
Threat actors use Google Ads tracking templates as a loophole to create convincing Webex software search ads that redirect users to websites that distribute the BatLoader malware.
Webex is a video conferencing and contact center suite that is part of Cisco's collaboration products portfolio and used by corporations and businesses worldwide.
Malwarebytes reports that the malvertising campaign has been active in Google Search for a week, with the threat actors appearing to be from Mexico.
Malicious Google Ad campaign
Malwarebytes reports that a malicious Google ad impersonates the official Webex download portal, ranking at the highest position in Google Search results for the "webex" term.
What makes the advertisement look legitimate is that it uses the real Webex logo and displays the legitimate URL, "webex.com," as the click destination. These ad components make the advertisement appear legitimate and indistinguishable from a real advertisement from Cisco.
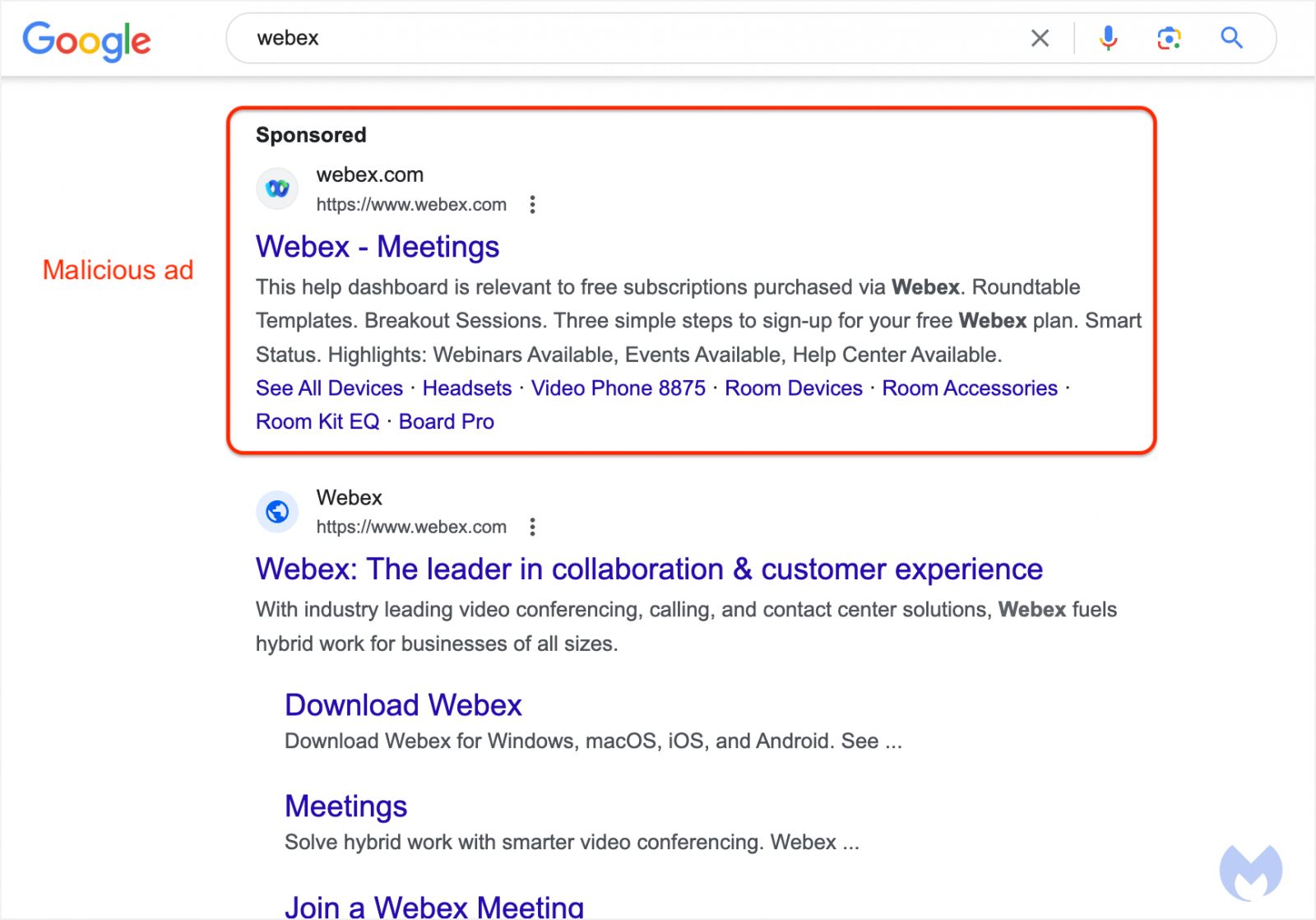
The threat actors can exploit a loophole in the Google Ad platform's tracking template that allows them to redirect at will while complying with Google's policy.
