Impacts and Response to Heartbleed Vulnerability
Content
Introduction
Impacts
How to respond to Heartbleed Vulnerability
Introduction
On 8th April 2014, there were numerous reports about OpenSSL Heartbleed vulnerability on information security websites globally. HKCERT published a security bulletin about the vulnerability here.
Impacts
Heartbleed vulnerability has been identified in the TLS heartbeat extension of OpenSSL. The impacts of this vulnerability are enormous because OpenSSL is the most popular open source library used to encrypt and secure data connection. Some popular websites, such as Facebook, Instagram, Pinterest, Tumblr, Twitter, Google, Yahoo, Gmail, Yahoo Mail, GoDaddy, Dropbox, Minecraft that were vulnerable to this vulnerability have been patched to minimize the impact to their users. Furthermore, system and service such as SSL VPN, POP3 /IMAP /SMTP email service with SSL encryption and some mobile applications are also vulnerable.
Heartbleed vulnerability can be exploited to retrieve sensitive information from the memory by sending specially crafted packets to the vulnerable server. It can expose sensitive information including user name and password, and the private key of server certificate.
How to respond to the Heartbleed vulnerability?
System Administrator
Utilize the Heartbleed vulnerability checking tools, and the Affected Vendor information list to check whether the system is being affected.
If the system is affected by Heartbleed vulnerability:
- Apply latest patches
- Revoke and reissue a new certificate from CA with new private key
- Update the new certificate of all the affected server
- Notify or enforce user to change password
- Stay tuned for the latest news about this vulnerability
General Users
1. Change Password
