
Johnson Controls International has suffered what is described as a massive ransomware attack that encrypted many of the company devices, including VMware ESXi servers, impacting the company’s and its subsidiaries’ operations.
Johnson Controls is a multinational conglomerate that develops and manufactures industrial control systems, security equipment, air conditioners, and fire safety equipment.
The company employs 100,000 people through its corporate operations and subsidiaries, including York, Tyco, Luxaire, Coleman, Ruskin, Grinnel, and Simplex.
A weekend cyberattack
Yesterday, a source told BleepingComputer that Johnson Controls suffered a ransomware attack after initially being breached at its Asia offices.
BleepingComputer has since learned that the company suffered a cyberattack over the weekend that caused the company to shut down portions of its IT systems.
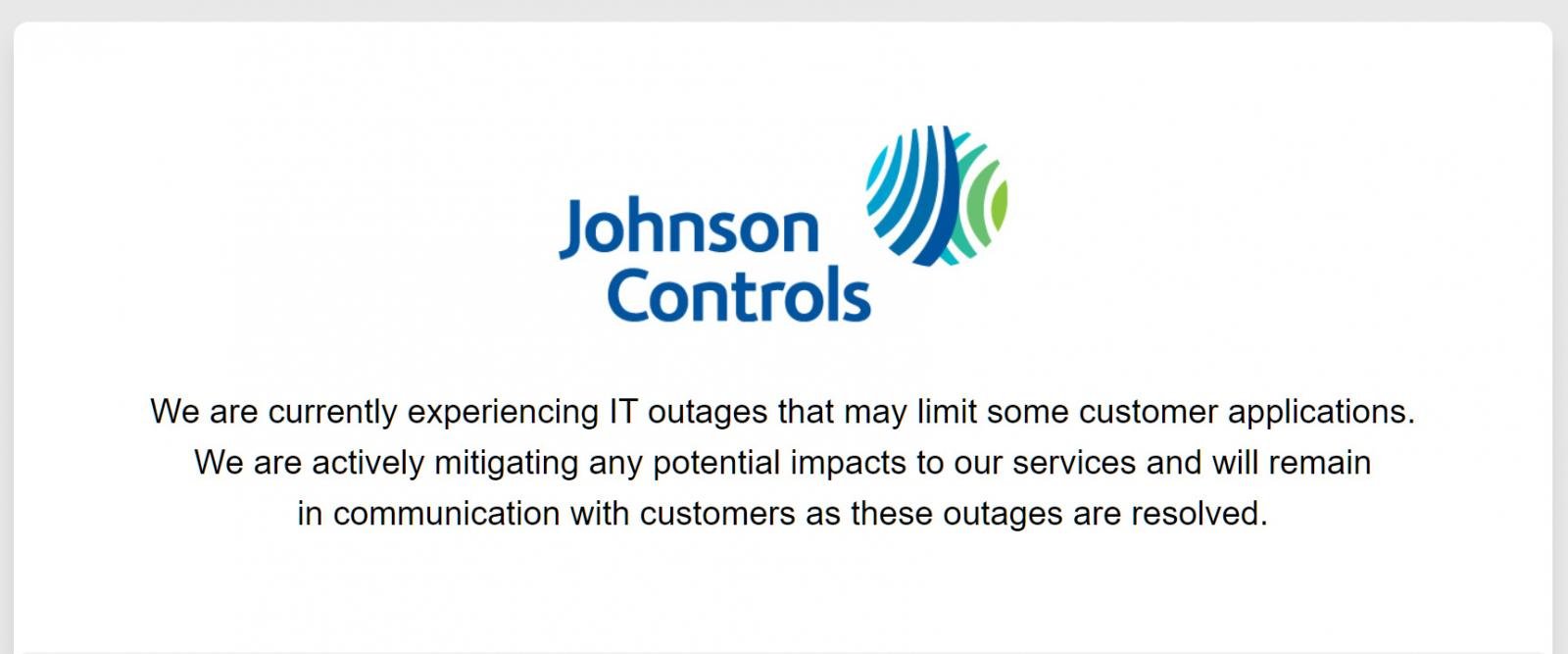
Since then, many of its subsidiaries, including York, Simplex, and Ruskin, have begun to display technical outage messages on website login pages and customer portals.
"We are currently experiencing IT outages that may limit some customer applications such as the Simplex Customer Portal," reads a message on the Simplex website.
"We are actively mitigating any potential impacts to our services and will remain in communication with customers as these outages are resolved."
