Abuse of Open Network Service in Distributed Reflection Denial of Service (DRDoS) Attack

(Image created by RRZEicons: http://commons.wikimedia.org/wiki/File:Temporarily-not-available-clock.svg)
Few months ago, there were reports about Network Time Protocol (NTP) servers widely abused in distributed reflection denial of service (DRDoS) attack. Abuse of open network services such as DNS and NTP to launch reflection attack is not new, in which attackers can make use of your infrastructure to attack their target. Securing our network infrastructure can minimize the chance of abuse by attackers.
Amplification - reason of attackers abusing our infrastructure
You may wonder why attackers want to use our infrastructure. As UDP protocol is connectionless, attackers can hide their actual location and need not fear being tracked when using our infrastructure. Besides, they need not use their own bandwidth in order to amplify the attack bandwidth. Here is how it works:
- Attacker, spoofed as coming from the victim's IP address, queries some open network services such as DNS, NTP.
- Due to the nature or flaw of the service, the response to the query might deliver larger size of data.
- For example, if querying the service consumes 0.5 KB data, the response to the query might be 40 KB, i.e. sending 0.5 KB data gets 40 KB data returned. Such scenario is called amplification. In this case, the amplification factor is 40 / 0.5 = 80X.
- Suppose the attacker has controlled 500 machines to submit that 0.5 KB query at the same time, the response would be 0.5 × 500 × 80 = 20,000 KB, i.e. around 20 MB.
- If the network service could not identify whether the source IP address is spoofed, it would return that 20 MB data to the victim.
DDoS attack using amplification via others' infrastructure is called distributed reflection denial of service (DRDoS) attack.
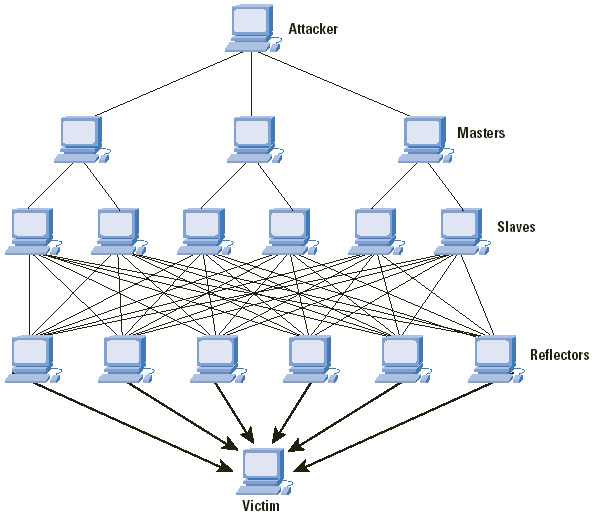
(Image source: Cisco)
Examples of DRDoS attack raising public concern
- DNS
The bandwidth generated by one of the most serious DRDoS attacks via DNS server was 65 Gbps1 (as a reference, the overall Internet traffic in Hong Kong through HKIX is around 150 Gbps on average in Nov 20132). These servers were abused because they were configured as "open resolver", which implied that anyone can query them on the Internet. Due to the misconfiguration (actually many of such servers need not be open to public), they became "valuable" resources to the attackers.
- NTP
In Nov 2013, there were widely active DRDoS attacks via NTP3. NTP has a command MONLIST (or MON_GETLIST), which returns a list of recent servers querying that NTP server. The amplification factor ranges from 19X to 206X, i.e. if the attack could gather 100 machines with querying traffic 1 MB each, it can launch 100 × 206 ≈ 20 GB DRDoS attack. HKCERT has received reports that thousands of NTP servers in Hong Kong are open to public. Regarding the reports and the attack in Nov 2013, HKCERT has issued a security bulletin SA14020701.
- SNMP
SNMP is an application layer protocol used for managing devices on various network layers such as router, switch, printer etc. Devices being monitored under SNMP will respond to requests from management software via UDP port. Attackers can abuseGetBulkRequestcommand in SNMP to query several devices in order to conduct reflection attack4.
- CHARGEN
CHARGEN is a debugging and measurement tool and a character generator service. It can make use of UDP port for traffic4. Attack via CHARGEN was first addressed in 19965.
General Advice on securing network services
- If the services are supposed only for use within internal network, disallow access from outside (e.g. placed behind a firewall and filtering incoming traffic).
- Disable unused services.
- Perform ingress filtering on your firewall - prevent any infected machine from controlling by bot software to perform malicious activity.
- To verify whether your DNS server can be abused for DRDoS, visit this website: http://openresolverproject.org/; for NTP server, please refer to HKCERT Security Bulletin SA14020701; for any protocol, you can verify it by using vulnerability scanner.
References
- How to Launch a 65Gbps DDoS, and How to Stop One, CloudFlare
- Using Joomla? Your website might have already taken part in DDoS attack, HKCERT
- NTP Reflections, RIPE
- [PDF] An Analysis of DrDoS SNMP/NTP/CHARGEN Reflection Attacks, Prolexic
- UDP Port Denial-of-Service Attack, CERT
- UDP-based Amplification Attacks, US-CERT
- [Image] The Rise of DRDoS Atacks, Prolexic
Share with
