
The Chinese hacking group known as 'Winnti' has been stealthily stealing intellectual property assets like patents, copyrights, trademarks, and other corporate data – all while remaining undetected by researchers and targets since 2019.
Winnti, also tracked as APT41, is an advanced and elusive cyber-espionage group that is believed to be backed by the Chinese state and operates on behalf of its national interests.
The discovered cybercrime campaign has been underway since at least 2019 and targeted technology and manufacturing firms in East Asia, Western Europe, and North America.
Operation CuckooBees
This criminal operation is known as 'Operation CuckooBees' and was discovered by analysts at Cybereason, who revealed new malware deployed by the notorious group of hackers, the mechanisms they leverage for intrusion, and the intricate payload delivery methods they use.
.png)
"With years to surreptitiously conduct reconnaissance and identify valuable data, it is estimated that the group managed to exfiltrate hundreds of gigabytes of information.
The attackers targeted intellectual property developed by the victims, including sensitive documents, blueprints, diagrams, formulas, and manufacturing-related proprietary data. - Cybereason.
The financial losses incurred by "CuckooBees" are hard to determine, but the figure should be on a scale that puts the operation among the most damaging cyber campaigns of the past years.
A stealthy operation
The infection chain observed in Operation CuckooBees begins with exploiting known and zero-day vulnerabilities in ERP platforms used by the targets.
Winnti establishes persistence via an encoded WebShell, by abusing the WinRM protocol for remote access, the IKEEXT and PrintNotify Windows services for DLL side-loading, or by loading a signed kernel rootkit.
Once they gain a foothold on networks, the hackers perform reconnaissance using built-in Windows commands like 'systeminfo', 'net start',' net user', and 'dir c:\', that are unlikely to trigger any alerts for suspicious activity, even when run in batch files via a Scheduled Task.
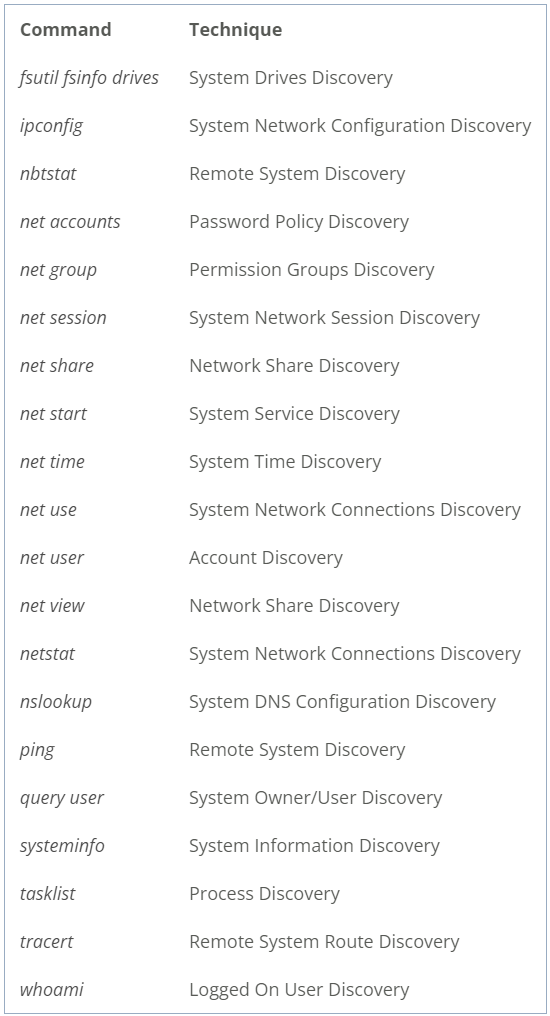
(Cybereason)
For credential dumping, Winnti uses either the 'reg save' command to save the stolen passwords in a safe place or a variant of a previously undocumented tool named 'MFSDLL.exe.'
For lateral movement, the hackers continue to abuse the Windows Scheduled Tasks along with a set of special batch files.

Finally, for the data collection and exfiltration, the threat actors deploy a portable command-line WinRAR app that features a valid digital signature and uses "rundll32.exe" for its executable.
.png)
New findings
What stands out in Cybereason's report is a new Winnti malware dubbed "DEPLOYLOG" and the method of abuse of the Windows CLFS (Common Log File System) mechanism for payload concealing.
CLFS is an internal logging system for Windows OSes, which uses a proprietary file format that's only accessible through the system's API functions. As such, its log files are skipped by AV scanners while human inspectors don't have a tool that can parse them.
Winnti abuses this system to store and hide its payloads that are dropped on the target system in CLFS log form and then extracted and executed via CLFS API calls.
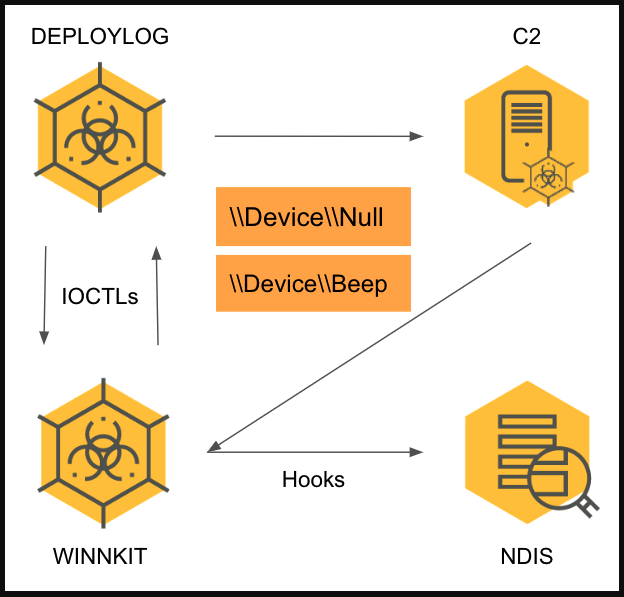
The DEPLOYLOG malware, which hasn't been documented before, is a 64-bit DLL (masqueraded as "dbghelp.dll") that extracts and executes Winnti's final payload, the WINNKIT rootkit, and then establishes two communication channels with the remote C2 and the kernel-level rootkit.
