
Ivanti has disclosed two Connect Secure (ICS) and Policy Secure (IPS) zero-days exploited by suspected Chinese hackers in the wild that can let remote attackers execute arbitrary commands on targeted gateways.
The first security flaw (CVE-2023-46805) is an authentication bypass in the appliances' web component, enabling attackers to access restricted resources by circumventing control checks, while the second (tracked as CVE-2024-21887) is a command injection vulnerability that lets authenticated admins execute arbitrary commands on vulnerable appliances by sending specially crafted requests.
When successfully chaining the two zero days, threat actors can run arbitrary commands on all supported versions of ICS VPN and IPS network access control (NAC) appliances.
"If CVE-2024-21887 is used in conjunction with CVE-2023-46805, exploitation does not require authentication and enables a threat actor to craft malicious requests and execute arbitrary commands on the system," Ivanti said.
"We are providing mitigation now while the patch is in development to prioritize the best interest of our customers. It is critical that you immediately take action to ensure you are fully protected."
The company says that patches will be available in a staggered schedule, with "the first version targeted to be available to customers the week of 22 January and the final version targeted to be available the week of 19 February."
Until patches are available, the zero-days can be mitigated by importing an XML file available to customers via Ivanti's download portal.
Zero-days likely exploited by Chinese hackers
Ivanti says the two zero-days have already been exploited in the wild in attacks targeting a small number of customers.
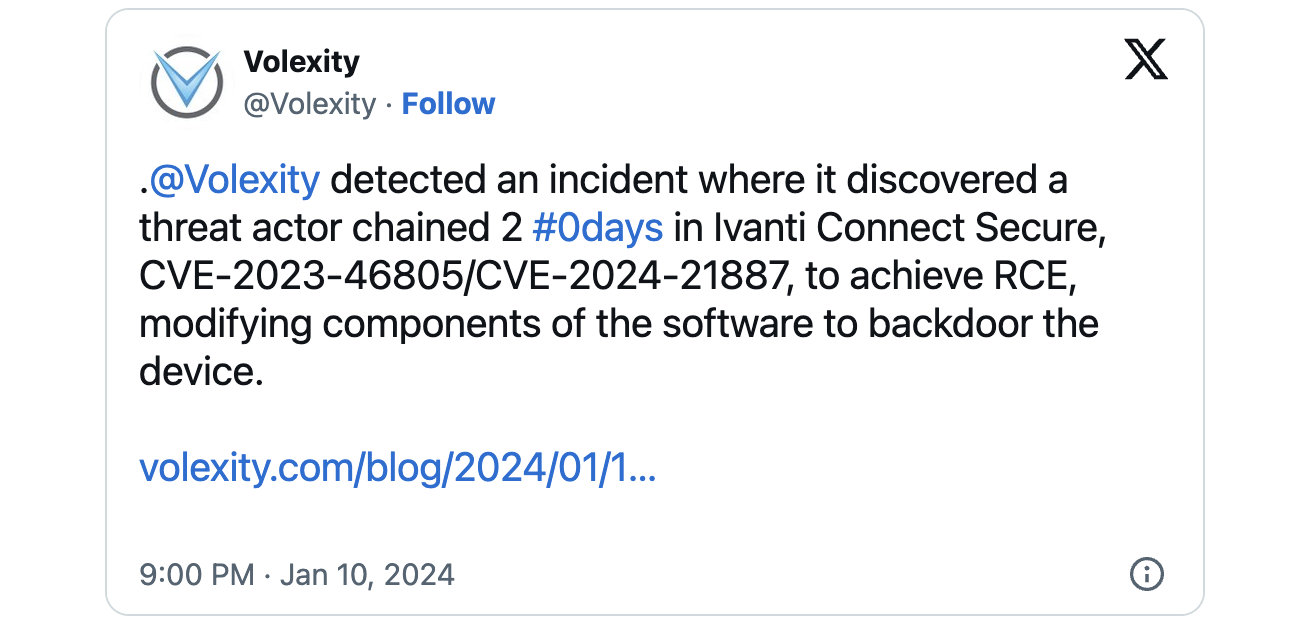
Threat intelligence company Volexity, which spotted the zero-days being exploited to breach a customer's network in December, believes the attacker is a Chinese state-backed threat actor.
Suspected Chinese threat groups used another Connect Secure zero-day tracked as CVE-2021-22893 in 2021 to breach dozens of U.S. and European government, defense, and financial organizations.
"We are aware of less than 10 customers impacted by the vulnerabilities. We are unable to discuss the specifics of our customers," Ivanti revealed.
"We have seen evidence of threat actors attempting to manipulate Ivanti's internal integrity checker (ICT). Out of an abundance of caution, we are recommending that all customers run the external ICT.