As heartbleed vulnerability has existed for two years, hackers may have exploited this vulnerability since then. HKCERT advises users to change password on all web service to ensure the accounts are safe.
- Users shall use Heartbleed checking tools to ensure all web services not being affected by this vulnerability before changing password, otherwise the risk of sensitive information being exposed still exists.
- If the web services currently in use are being affected by Heartbleed vulnerability
- Notify the website administrator immediately. Stop using the web services, and remove all personal information on the website
- After confirming the vulnerability has been patched, login to the web service and change password
2. Beware of Phishing
User shall be caution of phishing campaign related to the widely known Heartbleed vulnerability.
- When receiving email notification of changing password, do not click on the link provided in the email. Go to the official website of the service, check and make sure the website is not affected or the vulnerability has been fixed before login and change password.
3. Keep System Updated
Third party applications (eg Google Drive, DropBox, iTune etc) may be affected by Heartbleed vulnerability.
- Users shall verify if the third party applications are being affected by this vulnerability. Update application to the latest and apply patches for the third party applications.
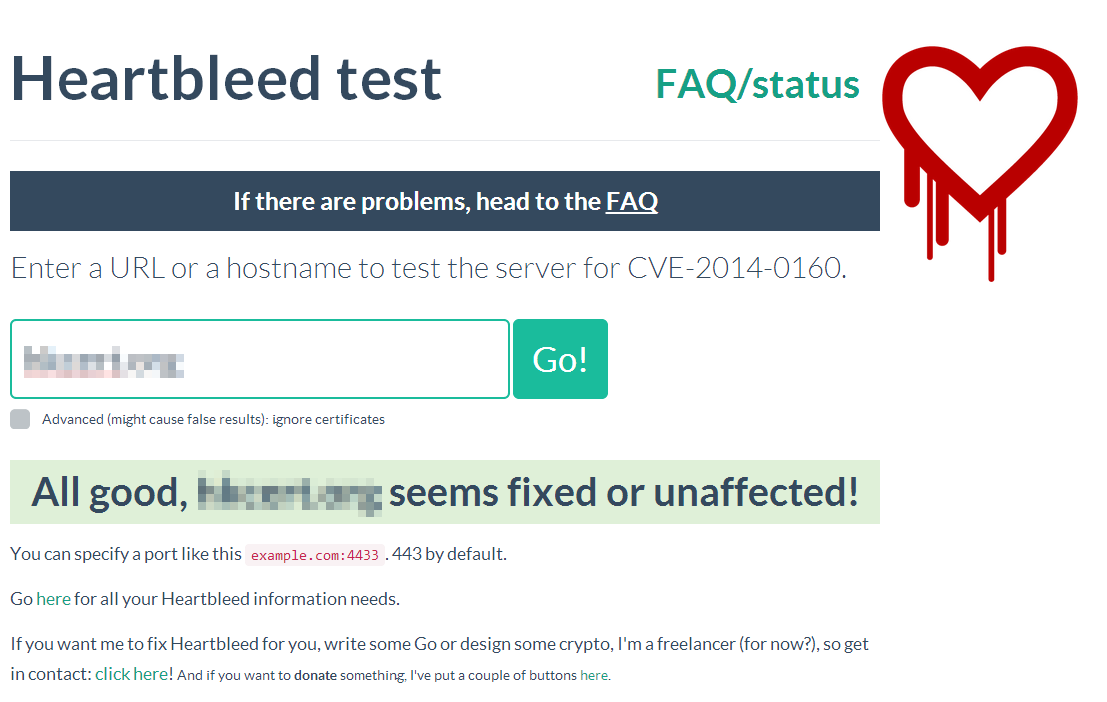
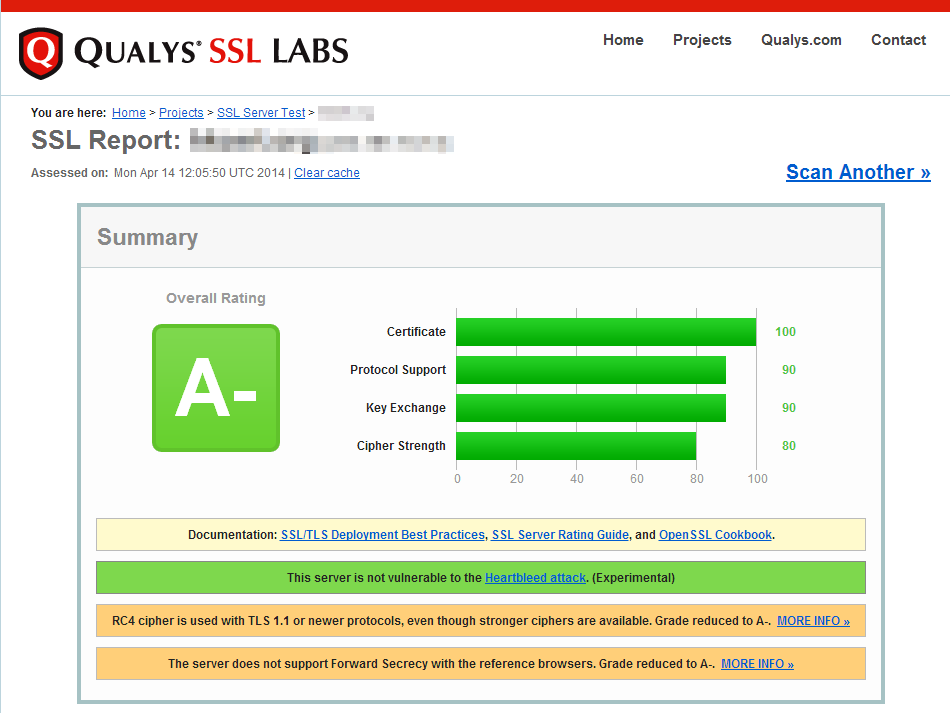
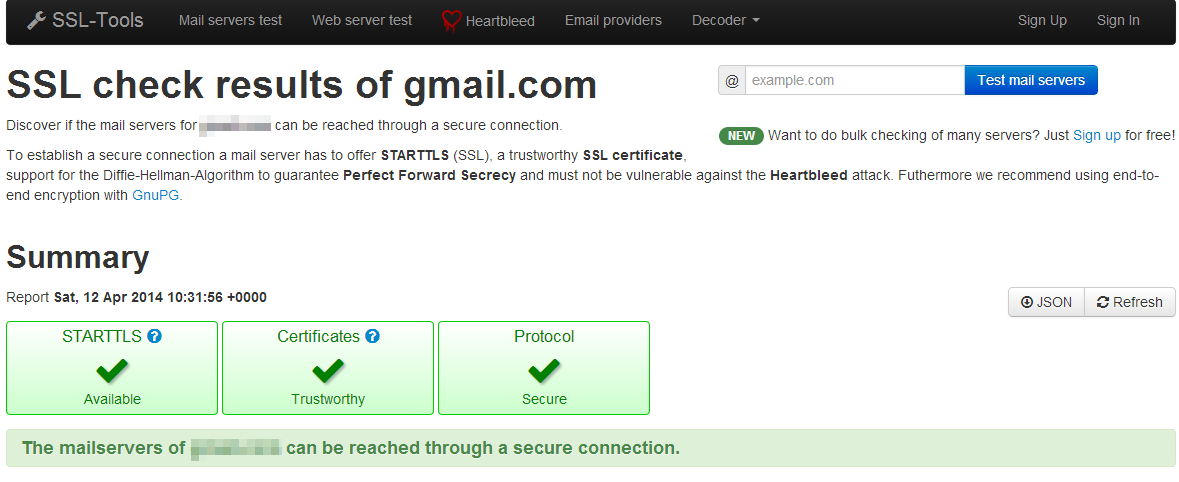
Heartbleed vulnerability checking tools
Some websites provide online checking tool for Heartbleed vulnerability. User simply enters a URLs of the website or the host name of the email server and the tool will tell you whether it is vulnerable.
Website checking tools
Email
Email Checking Tool
Chrome plug-in
This plug in will show the Heartbleed vulnerability status of the website visiting currently.
Additional information:
Share with