Some of the malware used to abuse Windows CLFS was previously discovered by Mandiant but had not been attributed to any threat actors.
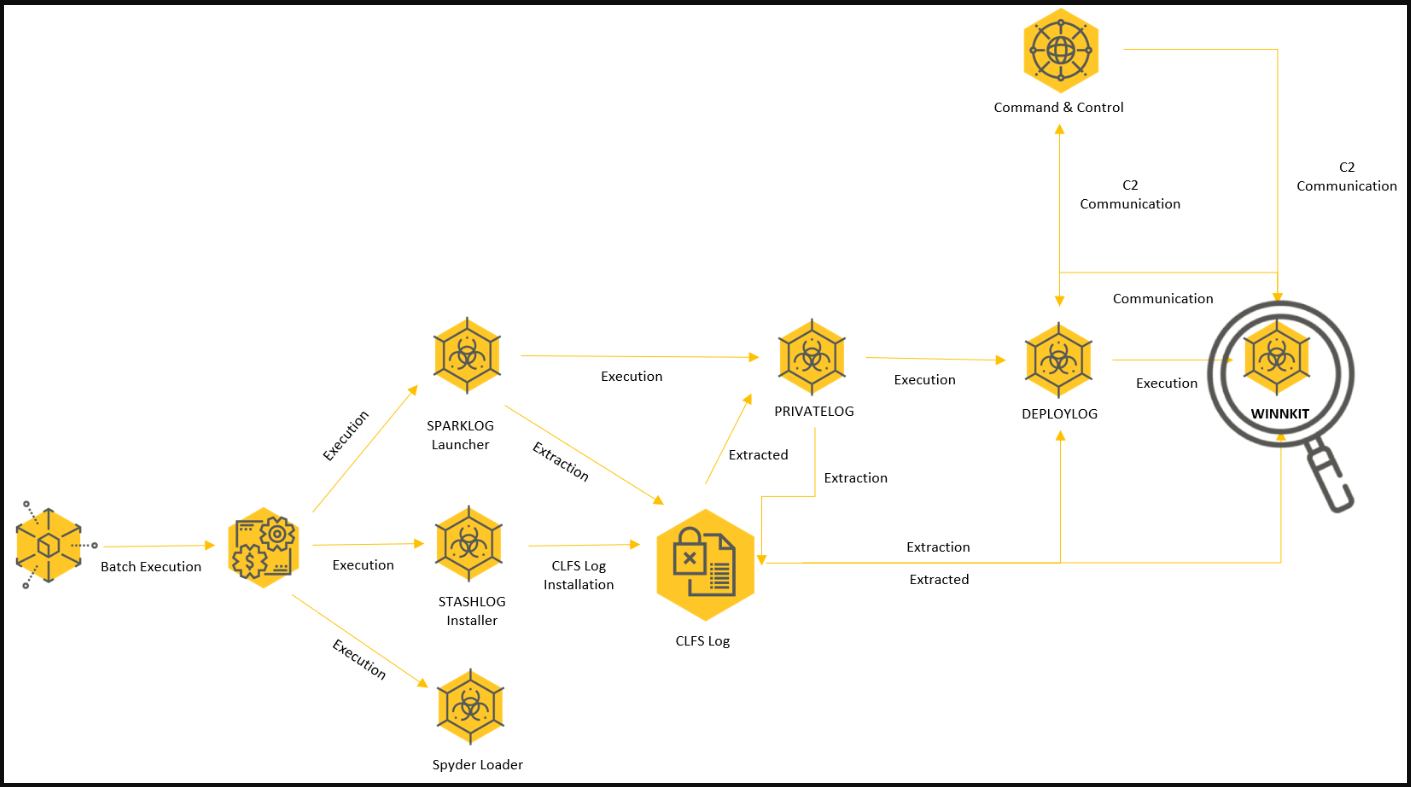
WINNKIT is the threat actor's most evasive and sophisticated payload, which has been extensively analyzed in the past. Still, even after all this time, it remains largely impervious to anti-virus detection.
In Operation CuckooBees, WINNKIT uses reflective loading injection to inject its malicious modules into legitimate svchost processes.
"WINNKIT contains an expired BenQ digital signature, which is leveraged to bypass the Driver Signature Enforcement (DSE) mechanism that requires drivers to be properly signed with digital signatures in order to be loaded successfully," explains the malware report by Cybereason.
"This mechanism was first introduced in Windows Vista 64-bit, and affects all versions of Windows since then."
After successful initialization, WINNKIT will hook the network communication and start receiving custom commands through DEPLOYLOG.
Defending your network
Despite indictments of Winnti members announced in the past couple of years by the U.S. Department of Justice, and no matter how many technical reports analyzing its tools and tactics have been published, the notorious Chinese cyber-espionage group remains active and industrious.
Cybereason believes that due to the complexity, stealth, and sophistication of Operation CuckooBees, it's very likely that Winnti compromised many more companies than those they were able to verify.
The best bet for defenders against such threats is to update all their software to the latest available version, monitor all network traffic, and use network segmentation.
For more details on Winnti's TTPs, check out an additional Cybereason blog piece that focuses on the techniques, or a third devoted to the malware used in the campaign.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now