Specifically, Google says advertisers may use tracking templates with URL parameters that define a "final URL" construction process based on gathered user information regarding their device, location, and other metrics related to ad interactions.
The policy mandates that the display URL of an ad and the final URL must belong to the same domain. Still, nothing is stopping the tracking template from redirecting users to a website outside the indicated domain.
In this case, the threat actors used a Firebase URL ("trixwe.page.link") as their tracking template, with a final URL of https://www.webex.com.
However, if the ad is clicked, the visitor is redirected to the "trixwe.page[.]link," which filters out visits that appear to originate from researchers and automated crawlers.
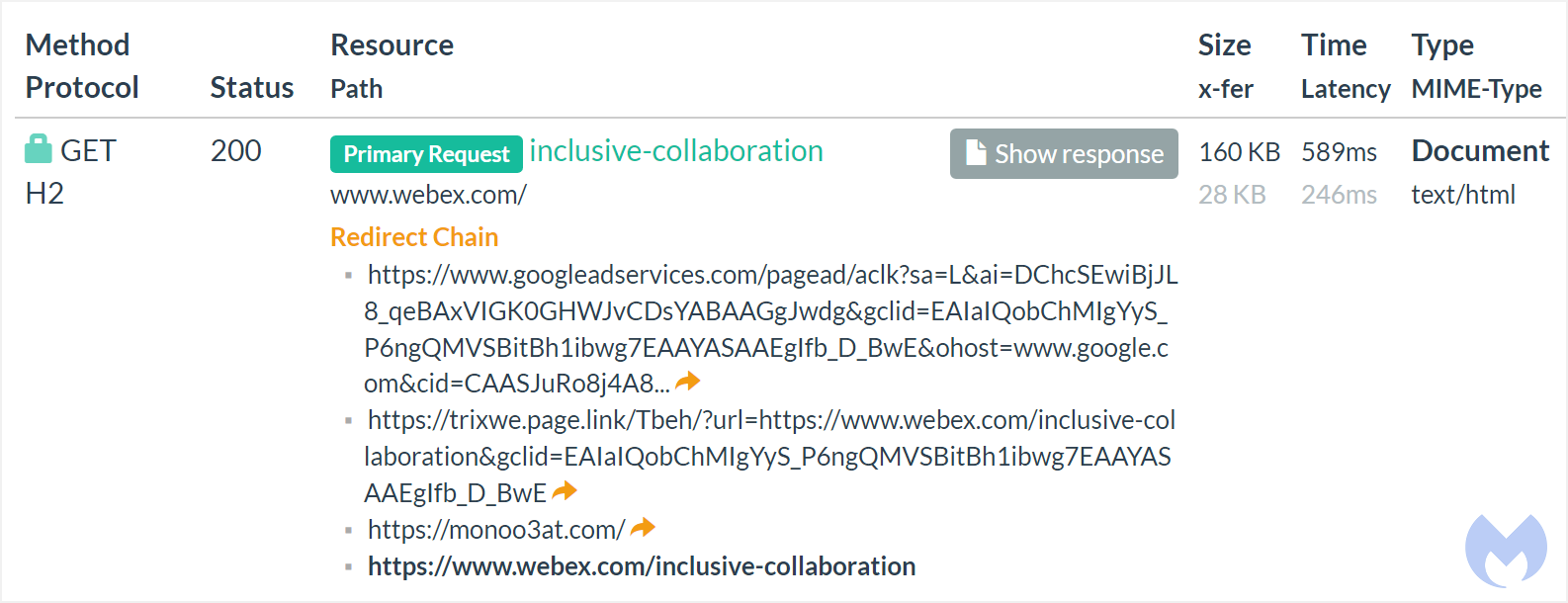
If the user is one they wish to target, it will redirect them to the site "monoo3at[.]com," where further checks are performed to determine if they are potential victims or researchers using a sandbox.
If the visitor is one the threat actors wish to target, they will be redirected to a malware-dropping site at "webexadvertisingoffer[.]com," while all others will be redirected to Cisco's legitimate "webex.com" site.