Source: BleepingComputer
If you have any information on this attack or other attacks, you can contact us confidentially via Signal at 646-961-3731
Customers of York, another Johnson Controls subsidiary, report that they are being told the company’s systems are down, with some stating they were told it was due to a cyberattack.
"Their computer system crashed over the weekend. Manufacturing and everything is down," a York customer posted to Reddit.
"I talked to our rep and he said someone hacked them," posted another customer.
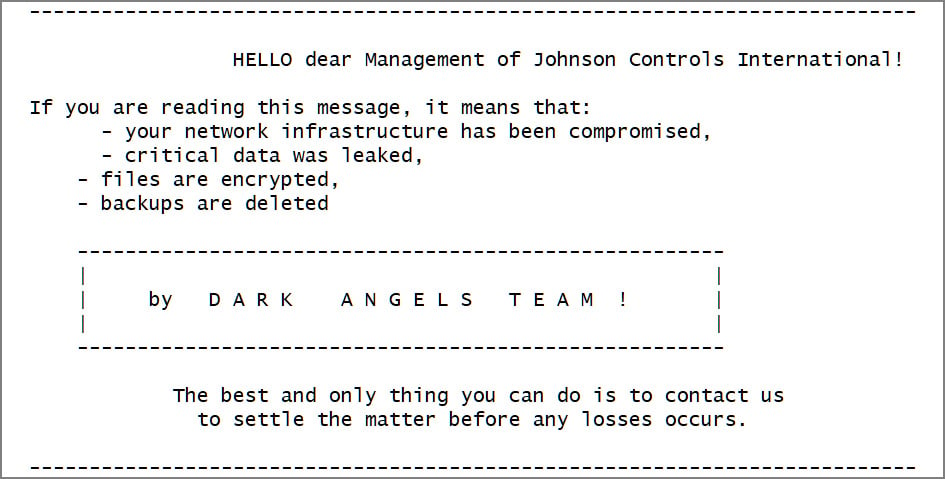
This morning, Nextron Systems threat researcher Gameel Ali tweeted a sample of a Dark Angels VMware ESXi encryptor containing a ransom note stating it was used against Johnson Controls.
Source: BleepingComputer
BleepingComputer has been told that the ransom note links to a negotiation chat where the ransomware gang demands $51 million to provide a decryptor and to delete stolen data.
The threat actors also claim to have stolen over 27 TB of corporate data and encrypted the company's VMWare ESXi virtual machines during the attack.
BleepingComputer has contacted Johnson Controls with questions regarding the attack but has not received a response.
After publication of our story, Johnson Controls confirmed the cybersecurity incident in a Form 8-K filing with the SEC, stating that they are working with external cybersecurity experts to investigate the incident and coordinating with insurers.
"Johnson Controls International plc (the “Company”) has experienced disruptions in portions of its internal information technology infrastructure and applications resulting from a cybersecurity incident. Promptly after detecting the issue, the Company began an investigation with assistance from leading external cybersecurity experts and is also coordinating with its insurers. The Company continues to assess what information was impacted and is executing its incident management and protection plan, including implementing remediation measures to mitigate the impact of the incident, and will continue taking additional steps as appropriate. To date, many of the Company’s applications are largely unaffected and remain operational. To the extent possible, and in line with its business continuity plans, the Company implemented workarounds for certain operations to mitigate disruptions and continue servicing its customers. However, the incident has caused, and is expected to continue to cause, disruption to parts of the Company’s business operations. The Company is assessing whether the incident will impact its ability to timely release its fourth quarter and full fiscal year results, as well as the impact to its financial results.
The Company’s investigation and remediation efforts are ongoing."
Who is the Dark Angels ransomware gang?
Dark Angels is a ransomware operation launched in May 2022 when it began targeting organizations worldwide.
Like almost all human-operated ransomware gangs, Dark Angels breaches corporate networks and then spreads laterally through the network. During this time, the threat actors steal data from file servers to be used in double-extortion attacks.
When they gain access to the Windows domain controller, the threat actors deploy the ransomware to encrypt all devices on the network.
The threat actors initially used Windows and VMware ESXi encryptors based on the source code leak for the Babuk ransomware.
However, cybersecurity researcher MalwareHunterTeam tells BleepingComputer that the Linux encryptor used in the Johnson Controls attack is the same as ones used by Ragnar Locker since 2021.