"Based on our analysis, Ivanti has not found any indication that this vulnerability was introduced into our code development process maliciously. Ivanti has no indication that it has been compromised."
As reported by Shodan, according to a search string shared by security expert Kevin Beaumont, over 15,000 Connect Secure and Policy Secure gateways are currently exposed online (security threat monitoring platform Shadowserver currently tracks more than 17,000 such appliances).
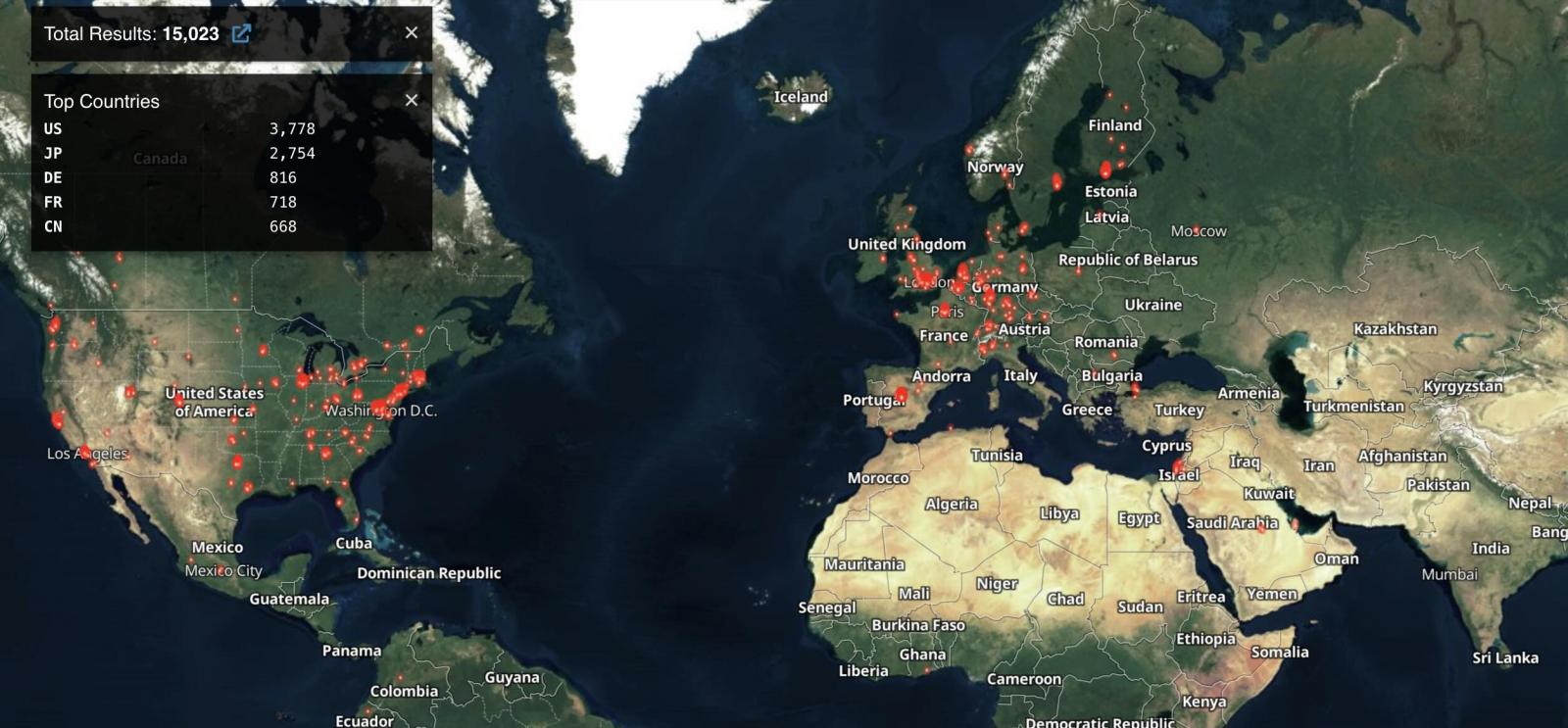
Beaumont also warned earlier today that the two zero-days are used in attacks and allow MFA bypass and code execution.
Last week, Ivanti said that a critical remote code execution (RCE) vulnerability (CVE-2023-39336) in its Endpoint Management software (EPM) could be abused by unauthenticated attackers to hijack enrolled devices or the core server.
In July, state hackers explored two other zero-days (CVE-2023-35078 and CVE-2023-35081) in Ivanti's Endpoint Manager Mobile (EPMM) to breach the networks of several Norwegian government organizations.
A month later, hackers exploited a third zero-day flaw (CVE-2023-38035) in Ivanti's Sentry software to bypass API authentication on vulnerable devices.
Ivanti's products are used by over 40,000 companies worldwide to manage their IT assets and systems.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now