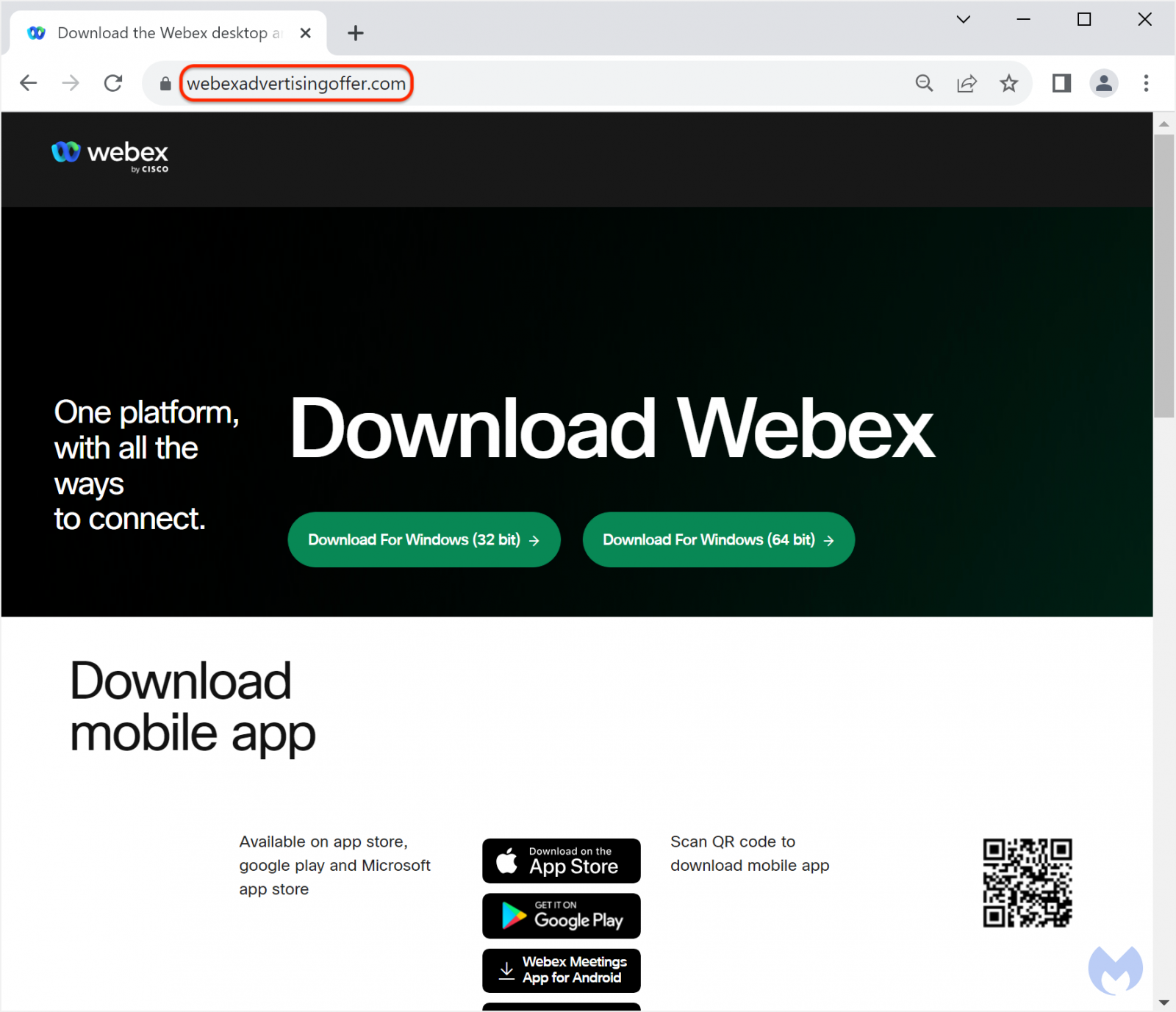
Fake Webex installer
If visitors of the fake Webex page click on the download buttons, they receive an MSI installer that spawns several processes and runs PowerShell commands to install the BatLoader malware.
This malware will ultimately fetch, decrypt, and execute an additional DanaBot malware payload.
DanaBot is a modular banking trojan that has circulated in the wild since 2018, with the ability to steal passwords, snap screenshots, load ransomware modules, mask malicious C2 traffic, and give direct access to compromised hosts via HVNC.
Those infected with DanaBot will have their credentials stolen and sent to the attackers, who will either use them for further attacks or sell them to other threat actors.
When looking to source software, it is a good practice to always skip promoted results on Google Search and only download directly from the software developer or a well-known, trusted site.
Update 9/15 - A Google spokesperson has sent BleepingComputer the following comment:
Protecting users is our top priority. We don’t allow advertisers on our platform to spread malicious software. We’ve reviewed the ads in question and have taken appropriate action against the associated accounts.


Comments
crowruin - 7 months ago
This is why it is important to use a reputable ad-blocker like Ublock Origin It completely removes these results from the google search
DO NOT use Adblockplus it allows these sponsored search results to appear
I read an article from here a few months ago where an NFTbro fell for a fake OBS download which infected him with the redline stealer
That could have been prevented if he had a good ad-blocker....
Mahhn - 7 months ago
Good old goog, enabling criminals so long as they get paid. Never Trust an Advertisement on Google. Never.