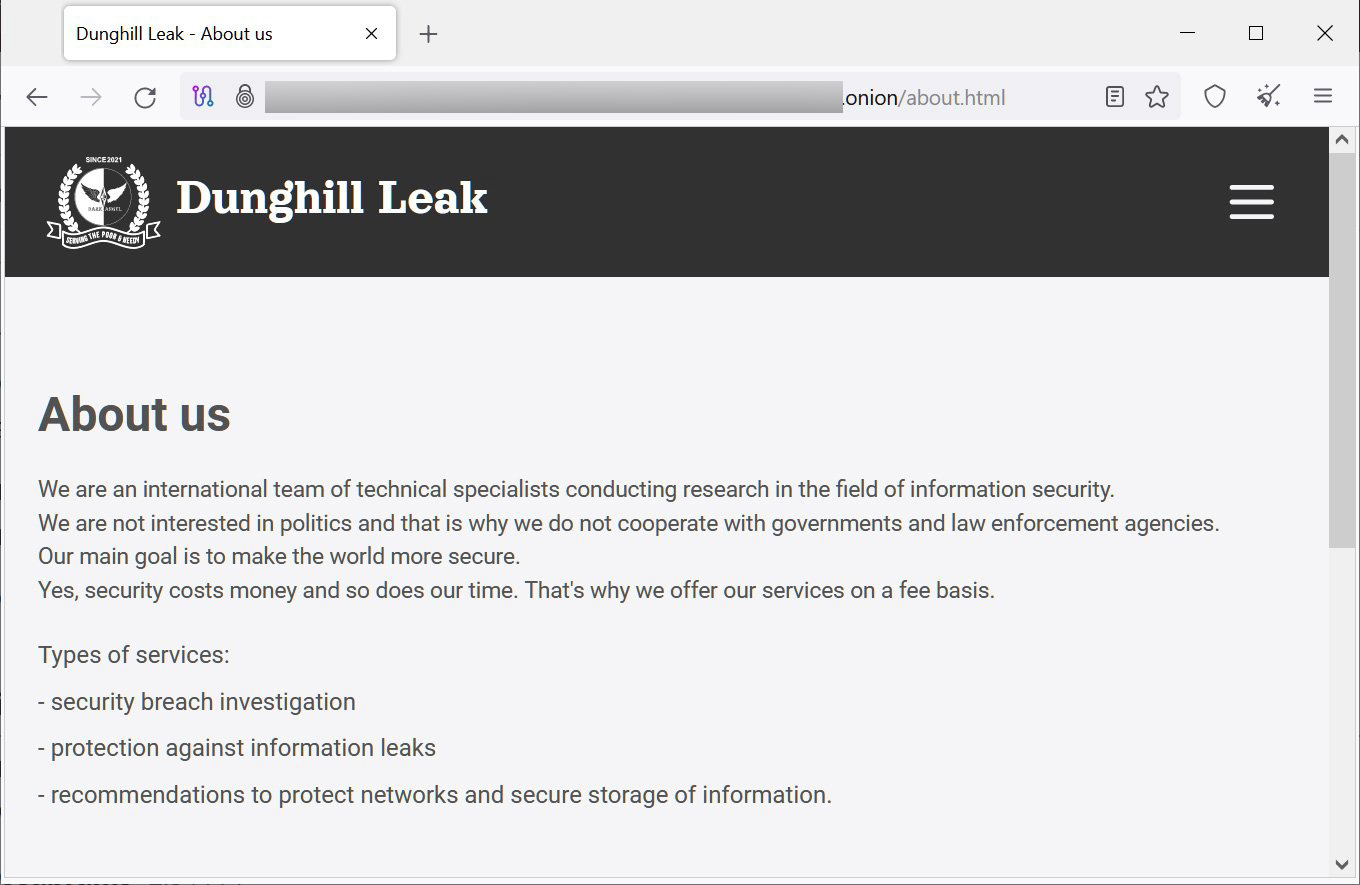
Dark Angels launched a data leak site in April 2023 called 'Dunghill Leaks' that is used to extort its victims, threatening to leak data if a ransom is not paid.
Source: BleepingComputer
This extortion site currently lists nine victims, including Sabre and Sysco, who recently disclosed cyberattacks.
Update 9/27/23: Added statement from Form 8-K filing.



Comments
mikebutash - 7 months ago
That is actually massive, they do mega state and federal building controls in airports, power plants, and all sorts of critical infrastructure places. I can only imagine the data they pilfered.