
For about half a year, work email accounts belonging to over 100 employees of the National Health System (NHS) in the U.K. were used in several phishing campaigns, some aiming to steal Microsoft logins.
Attackers started using legitimate NHS email accounts in October last year after hijacking them and continued to use them in phishing activity through at least April 2022.
NHS
More than a thousand phishing messages have been sent from NHS email accounts belonging to employees in England and Scotland, according to researchers from email security INKY.
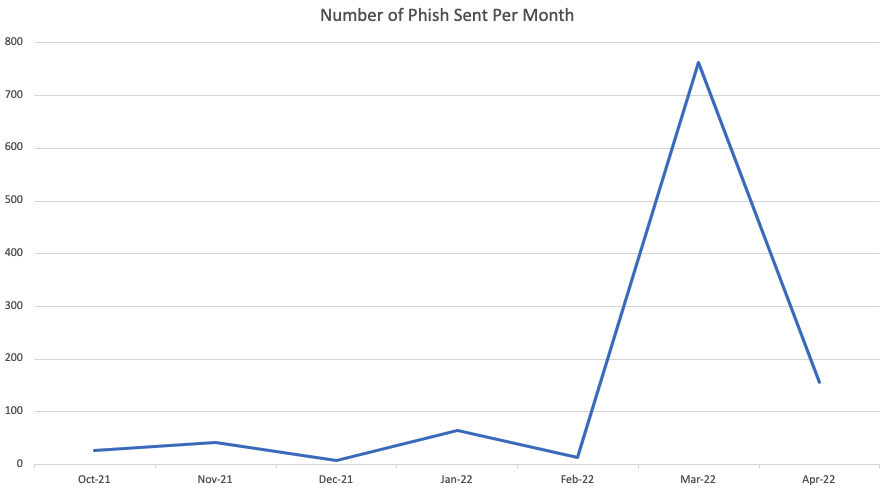
The researchers tracked the fraudulent messages as coming from two NHS IP addresses, delivered from email accounts of 139 NHS employees. INKY detected 1,157 fraudulent emails at its clients originating from the two addresses.
“The NHS confirmed that the two addresses were relays within the mail system [NHSMail] used for a large number of accounts,” INKY said in a report today.
