed denial of service) attacks, but the malware isn’t strictly limited to it.
More specifically, Fortinet presents the following set of supported commands:
- ADNS – Perform DNS amplification attack
- ARK – Perform an attack on the servers of the game “ARK: Survival Evolved”
- BLACKNURSE – Flood the target with Destination Port Unreachable ICMP messages
- DNS – Flood DNS servers with hardcoded DNS UDP queries
- HOLD – Flood the target with TCP connections and hold them for a specified time
- HTTP – Flood the target with HTTP requests
- JUNK – Flood the target with random non-zero-byte UDP packets
- OVH – Flood OVH servers with custom UDP packets
- STD – Flood the target with random-byte UDP packets
- TCP – Flood the target with TCP packets featuring spoofed source headers
- TLS – Perform SSL/TLS attack
- UDP – Flood the target with UDP packets featuring spoofed source headers
- OVERTCP – Perform TCP attack with randomized packet delivery intervals
- STOP – Stop ongoing DoS attacks
- LDSERVER – Update download server for exploit payload
- SCANNER – Spread to other devices via SSH/Telnet brute-forcing and exploits
- SH – Run shell command
- TCPOFF/TCPON – Turn sniffing off or on at ports 80, 21, 25, 666, 1337, and 8080, possibly to collect credentials
The commands targeting the ARK game and the OVH servers are of particular interest, which may indicate extortion campaigns targeting these companies.
Also, the LDSERVER command allows the threat actors to push out new URLs for payloads to deal with any problems in the download server. That's notable because most Mirai-based botnets have a fixed, hard-coded download URL.
Targeted archs and flaws
Enemybot targets multiple architectures, from the common x86, x64, i686, darwin, bsd, arm, and arm64, to scarcer and obsolete system types like ppc, m68k, and spc.
This is very important for the malware’s spreading capabilities, as it can identify the architecture of the pivot point and fetch the matching binary from the C2.
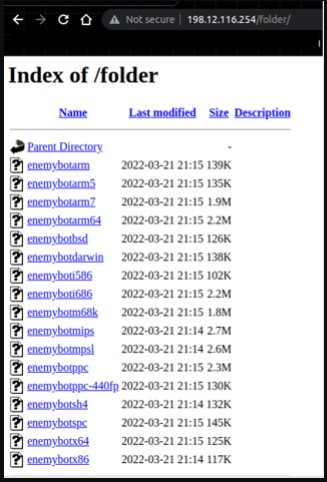
(Fortinet)
In terms of the targeted vulnerabilities, Fortinet has seen some differences in the sets between the sampled variants, but the three present everywhere are:
- CVE-2020-17456: Critical (CVSS 9.8) remote code execution (RCE) flaw in Seowon Intech SLC-130 and SLR-120S routers.
- CVE-2018-10823: High severity (CVSS 8.8) RCE flaw affecting multiple D-Link DWR routers.
- CVE-2022-27226: High severity (CVSS 8.8) arbitrary cronjob injection impacting iRZ mobile routers.
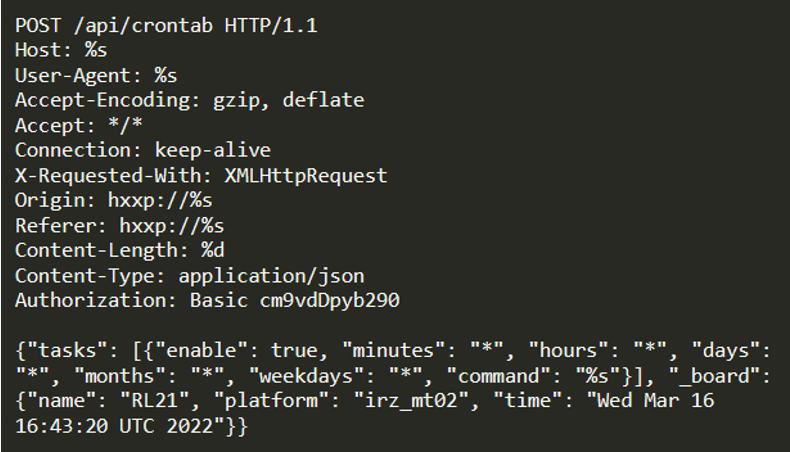
Other flaws that may or may not be present in Enemybot depending on the variant are:
- CVE-2022-25075 to 25084: Set of flaws targeting TOTOLINK routers. The same set is also exploited by the Beastmode botnet.
- CVE-2021-44228/2021-45046: The Log4Shell and subsequent critical vulnerabilities targeting Apache Log4j.
- CVE-2021-41773/CVE-2021-42013: Targets Apache HTTP servers
- CVE-2018-20062: Targets ThinkPHP CMS
- CVE-2017-18368: Targets Zyxel P660HN routers
- CVE-2016-6277: Targets NETGEAR routers
- CVE-2015-2051: Targets D-Link routers
- CVE-2014-9118: Targets Zhone routers
- NETGEAR DGN1000 exploit (No CVE assigned): Targets NETGEAR routers
Keep botnets out
To prevent Enemybot or any other botnet from infecting your devices and recruiting them to malicious DDoS botnets, always apply the latest available software and firmware updates for your product.
If your router becomes unresponsive, internet speeds drop, and is heating up more than usual, you may be dealing with a botnet malware infection.
In this case, perform a manual hard reset on the device, enter the management panel to change the admin password, and finally install the latest available updates directly from the vendor’s website.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now