
A hacking group tracked as 'Pink Drainer' is impersonating journalists in phishing attacks to compromise Discord and Twitter accounts for cryptocurrency-stealing attacks.
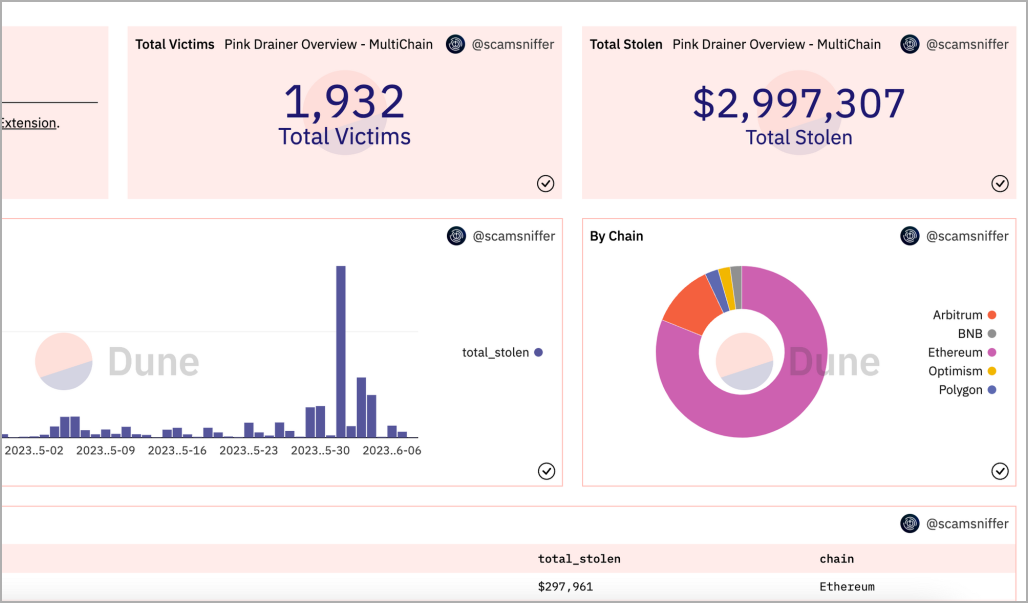
According to ScamSniffer analysts, Pink Drainer successfully compromised the accounts of 1,932 victims to steal roughly $2,997,307 worth of digital assets on the Mainnet and Arbitrum.
ScamSniffer's on-chain monitoring bots caught the threat actor when they snatched $327,000 worth of NFTs from a single person.
Some of the threat actor's recent targets are believed to include the CTO of OpenAI Mira Murati, Steve Aoki, Evmos, Pika Protocol, Orbiter Finance, LiFi, Flare Network, Cherry Network, and Starknet.
Impersonating journalists
Pink Drainer hijacks accounts through social engineering, where the threat actors spend a couple of days impersonating journalists from popular media outlets like Cointelegraph and Decrypt to conduct phony interviews with the victims.
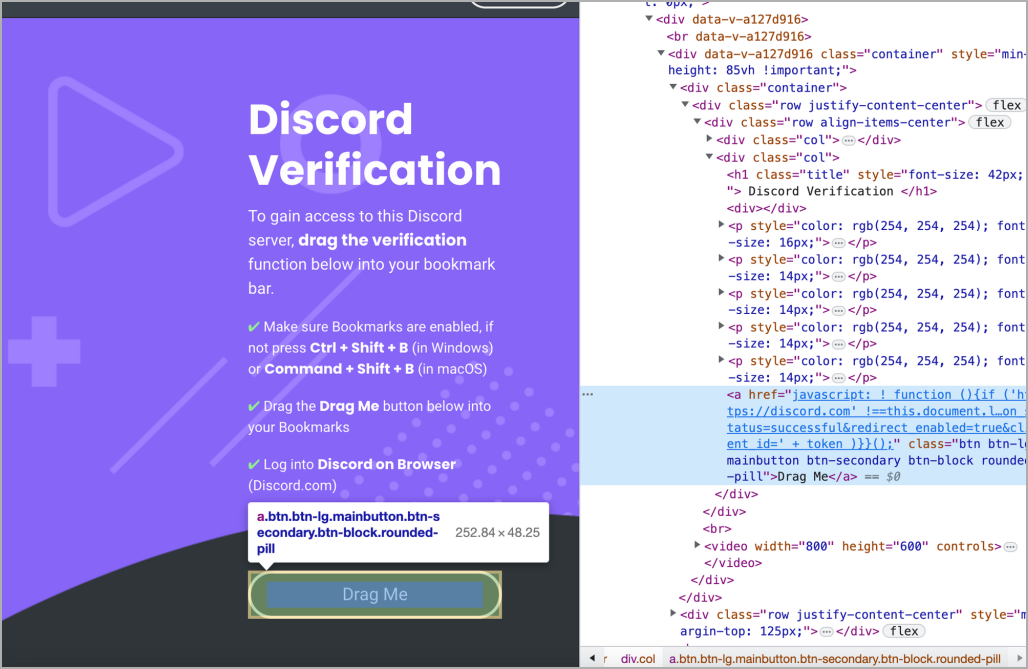
After gaining their victim's trust, the threat actors tell the targets they must conduct a KYC (know your customer) validation to prove their identity, guiding them to websites used to steal Discord authentication tokens.
These sites impersonate malicious bots like a Carl verification bot, where they are told to add bookmarks containing malicious JavaScript code using a "Drag Me" button on the malicious page.
This code steals Discord tokens, enabling the attackers to hijack the accounts without knowing the user credentials or having a way to intercept the two-factor authentication code.
To extend their control of the account, the attackers set themselves as administrators and removed all other administrators to steal digital assets and sensitive information undisturbed.
In cases where the account belongs to a renowned project or person with many followers, the attackers use their access to it to promote fake giveaways, fake mints, cryptocurrency scams, and phishing pages.
Unfortunately, Pink Drainer remains active, so high-profile digital asset holders must stay vigilant and treat media outlet communications with suspicion.
If a journalist approaches you, contact the media outlet via the details provided on their official website, and verify that the message originates from them.
Cryptocurrency investors should not automatically trust promotions posted by legitimate accounts. Instead, confirm the authenticity of giveaways and token drops by checking the platform's website and other social media channels.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now