In most cases, the phishing messages sent fake alerts for new document delivery that linked to fraudulent pages asking for Microsoft credentials.
To make the email more credible, the attackers added the NHS confidentiality disclaimer at the bottom of the message.
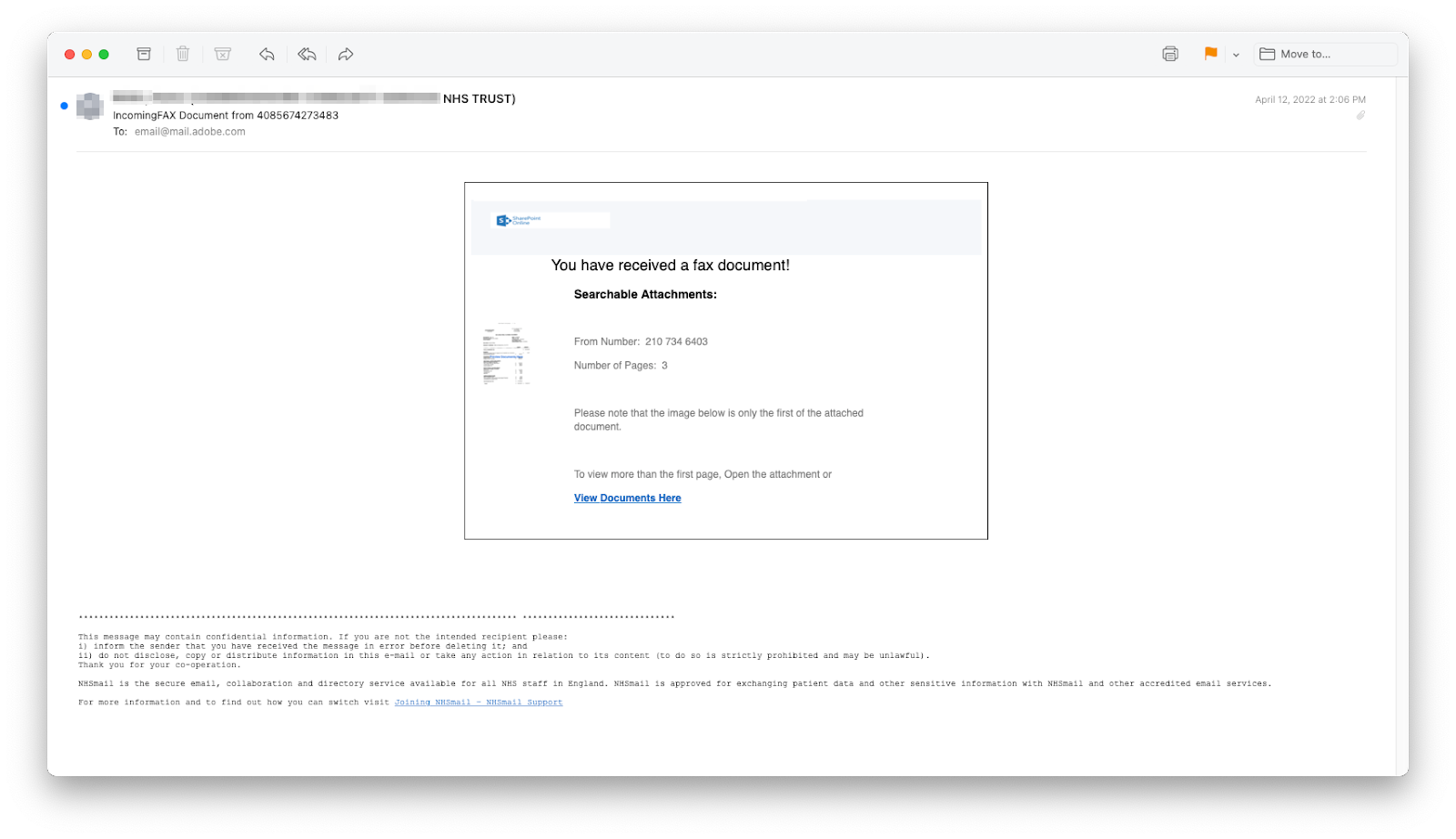
In other samples that INKY researchers collected, the phishing message impersonated brands like Adobe and Microsoft by adding the companies’ logos.
The campaigns appear to have been broad in scope and apart from attempting to steal credentials there have been a few advanced-fee instances where the attacker informed of a massive $2 million donation to the recipient.
Of course, receiving the funds came with a cost from the potential victim in the form of personal details (e.g. full name and address, mobile number).
Replying to the message returned an answer from someone using the name Shyann Huels and pretending to be “the special secretary to Mr. Jeff Bezos on International Affair Matters.”
