Beware of Encryption Ransomware, Do data protection now
What is "Encryption Ransomware"?
Encryption Ransomware attacks victims through phishing emails. Once infected, the malware encrypts not only the files located in the affected machines, but also the files shared on the connected network drive. The malware demands payment for a decryption key to recover the data.
Strengthen awareness, Stay alert for "Encryption Ransomware"
In Oct 2013, a well-known encryption ransomware CryptoLocker was discovered. According to the reports from a number of Hong Kong SMEs, their computers were infected and the files were encrypted. This seriously affected their regular operation in the companies. The encrypted files cannot be recovered if decryption key and backup are not available.
Due to the success of CryptoLocker operation model, the trend of encryption ransomware is growing. Recent active encryption ransomwares are listed below.
- Bitcrypt (Feb, 2014)
- CryptoDefense (Mar, 2014)
Recently, HKCERT has received several incident reports on CryptoDefense. We believe CryptoDefense has started its propagation in Hong Kong. Besides phishing email, the infection channel of CryptoDefense may come from various sources, including P2P file sharing, update fake flash player, setup fake online video player, etc.
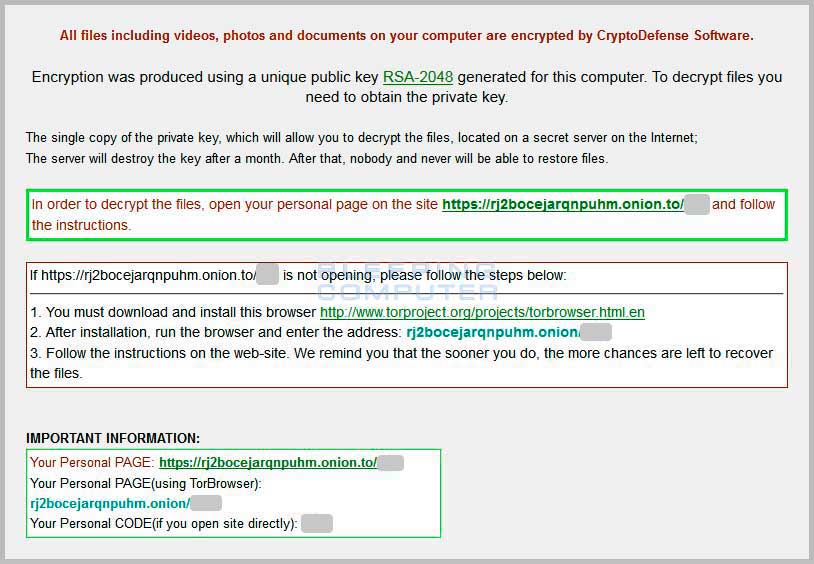
Fig) CryptoDefense screen shot
Recover the files encrypted by CryptoDefense
CryptoDefense is similar to CryptoLocker on encryption, but you may recover the files encrypted by CryptoDefense in the following situations.
- If you were infected before 1st April 2014, you may have a chance to decrypt the files. It is because the earlier version of CryptoDefense has a bug that mistakenly left the private decryption key behind on the computer. So, you can use Emsisoft Decryptor # to decrypt the encrypted files.
For details: http://www.bleepingcomputer.com/virus-removal/cryptodefense-ransomware-information#emsisoft
- If Shadow Volume Copy Service* is enabled in your computers, CryptoDefense attempts to clear your shadow copies (i.e. Previous Version in the folder Properties), and you cannot recover the files through native windows backup. However, you can use Shadow Explorer # to restore entries folders.
For details: http://www.bleepingcomputer.com/virus-removal/cryptodefense-ransomware-information#shadow
If you are not in either of the above two situations, your only alternative will be to restore from an available backup.
Suggestions from HKCERT
1.Beware of suspicious email. Do not open the attachment, especially compress files (.zip,.7zip) or executable files (.exe)
2.Install Security software and update to the latest signature. #
3.Backup important documents instantly and regularly. Keep the backups in a safe location to avoid being affected by malware.
For more information of data protection management, please refer to Data Protection Guideline.
# Before installation of the software, please visit the software manufacturer web-site for more details.
* Volume Shadow Copy Service: http://en.wikipedia.org/wiki/Shadow_Copy
Share with
