Protect Your Home Network Devices from Joining the Botnet Army

An Internet Service Provider (ISP) recently reported to HKCERT that some home broadband routers in its network were suspected to be compromised to conduct distributed denial of service (DDoS) attacks. HKCERT is still investigating the cause of compromise of these routers.
These compromised routers generated a large volume of random sub-domain queries for some targeted domains, e.g. xxx.domain.com. Firstly, the resources of the target domains’ DNS servers were exhausted and cannot respond to other normal queries, resulting in a denial of service of the domains’ services. Furthermore, these routers also created huge amount of DNS queries to the upstream recursive DNS servers of the ISP they connect to. Subsequently the customers of the affected ISPs were not able to resolve host names and experienced a general denial of service attack to any domains.
Home networking nowadays might involve many different network devices, including the IP cameras, network TV box and network storage devices etc. which share a single Internet connection via the broadband router. The broadband router and network devices may be exposed to the Internet by nature of use (e.g. the broadband router need to be network accessible from the Internet) or by configuration flaws. Many users ignore to put up proper protection for these home network devices. Once attackers compromise the devices, they turn them into part of their botnet and use them as cyber weapons.
Home network device being used for cyber attacks
The security issues of home network devices attracted more concerns in recent years. In April 2014, Nominum (Ref. 1), a network security company, published a research report, claiming that more than 24 million home broadband routers worldwide were exposed to the Internet and were providing open DNS query service, of which 5.3 million devices were used in reflective denial of service attacks, capable of generating 10Gbps of cyber attack traffic.
Test if your network devices are exposed to the Internet
To check whether your network devices are exposed to the Internet, you can follow the steps below:
- Go to the following website. The site will automatically detect your current public IP address.
http://www.yougetsignal.com/tools/open-ports/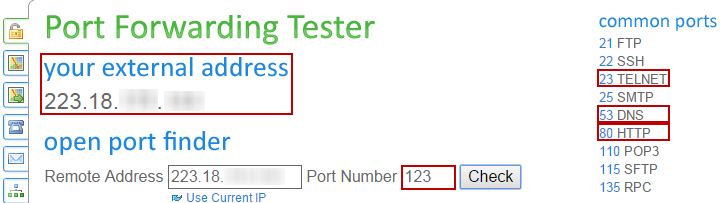
Figure 1: Screenshot of testing tool interface
- Enter the ports to test or select the common service ports on the right hand side and then press the “Check” button.
Note: it is recommended to test the following ports, including 23(Telnet), 53(DNS), 80(Http), 123(NTP) and 8080(Web Proxy). - The test results will show the ports that are “open” (i.e. exposed to the Internet).

or “closed” (i.e. not exposed)
Note: This tool should be used only for personal network inspection
If the test finds that any of the ports 23 (Telnet) or 53 (DNS) or 123 (NTP) etc. is open, any person on the Internet can access the services provided by your devices. These ports should not be turned on by default on the home network devices. If these services were not turned on by you, your network devices might have been compromised.
If you do not need to provide these network services to external users, you should disable them on the management interface of the devices, or resetting the device to factory settings. If you do not know how to change the settings of network devices, please consult user manual or contact the vendors or manufacturers of the devices to provide technical support.
Steps to protect the home network devices
In addition to the above test, you can refer to the following advice to protect the home network devices.
- Remote Management should be turned off to minimize the exposure to the Internet. Even if it is necessary to turn on remote management for you to access the device outside the home network, please consider changing the factory default port for remote management.
- Use a strong password and change the default administrator password. A password should be of at least 8 characters and composed of letters, numbers and symbols.
- Ensure your network device is installed with the most updated firmware from the manufacturer website.
- Install only software from trusted sources (e.g. the product support website) on to the network devices.
- Consult the manual or the product website about changing device settings or updating firmware. If you cannot find the information, please contact the devices vendor or manufacturer for information.
Reference:
1. http://nominum.com/news-post/24m-home-routers-expose-ddos/
Share with