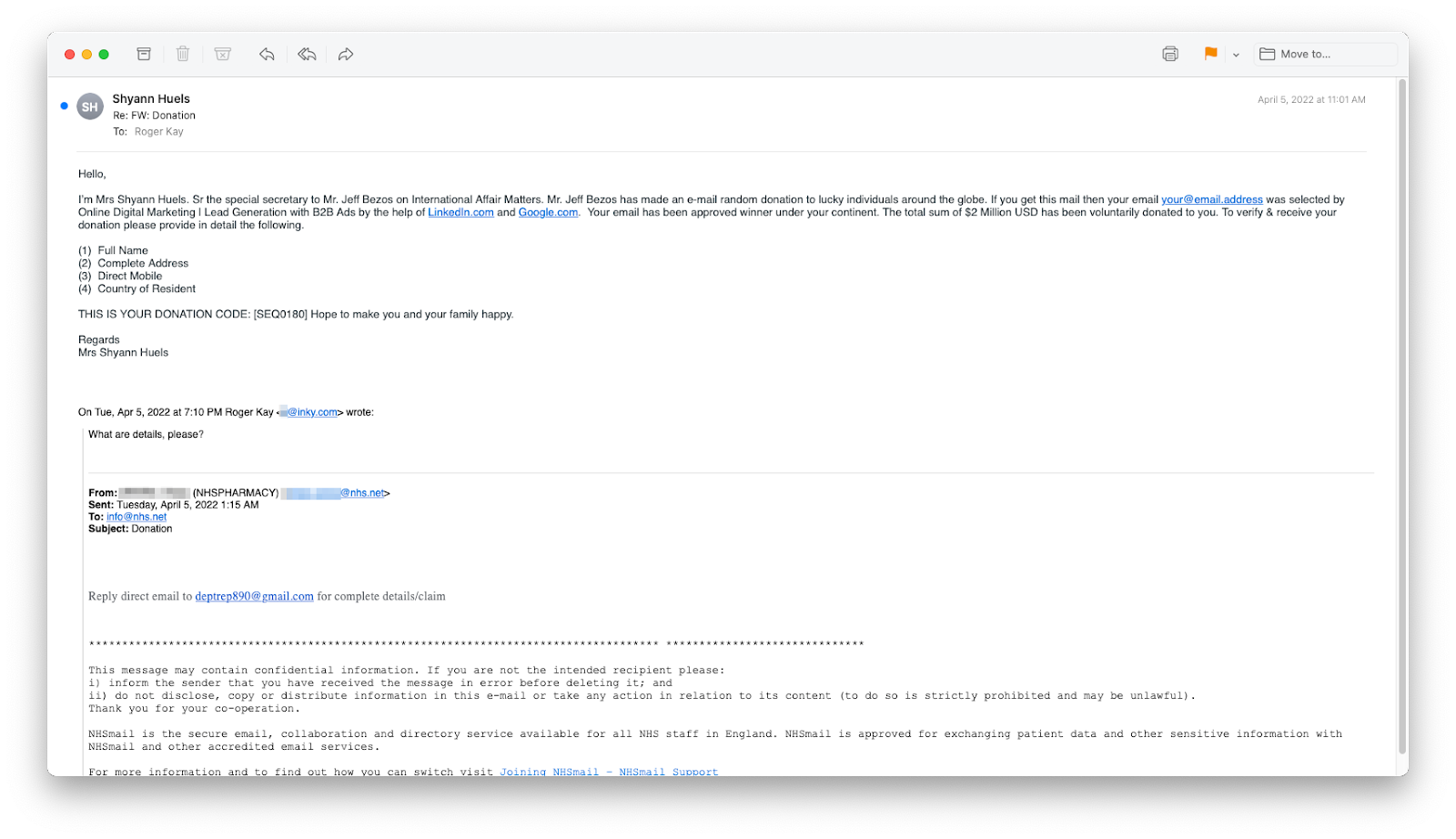
The same name and message in the image above have been seen in scams in early April and the individual behind the operation has a cryptocurrency wallet address that received about 4.5 bitcoins, currently worth around $171,000.
INKY has been in contact with NHS since they discovered the phishing campaign. The U.K. agency has addressed the risk after mid-April by switching from on-premise Microsoft Exchange deployments to the cloud service.
However, the move did completely stop the phishing as INKY customers continued to receive fraudulent messages, although in much smaller numbers.
This was due to NHS providing an infrastructure for tens of thousands of organizations (e.g. hospitals, clinics, suppliers, doctor’s offices) in the country that rely on various technical solutions.
Roger Kay, INKY's Vice President of Security Strategy, highlights that these campaigns are not the result of breaching NHS’ email server “but rather individually hijacked accounts.”


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now