
Security researchers are seeing an uptick in the use of reverse tunnel services along with URL shorteners for large-scale phishing campaigns, making the malicious activity more difficult to stop.
This practice deviates from the more common method of registering domains with hosting providers, who are likely to respond to complaints and take down the phishing sites.
With reverse tunnels, threat actors can host the phishing pages locally on their own computers and route connections through the external service. Using a URL shortening service, they can generate new links as often as they want to bypass detection.
Many of the phishing links are refreshed in less than 24 hours, making tracking and taking down the domains a more challenging task.
Service abuse
Digital risk protection company CloudSEK observed an increase in the number of phishing campaigns that combine services for reverse tunneling and URL shortening.
In a report the company shared with BleepingComputer, researchers say they found more than 500 sites hosted and distributed this way.
The most widely abused reverse tunnel services that CloudSEK found in their research are Ngrok, LocalhostRun, and Cloudflare's Argo. They also saw Bit.ly, is.gd, and cutt.ly URL shortening services being more prevalent.
Reverse tunnel services shield the phishing site by handling all connections to the local server it is hosted on. This way, any incoming connection is resolved by the tunnel service and forwarded to the local machine.
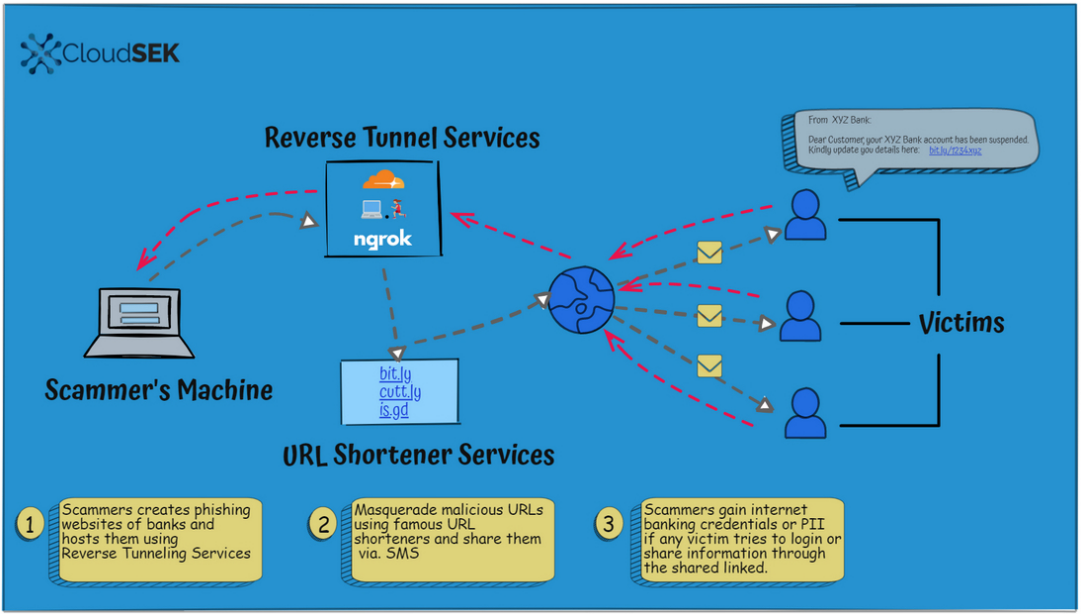
Victims interacting with these phishing sites end up with their sensitive data being stored directly on the attacker's computer.
By using URL shortners, the threat actor masks the name of the URL, which is typically a string of random characters, CloudSEK says. Thus, a domain name that would raise suspicions is hidden in a short URL.
According to CloudSEK, adversaries are distributing these links through popular communication channels like WhatsApp, Telegram, emails, text, or fake social media pages.
It is worth noting that misuse of these services isn’t new. For example, Cyble presented evidence of Ngrok abuse in February 2021. However, as per CloudSEK’s findings, the problem is getting worse.
Detected cases
One example of a phishing campaign abusing these services that CloudSEK detected was impersonating YONO, a digital banking platform offered by the State Bank of India.
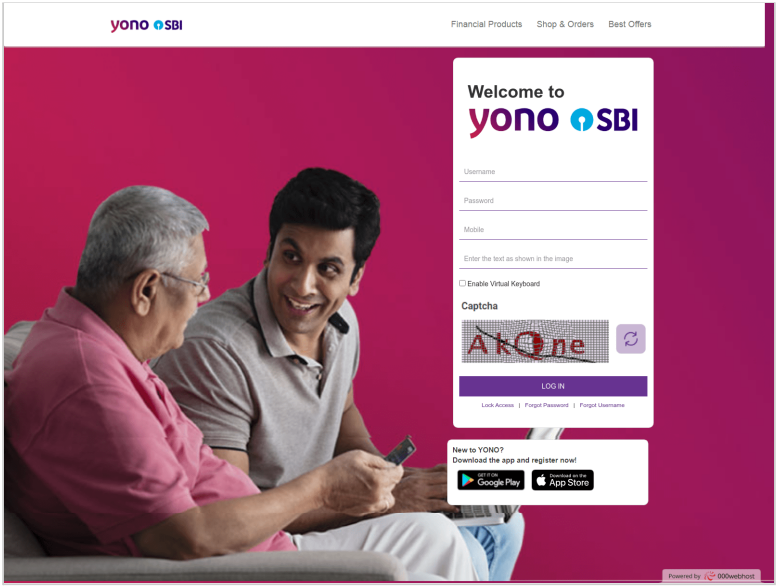
The URL defined by the attacker was hidden behind “cutt[.]ly/UdbpGhs” and led to the domain “ultimate-boy-bacterial-generates[.]trycloudflare[.]com/sbi” that used Cloudflare’s Argo tunneling service.
This phishing page requested bank account credentials, PAN card numbers, Aadhaar unique identification numbers, and mobile phone numbers.
CloudSEK did not share how effective this campaign was but highlights that threat actors are rarely using the same domain name for more than 24 hours, although they do recycle the phishing page templates.
"Even if a URL is reported or blocked, threat actors can easily host another page, using the same template" - CloudSEK
Sensitive information collected this way can be sold on the dark web or used by the attackers to empty banking accounts. If the data is from a company, the threat actor could use it to launch ransomware attacks, or business email compromise (BEC) fraud.
To protect against this type of threat, users should avoid clicking on links received from unknown or suspicious sources. Typing a bank's domain name in the browser manually is a good method to prevent being exposed to a fake website.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now